D
Deleted member 21043
Thread author
Hi everyone,
Previous guide in the series: Malware Analysis #5 - Covering just a tad more information
By the end of this guide, you should be aware and understand the following:
- What a packer is and what they are used for
- How malware writers pack files
- How to identify if a file is packed and what it was packed by
- Some examples of different packer types
- HEX signature for UPX
Let's get started!
Part 1 - What is a packer, and what are they used for?
Packers are basically a way of encrypting the contents of a file. Packers are often used by malware writers with their malware samples to try to avoid detection from their sample and to also make the sample smaller.
For example, let's say an Antivirus company has a sample which is malicious. They complete analysis on the file, and they decide to add HEX signatures which will be used to detect other samples with similarities to this malware sample (generic signatures). Of course, this can create false positives, but it helps detect malware. Then, there is a new sample which would be detected. However, the sample is then encrypted through a packer, let's say UPX. The data is now encrypted, therefore the HEX is not the same as it was before. When the Antivirus or Antimalware product scans the file, even though it will do things in the first sample, since the HEX is different, hence the data is encrypted, the detection is missed, thus avoiding the detection.
As a lookover from Antivirus companies, they now may have a strategy of developing "unpackers". Meaning, they will check if a file is packed, and if it is they may detect the file based on the packer, or attempt to "unpack" the file to then scan the unpacked version. This helps the Antivirus company with detections.
Of course, legitimate companies also have the right to use packers. This may be to make the file size smaller, preventing a increase length of time duration to download their installer/program off the website, download files in the installer (if it's a installer which downloads files), software updates and so on. However, malware writers use it as a common method to try to avoid detection.
Part 2 - How malware writers pack files
If you've ever wondered how malware writers pack files... Now is the time you will find out.
Before a malware writer can pack his sample, he must find a packer he likes and wants to use. An example of a well-known packer I will use for this article is UPX compression/packing. Of course, there are many other packers. I will list many more at the bottom of this guide, for you to experiment with, if you like.
