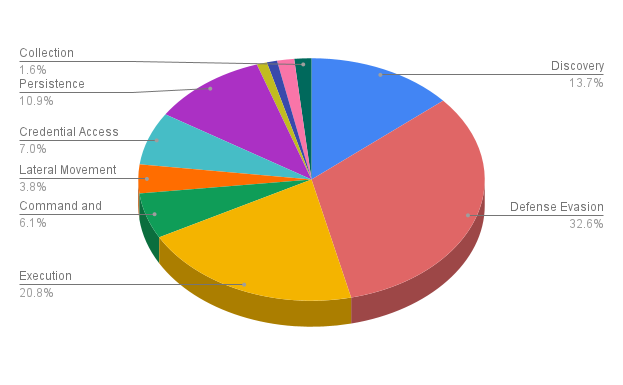
Not sure how you arrived at this position. Please explain. All evidence (anecdotal) suggests that LOLBin abuse is about the same. The techniques are the same. New TTPs are added slowly, but there is a small, net increase over time. The scale of campaigns are both increasing and decreasing. Which direction depends upon a lot of variables.
What is ever-increasing is attack surface generally. With all the additions of new platforms, and the software needed for those platforms, it is not difficult to see that one of the fundamental security challenges has been, and always shall be attack surface.
For some discussions, it would be helpful
@ticklemefeet if you ping me in a DM.
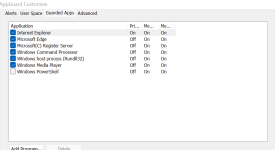
You mean processes that have not yet been added to one of the lists? Those do make it to lists quick enough so as not to negatively impact security in any meaningful way. At least internally, new LOLBins hit the print quickly. I get that it might take a project such as LOLBin to add a process to its maintained list.
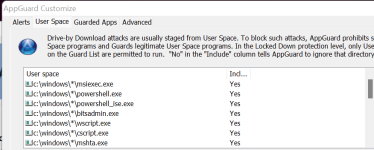
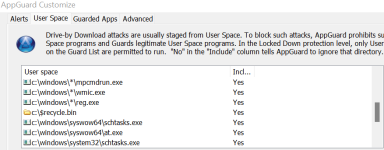
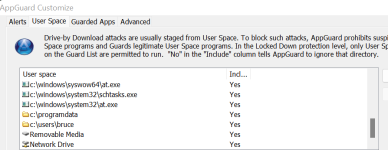
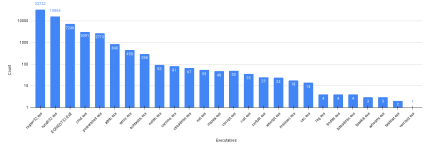
Blocking just the Uptycs list will thwart most threats regardless of the vector. It is difficult to give numbers but the likelihood that an attack will succeed on a hardened Windows image is low - a small number that only matters to statisticians and mathematicians.