Feature-rich remote access malware Pekraut emerges. The rodent seems to be of German origin and is ready to be released. We analyzed the malware in-depth.
While searching for new malware via suspicious pathes, a fake
svchost.exe in %APPDATA%/Microsoft tipped us off. The sample[1] is a .NET application which is packed with
ConfuserEx. The file was uploaded as
netRat.exe to Virustotal. The same name is also stated in the file's version information as InternalName and OriginalFilename. Version information also has a copyright statement for 2019.
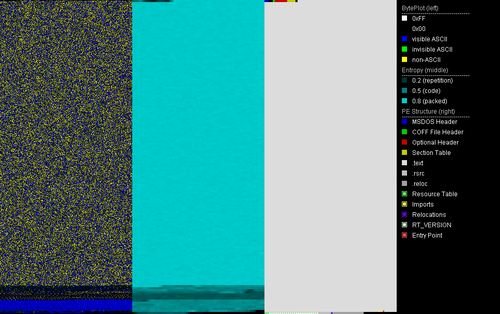
PortexAnalyzer output for ConfuserEx packed Pekraut sample
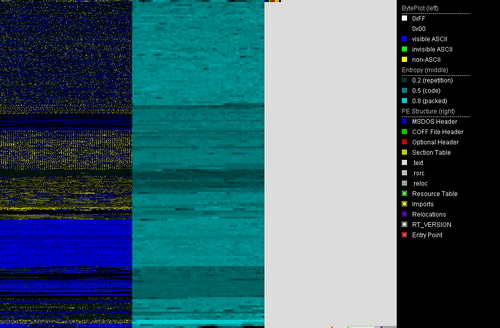
PortexAnalyzer output for unpacked Pekraut sample
Via similarity search we found a second sample[2] that was uploaded to Virustotal a day later. It is not packed but obfuscated with Dotfuscator. Unpacking the ConfuserEx sample[1] results in a file that is almost the same as the second sample[2].
The obfuscation removed the original names of .NET symbols like classes, variables and methods. We didn't find any non-obfuscated Pekraut sample, so we manually named the symbols based on their usage resulting in sample[3]. The deobfuscated sample[3] is also used for screenshots in this article. Please note that those symbol names aren't part of the original source code and thus do not suffice for signatures.
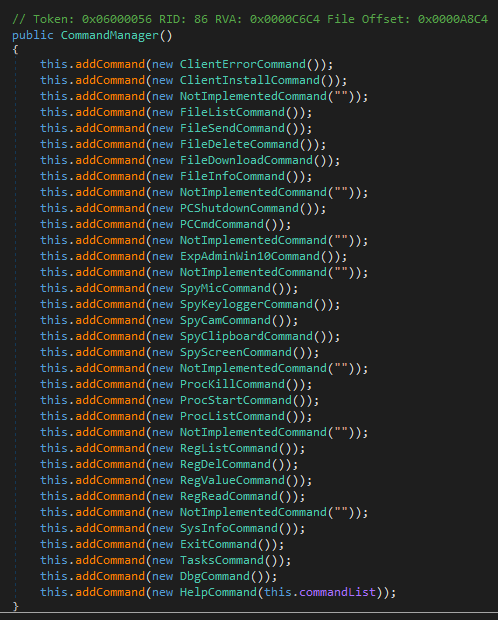
Pekraut RAT's command list
Pekraut's client accepts 27 commands. The
help command sends a German description for every command to the server. The commands themselves are still English, though.
Some commands aren't exactly offering what the explanations are saying. E.g. the
dbg command is not fully implemented.
The class responsible for managing all commands has seven placeholder objects in the command listing (see image below). The reason is most likely just a quirky way to place a newline when printing the help string of all commands.
To sum up, the whole RAT is quite function-rich and fully implemented except for the debugging option. Malware authors are not excempt from being so confident in their code that precautionary steps are neglected.
The table below sums up our analysis of the actual implementation for the commands.
| Command | Description |
|---|
| spy_cb | Writes the clipboard data or reads and sends it back to the server. Images stored in the clipboard are also supported. |
| spy_keylogger | Logs keystrokes. Supports these special keys: VK_OEM_NEC_EQUAL, VK_LShift, VK_RShift, VK_Scroll, VK_LMenu, VK_RMenu, VK_RControl, VK_LControl |
| spy_mic | Starts and stops recording with a microphone and sends the data to the server. |
| spy_scr | Shows information about a screen or takes a screenshot for a chosen screen and sends it to the server. |
| spy_cam | Takes a single picture via webcam or streams webcam to the server. |
| reg_list | Lists all subkeys and values of a given registry key. |
| reg_del | Deletes a registry key/value and sends the deleted key to the server. |
| reg_read | Reads a registry value and sends it to the server. |
| reg_value | Creates/writes a value in the registry. |
| proc_kill | Kills a process via name or ID. |
| proc_list | Sends process names and IDs of all running processes to the server. |
| proc_start | Executes a file via a given path. |
| file_delete | Deletes a file or folder. |
| file_download | Downloads a file from a given URL. |
| file_info | Sends the following information about a file to the server : filename, filename extension, size, creation date, last access and the read-only attribute. |
| file_list | Sends all file and folder names within a folder to the server. Extra option to list all available drives. |
| file_send | Sends a file to the server. |
| exploit_admin_win10 | Uses a Windows 10 UAC bypass method to start a given program with admin rights. More details to this later on. |
| pc_cmd | Starts a command via cmd.exe and sends the output to the server. |
| pc_shutdown | Shuts down the PC. |
| sysinfo | Sends information like the machine name, the username, the OS and processor architecture, the screen count, the webcam count and the microphone count to the server. |
| dbg | Option to start an endless-loop. Supposed to debug the client but not fully implemented yet. |
| exit | Disconnects from the server and terminates itself. |
| help | Sends all commands / the description of a command to the server. |
| client_err | Sends the last error to the server. |
| tasks | Sends currently executed commands to the server and has the option to terminate them. |
| client_install | Installs / uninstalls the client by using the procedure outlined in PekrautRAT's install / uninstall routine. |