- Feb 4, 2016
- 2,520
Since June this year, a group of cyber-criminals has been breaking into unsecured enterprise servers via RDP brute-force attacks and manually installing a new type of ransomware called LockCrypt.
A constant stream of victims have been asking for help with LockCrypt infections on a Bleeping Computer ransomware support forum.
According to experts at AlienVault — who looked deeper into some infections — attackers hit companies in countries such as the US, the UK, South Africa, India, and the Philippines.
LockCrypt gang operating via RDP brute-force attacks
The LockCrypt gang usually breaks into one server, moves laterally to as many machines as possible, and manually runs the LockCrypt ransomware on each system.
Each computer hit by LockCrypt shows a visual and ransom note like the one below, and files are encrypted and feature a new .lock extension.
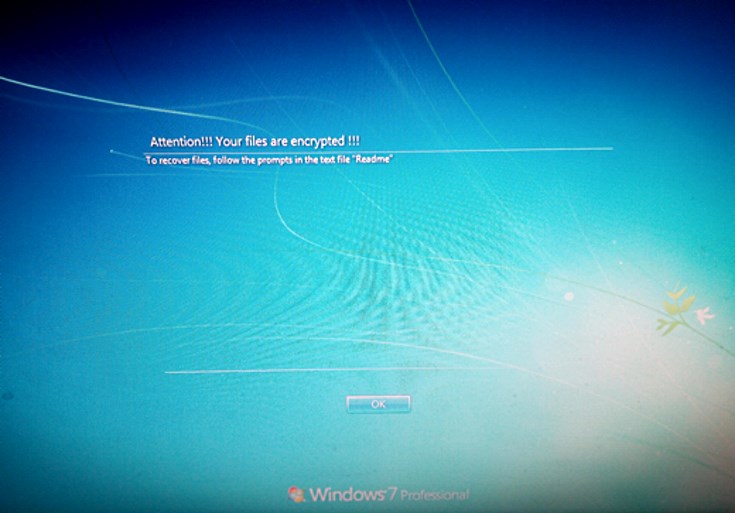
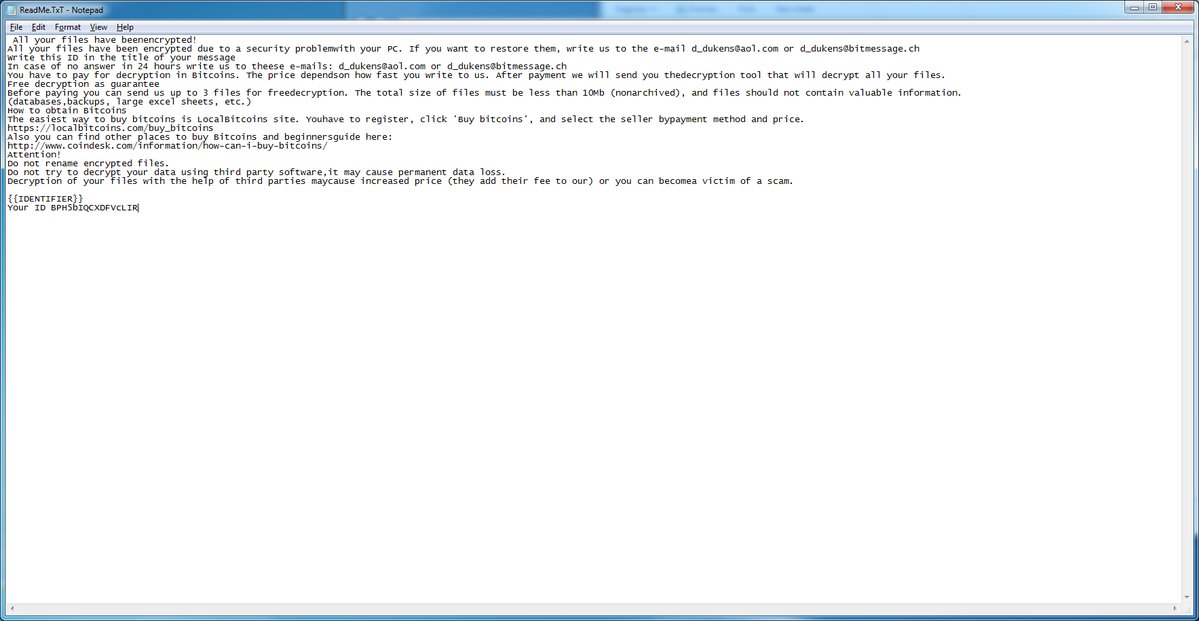
To decrypt locked data, victims must pay ransoms that usually vary between 0.5 and 1 Bitcoin per server, or between $3,500 and $7,000 per machine.