Once the malware writer has decided on the packer he wishes to use, usually they try and find packers which are unknown or brand new to avoid detection - antivirus companies develop unpacking technology and keep it updated regularly, and generic detections for certain packers all the time - they need to download the chosen packer.
Since we will be using UPX for this guide, we will download UPX packer/compressor from the following source, the official source:
UPX: the Ultimate Packer for eXecutables - Homepage
Click "Download UPX" -
Once downloaded, extract the contents of the ZIP to a folder. I would put this anywhere from your desktop to the analysis folder. You could create a folder called "packers", and store them all in there. Building a nice collection. This would be a good idea if you would like to become a malware researcher or help make signatures for AV companies, since you could find packers unknown and undetected by AV companies, make a detection for it and send it off to them. Anyway, let's continue...
Inside the folder should be a bunch of files, as well as the file we will be interacting with... upx.exe.
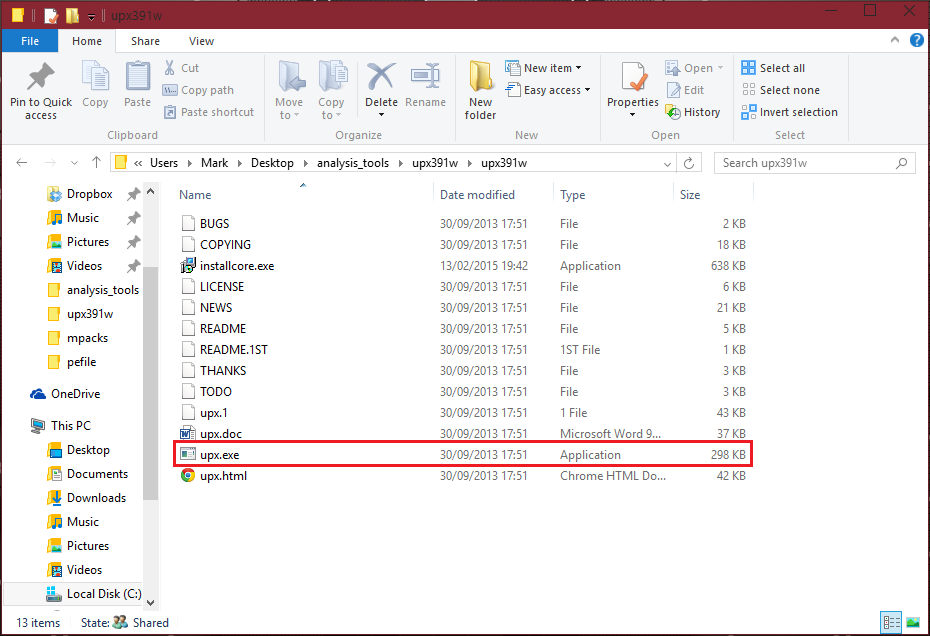
Now, before we can continue, you need to have a file. This can be any file, it doesn't "need" to be a malware sample. Of course, if you wish to try this with a malware sample, feel free... Just make sure to use a Virtual Machine for doing anything malware-related say on case something goes wrong. Also, remember from the first guide, to secure the VM. I do not personally feel my first guide was detailed enough with securing a VM, I will make a thread within next few days more about it. Just, for now, remember the things from first guide.
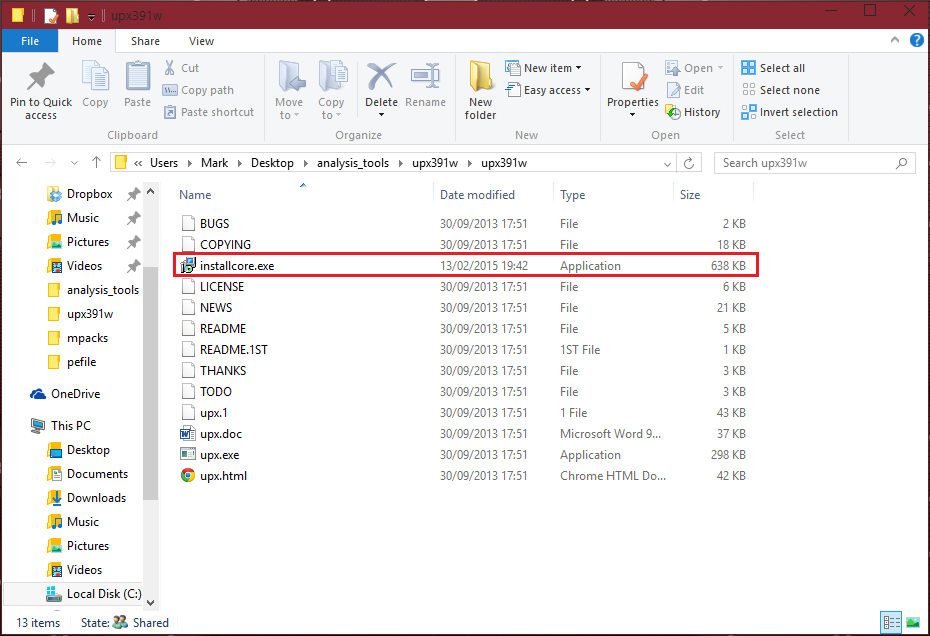
Once you have your file, copy and paste it to the folder with upx (same directory upx.exe is located at). For the purpose of this tutorial, I will be using a adware sample, with the filename "installcore.exe". I have already copied it over to the folder, before I made the above screenshot.
Now, how to use UPX to pack the file:
Open up CMD, preferably as administrator.
Use the cd command to navigate to the folder where upx is.
Now, type the following command: upx.exe <filename.extension>
You may be confused with the above command with the "<" and "> stuff, so I will show you what my command will look like for my file "installcore.exe": upx.exe installcore.exe
Then hit enter.
If everything went correctly, UPX will pack your file. All the screenshots are below:
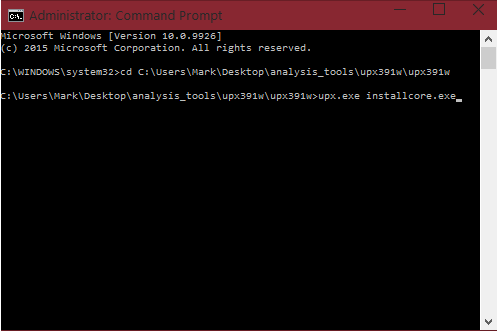
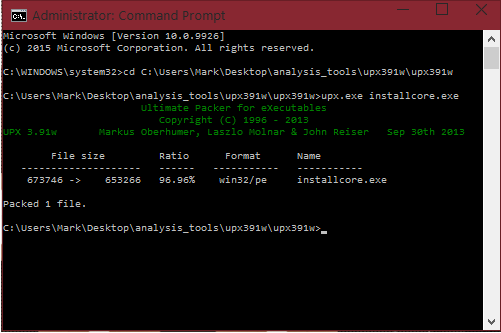
Well done, you now have a file to TEST the identifying and unpacking tutorials with. Remember, you don't need to use malware at first. If you do, please stick to a VM. Now, we will learn how to use a tool to identify a packed file!
