A malvertising group nicknamed KovCoreG by security researchers has been using fake browser and Flash updates to trick users into installing the Kovter malware.
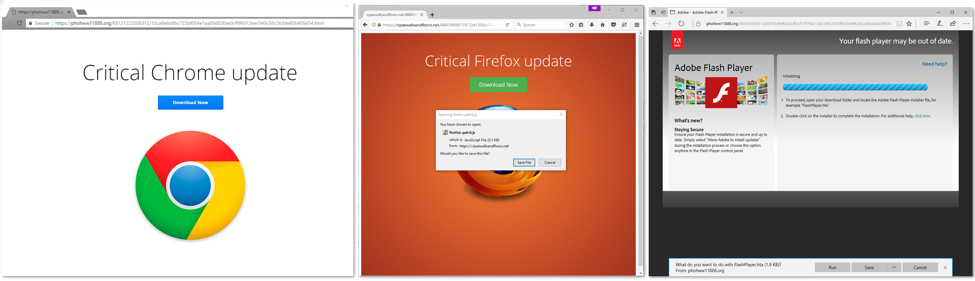
Attackers used malicious ads on PornHub to redirect users to a scam site that was advertising an urgent update. Depending on their browser, users got different messages.
For example, users arriving on this page via Chrome and Firefox were asked to download a browser update, while IE and Edge users were asked to download a Flash update.
The downloadable files were JavaScript (Chrome, Firefox) or HTA (IE, Edge) files that installed Kovter, a multi-purpose malware downloader that can deliver ad fraud malware, ransomware, infostealers, or more.