- Jul 27, 2015
- 5,458
Talos recently observed a malware distribution campaign that tries to trick users into executing fake software installers of popular software on their systems. We believe with moderate confidence that online advertising is used to reach potential victims that are searching for software to install on their systems. The combination of advertising and fake software installers is particularly tricky, as the users reached by the ads are already predisposed to execute an installer on their systems. Once the fake installers run, they execute three pieces of malware on the victim's system:
Password stealers have long presented a risk to individuals and to companies. The compromised accounts are frequently sold in underground forums and may lead to additional compromise using the stolen accounts and through password reuse. The chrome extension adds to this risk by allowing the theft of credentials used on the web that may not be stored in the system. Additionally, the use of an SSH tunnel to forward RDP to an external server provides attackers with a reliable way to login remotely to a system, bypassing firewall control.
- A password stealer that collects all the credentials available on the system.
- A "backdoor" that sets up remote access via a stealth Microsoft Remote Desktop session by forwarding the RDP port through an SSH tunnel, allowing access to systems even when behind a firewall.
- A malicious browser extension that contains several information-stealing features, such as keylogging and taking screenshots.
The attack begins when a victim looks for a particular piece of software for download. Talos believes the attacker has set up an advertising campaign that will present links to a web page, offering the download of a software installer. The installer has many different file names. For example: viber-25164.exe, wechat-35355.exe, build_9.716-6032.exe, setup_164335.exe, nox_setup_55606.exe and battlefieldsetup_76522.exe. When executed, this installer does not install the actual software it announces, but instead executes a malicious loader on the system.
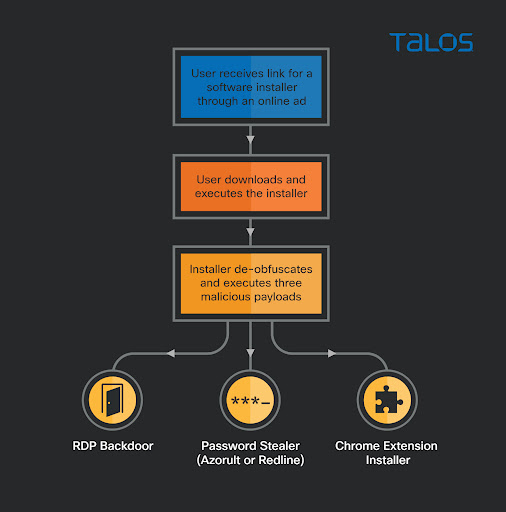
The installer/loader is an SFX-7-Zip archive or a nullsoft installer that decodes and drops a legitimate AutoIt interpreter, and three obfuscated AutoIt scripts that decode the final payloads in memory and inject them into the memory of another process. The final payloads are almost always the same three specific pieces of malware:
- A commodity password stealer. Initially Azorult and currently Redline. Both steal all the credentials it can find on the system. These password stealers are widely known and documented and we will analyse them further on this post.
- A backdoor, or backdoor installer that we are calling "MagnatBackdoor," that configures the system for stealthy RDP access, adds a new user and sets a scheduled task to periodically ping the C2 and, when instructed, create an outbound ssh tunnel forwarding the RDP service.
- An installer for a chrome extension, that we are calling "MagnatExtension," that packs several features useful for stealing data from the web browser: a form grabber, keylogger, screenshotter, cookie stealer and arbitrary JavaScript executor, among others.

Magnat campaigns use malvertising to deliver information stealer, backdoor and malicious Chrome extension
By Tiago Pereira. * Talos recently observed a malicious campaign offering fake installers of popular software as bait to get users to execute malware on their systems. * This campaign includes a set of malware distribution campaigns that started in late 2018 and have targeted mainly Canada...
 blog.talosintelligence.com
blog.talosintelligence.com