NOTE: UPX is not malicious. Only samples which are malicious by UPX are malicious. Just because you find a file packed by UPX doesn't make it malware. You must unpack the file to do some analysis, though.
Part 3 - Identifying a packed file and what it is packed by
Finally! We have got to the real "analysis" counting part of the guide! Now, we will learn how to identify a packed file, and what it is packed by.
For this guide, we will use a well-known tool called PEiD. You can download it from the following website:
PE iDentifier (PEiD) 0.95 / Binary Analysis / Editing / Downloads - Tuts 4 You
Once it is downloaded, extract the contents of the ZIP to a folder. Open up this folder you extracted it too.
The contents of the folder should look like as follows:
We are interested in PEiD.exe. Open it up. It should look like as follows:
If you wish to scan multiple files, click Multi-Scan. Otherwise, you can click the "..." button, which represents "Browse for a file":
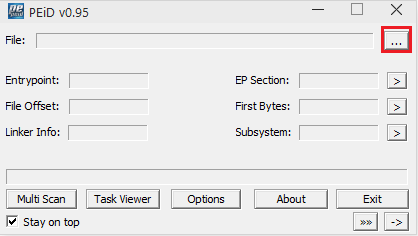
Choose a file. I will choose the UPX packed installcore.exe file in my upx folder.
As expected, PEiD will identify the file as being packed with UPX:
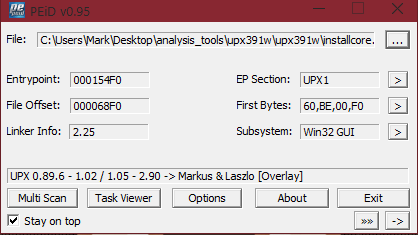
We can see in the textbox at the bottom it says "UPX 0.89.6 - 1.0.2 ......".
As well as being given this information, we are provided with additional information such as the Entrypoint, File Offset, Linker info, EP Section, First Bytes and Subsystem.
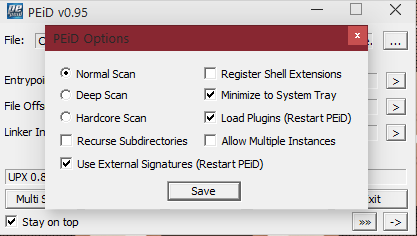
PEiD also inclues a Task Viewer and options. Under Options, I recommend keeping it set to "Normal", however if you wish to change it to Deep or Hardcore scan, okay.
Part 4 - Examples of other packers
Packer methods:
Runtime packers - unpacks itself once executed (this unpacked copy is executed and loaded in RAM).
I will mention more in the future.
Part 5 - HEX signature for UPX
I am unsure if anyone is interested in this, however UPX apps can be detected easily just by finding 55 50 58 in the HEX, which represents UPX. Yes, it's in there.
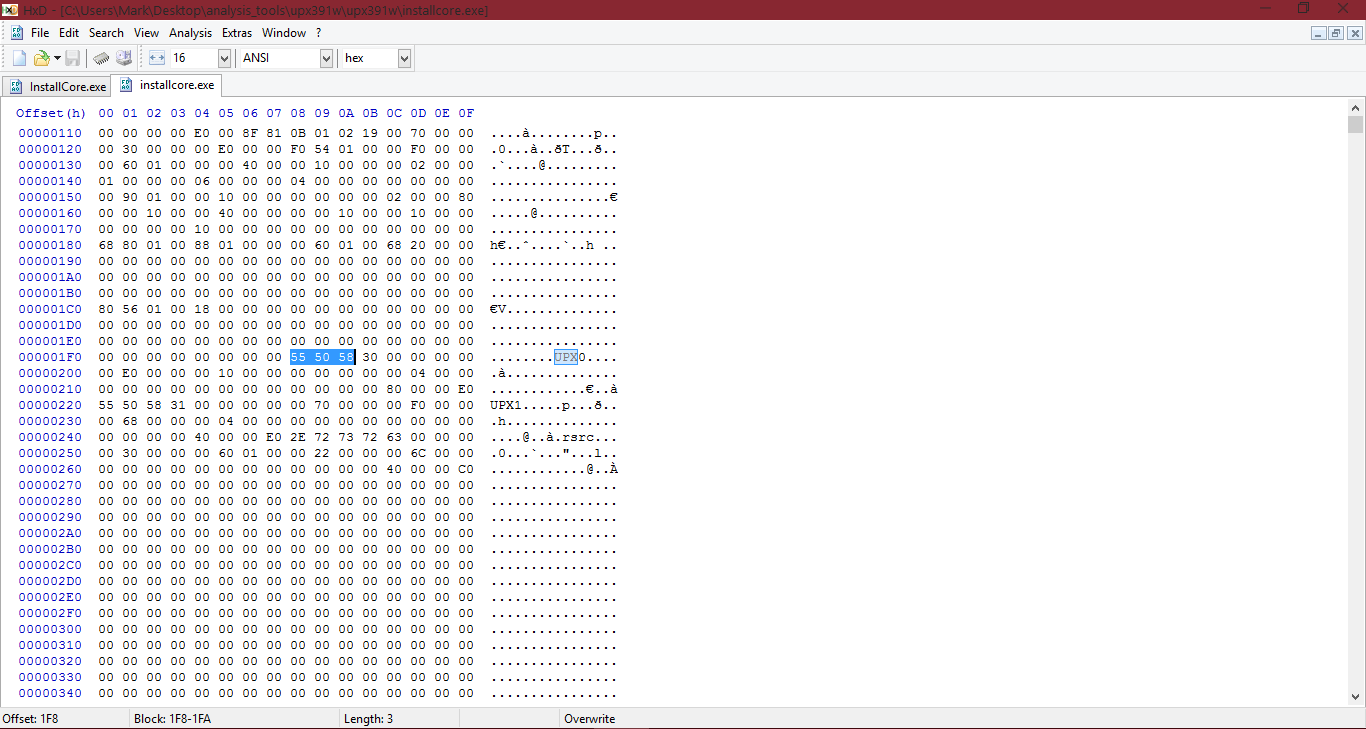
NOTE: UPX0/1 can be renamed to something else. If you know about creating signatures then of course you'll be able to make a good one, however as an example I will leave the above information with UPX0 and UPX1...
Cheers.
Previous guide in the series: Malware Analysis #5 - Covering just a tad more information
By the end of this guide, you should be aware and understand the following:
- What a packer is and what they are used for
- How malware writers pack files
- How to identify if a file is packed and what it was packed by
- Some examples of different packer types
- HEX signature for UPX
