- Oct 23, 2012
- 12,527
Security experts from Heimdal Security are warning against a new wave of malvertising that redirects users to malicious websites hosting the RIG exploit kit, which in the end infects victims with the CrypMIC ransomware.
This most recent wave of infections comes on the heels of a malvertising campaign that Cisco and GoDaddy brought down at the start of the month.
That particular malvertising campaign was exploiting advertising companies that deployed OpenX servers in order to inject malicious JavaScript code inside ads and redirect users to malicious websites hosting the Neutrino exploit kit.
Heimdal now says that there's an increase in the number of malvertising attacks that are leveraging the RIG exploit kit.
"RIG exploit kit has been spotted in several campaigns that use an 'iframe src' as the malicious inject to divert traffic to the arbitrary web pages created through domain shadowing," Heimdal's Andra Zaharia wrote today.
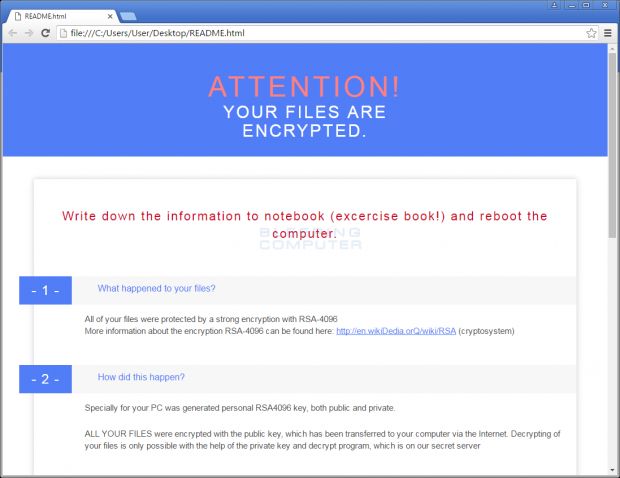
These RIG exploit kit installations use several recently disclosed Flash vulnerabilities to infect users with the same payload as the Neutrino campaigns, the CrypMIC ransomware.
This particular ransomware appeared over the summer, and it is a clone - with some variations - of the more famous CryptXXX ransomware.
This most recent wave of infections comes on the heels of a malvertising campaign that Cisco and GoDaddy brought down at the start of the month.
That particular malvertising campaign was exploiting advertising companies that deployed OpenX servers in order to inject malicious JavaScript code inside ads and redirect users to malicious websites hosting the Neutrino exploit kit.
Heimdal now says that there's an increase in the number of malvertising attacks that are leveraging the RIG exploit kit.
"RIG exploit kit has been spotted in several campaigns that use an 'iframe src' as the malicious inject to divert traffic to the arbitrary web pages created through domain shadowing," Heimdal's Andra Zaharia wrote today.
These RIG exploit kit installations use several recently disclosed Flash vulnerabilities to infect users with the same payload as the Neutrino campaigns, the CrypMIC ransomware.
This particular ransomware appeared over the summer, and it is a clone - with some variations - of the more famous CryptXXX ransomware.
A recent report released by Digital Shadows reveals that RIG is one of the five active exploit kits left on the market today, along with Neutrino, Magnitude, Sundown, and the lesser known Hunter EK.