I had suspicion the trading software I use (CryptoRocket Metatrader 4) was malicious. The following reports from VirusTotal and Hybrid Analysis showed the sandbox/behavior analysis reports flagged them as malicious:
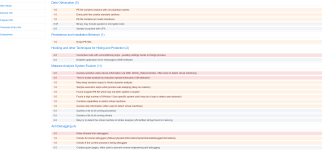
First Sandbox Report (threat score at the top right is 100/100):
Hybrid Analysis
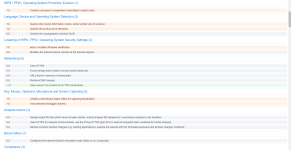
Second Sandbox Report (mentions of keylogger and persistence):
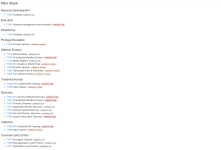
VirusTotal pt.1 -- VirusTotal pt.2 -- VirusTotal pt.3 -- VirusTotal pt.4
(*included screenshots of these in the attached incase links don't work)
From a malware signature scanning lens, the software was only flagged by 2 out the 62 total scanning vendors so I decided not to link that. Again, I know MetaTrader 4 is a trusted trading software but my version of MetaTrader 4 is from CryptoRocket. I've read online CryptoRocket is a very shady company so I wouldn't put it pass them if they ended up having malware in their applications.
Please let me know what you guys think of the behavior analysis reports. Thanks!
First Sandbox Report (threat score at the top right is 100/100):
Hybrid Analysis
Second Sandbox Report (mentions of keylogger and persistence):
VirusTotal pt.1 -- VirusTotal pt.2 -- VirusTotal pt.3 -- VirusTotal pt.4
(*included screenshots of these in the attached incase links don't work)
From a malware signature scanning lens, the software was only flagged by 2 out the 62 total scanning vendors so I decided not to link that. Again, I know MetaTrader 4 is a trusted trading software but my version of MetaTrader 4 is from CryptoRocket. I've read online CryptoRocket is a very shady company so I wouldn't put it pass them if they ended up having malware in their applications.
Please let me know what you guys think of the behavior analysis reports. Thanks!