Let's get started!
Part 1 - What is a packer, and what are they used for?
Packers are basically a way of encrypting the contents of a file. Packers are often used by malware writers with their malware samples to try to avoid detection from their sample and to also make the sample smaller.
For example, let's say an Antivirus company has a sample which is malicious. They complete analysis on the file, and they decide to add HEX signatures which will be used to detect other samples with similarities to this malware sample (generic signatures). Of course, this can create false positives, but it helps detect malware. Then, there is a new sample which would be detected. However, the sample is then encrypted through a packer, let's say UPX. The data is now encrypted, therefore the HEX is not the same as it was before. When the Antivirus or Antimalware product scans the file, even though it will do things in the first sample, since the HEX is different, hence the data is encrypted, the detection is missed, thus avoiding the detection.
As a lookover from Antivirus companies, they now may have a strategy of developing "unpackers". Meaning, they will check if a file is packed, and if it is they may detect the file based on the packer, or attempt to "unpack" the file to then scan the unpacked version. This helps the Antivirus company with detections.
Of course, legitimate companies also have the right to use packers. This may be to make the file size smaller, preventing a increase length of time duration to download their installer/program off the website, download files in the installer (if it's a installer which downloads files), software updates and so on. However, malware writers use it as a common method to try to avoid detection.
Part 2 - How malware writers pack files
If you've ever wondered how malware writers pack files... Now is the time you will find out.
Before a malware writer can pack his sample, he must find a packer he likes and wants to use. An example of a well-known packer I will use for this article is UPX compression/packing. Of course, there are many other packers. I will list many more at the bottom of this guide, for you to experiment with, if you like.
Once the malware writer has decided on the packer he wishes to use, usually they try and find packers which are unknown or brand new to avoid detection - antivirus companies develop unpacking technology and keep it updated regularly, and generic detections for certain packers all the time - they need to download the chosen packer.
Since we will be using UPX for this guide, we will download UPX packer/compressor from the following source, the official source:
UPX: the Ultimate Packer for eXecutables - Homepage