Some companies may face ransom demands of hundreds of thousands of dollars, if attackers manage to compromise a larger number of systems.
LockCrypt gang started on the Satan RaaS
According to the AlienVault team who were called in to investigate some incidents, first versions of the LockCrypt ransomware featured an email address that was previously associated with ransomware strains generated via the Satan RaaS (Ransomware-as-a-Service) portal, launched in January this year.
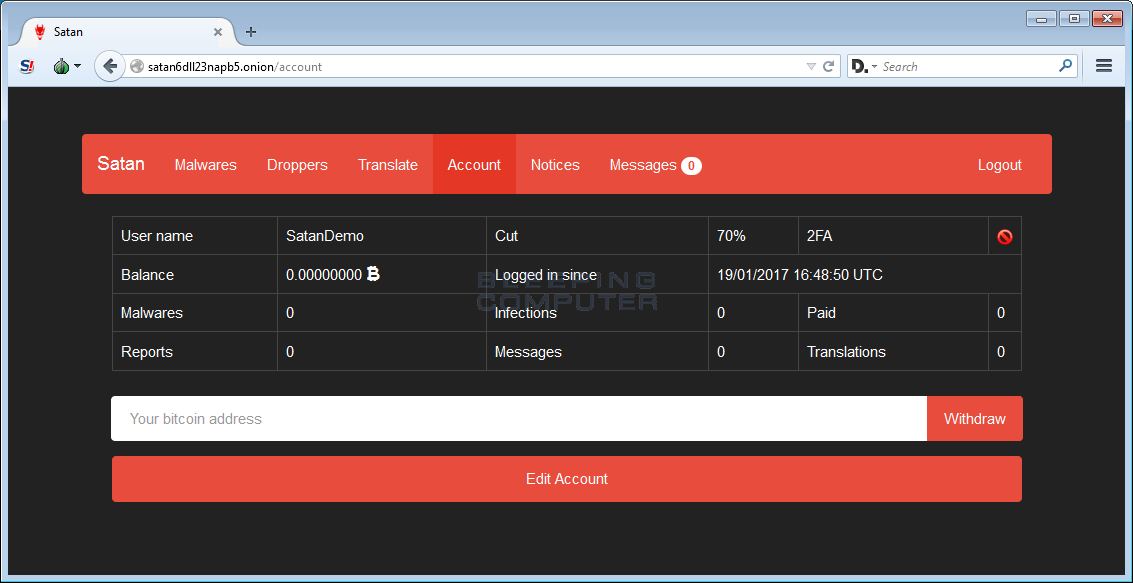
Experts believe the group might have used a Satan ransomware strain in the beginning and used the profits to code a custom version afterward, which eventually became the LockCrypt ransomware.
LockCrypt is also not your run-of-the-mill strain. The ransomware uses strong encryption, gets boot persistence, deletes shadow volume copies, and runs a batch file that kills all non-Windows core processes, as a way to make sure it stops antivirus solutions or any other process that may affect the subsequent file encryption process.
LockCrypt is just the latest addition to a long list of ransomware families that cyber-criminals don't spread via spam or exploit kits, but rely on RDP brute-force attacks.
Previous ransomware families installed the same way include SynAck, Bit Paymer, RSAUtil, Xpan, Crysis, Samas (SamSam), LowLevel, DMA Locker, Apocalypse, Smrss32, Bucbi, Aura/BandarChor, ACCDFISA, and Globe.
AlienVault and users who reported LockCrypt infections on the Bleeping Computer forum said that attackers usually logged into their network via RDP from 212.111.192.203, an IP address associated with the Ministry of Education and Science of Ukraine.
The LockCrypt gang appears to be making quite the profit from their criminal endeavors. Just three of the many Bitcoin wallet addresses [1, 2, 3] used in ransom notes reveal the group made around $175,000 worth of Bitcoin.