Click "Download UPX" -

Once downloaded, extract the contents of the ZIP to a folder. I would put this anywhere from your desktop to the analysis folder. You could create a folder called "packers", and store them all in there. Building a nice collection. This would be a good idea if you would like to become a malware researcher or help make signatures for AV companies, since you could find packers unknown and undetected by AV companies, make a detection for it and send it off to them. Anyway, let's continue...
Inside the folder should be a bunch of files, as well as the file we will be interacting with... upx.exe.

Now, before we can continue, you need to have a file. This can be any file, it doesn't "need" to be a malware sample. Of course, if you wish to try this with a malware sample, feel free... Just make sure to use a Virtual Machine for doing anything malware-related say on case something goes wrong. Also, remember from the first guide, to secure the VM. I do not personally feel my first guide was detailed enough with securing a VM, I will make a thread within next few days more about it. Just, for now, remember the things from first guide.
Once you have your file, copy and paste it to the folder with upx (same directory upx.exe is located at). For the purpose of this tutorial, I will be using a adware sample, with the filename "installcore.exe". I have already copied it over to the folder, before I made the above screenshot.

Now, how to use UPX to pack the file:
Open up CMD, preferably as administrator.
Use the cd command to navigate to the folder where upx is.
Now, type the following command: upx.exe <filename.extension>
You may be confused with the above command with the "<" and "> stuff, so I will show you what my command will look like for my file "installcore.exe": upx.exe installcore.exe
Then hit enter.
If everything went correctly, UPX will pack your file. All the screenshots are below:


Well done, you now have a file to TEST the identifying and unpacking tutorials with. Remember, you don't need to use malware at first. If you do, please stick to a VM. Now, we will learn how to use a tool to identify a packed file!
NOTE: UPX is not malicious. Only samples which are malicious by UPX are malicious. Just because you find a file packed by UPX doesn't make it malware. You must unpack the file to do some analysis, though.
Part 3 - Identifying a packed file and what it is packed by
Finally! We have got to the real "analysis" counting part of the guide! Now, we will learn how to identify a packed file, and what it is packed by.
For this guide, we will use a well-known tool called PEiD. You can download it from the following website:
PE iDentifier (PEiD) 0.95 / Binary Analysis / Editing / Downloads - Tuts 4 You

Once it is downloaded, extract the contents of the ZIP to a folder. Open up this folder you extracted it too.
The contents of the folder should look like as follows:

We are interested in PEiD.exe. Open it up. It should look like as follows:

If you wish to scan multiple files, click Multi-Scan. Otherwise, you can click the "..." button, which represents "Browse for a file":

Choose a file. I will choose the UPX packed installcore.exe file in my upx folder.
As expected, PEiD will identify the file as being packed with UPX:

We can see in the textbox at the bottom it says "UPX 0.89.6 - 1.0.2 ......".
As well as being given this information, we are provided with additional information such as the Entrypoint, File Offset, Linker info, EP Section, First Bytes and Subsystem.
PEiD also inclues a Task Viewer and options. Under Options, I recommend keeping it set to "Normal", however if you wish to change it to Deep or Hardcore scan, okay.

Part 4 - Examples of other packers
Packer methods:
Runtime packers - unpacks itself once executed (this unpacked copy is executed and loaded in RAM).
I will mention more in the future.
Part 5 - HEX signature for UPX
I am unsure if anyone is interested in this, however UPX apps can be detected easily just by finding 55 50 58 in the HEX, which represents UPX. Yes, it's in there.

NOTE: UPX0/1 can be renamed to something else. If you know about creating signatures then of course you'll be able to make a good one, however as an example I will leave the above information with UPX0 and UPX1...
Cheers.
Last edited by a moderator: