L
LabZero
Thread author
Introduction
In this thread I'd like to make a dynamic analysis of a malware using Regshot.
This software allows you to track changes made to the Windows registry by the installation of a program or, in our case, by running a malware.
The tutorial of Regshot it was illustrated by @kram7750 in his thread: http://malwaretips.com/threads/how-to-start-analyzing-malware-guide.42291/
In the future, in the next report, if other tools tool works for analysis malware, I'll do a tutorial (if it doesn't already exist) as an introduction to proper use.
I thought I'd make a simple outline for posting the reports in order to simplify the procedure (I hope you like it, all comments are useful).
Of course before you begin, you must have a virtualization software to create a totally isolated Guest system from the Host system.
A virtual machine, Virtualbox or VMware Player.
I try ' Shadow Defender (light virtualization) , a shareware program very stable and secure.
OK, let's get started.
Virtualization tool
Shadow Defender : http://www.shadowdefender.com/
Malware Analysis tool
Regshot : http://sourceforge.net/projects/regshot/
Tipe of Analysis
Dynamic
Malware Identification
Adware
Link to malicious samples : hxxp://rghost.net/7FqNDWSG4
Archive password
infected
VirusTotal report link : https://www.virustotal.com/it/file/...7f1be5b705ebd0f210094fd6/analysis/1428851615/
Malware Analysis
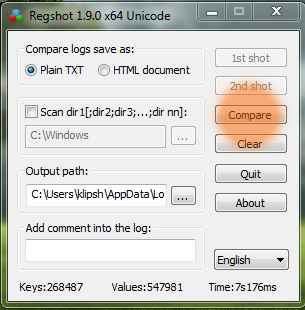
Run Regshot
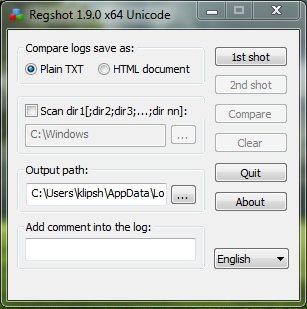
Create 1°snapshot to save the state of the registry before you run the malware.
After this step, do not start other applications to not create other changes besides those of the malware.
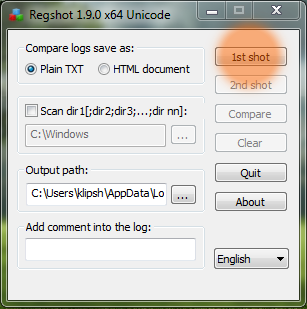
Run malware
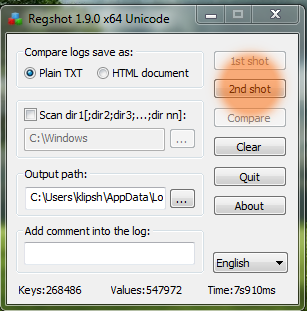
Create 2° snapshot to save the state of the register after execution of the malware
Click Compare to have the results log
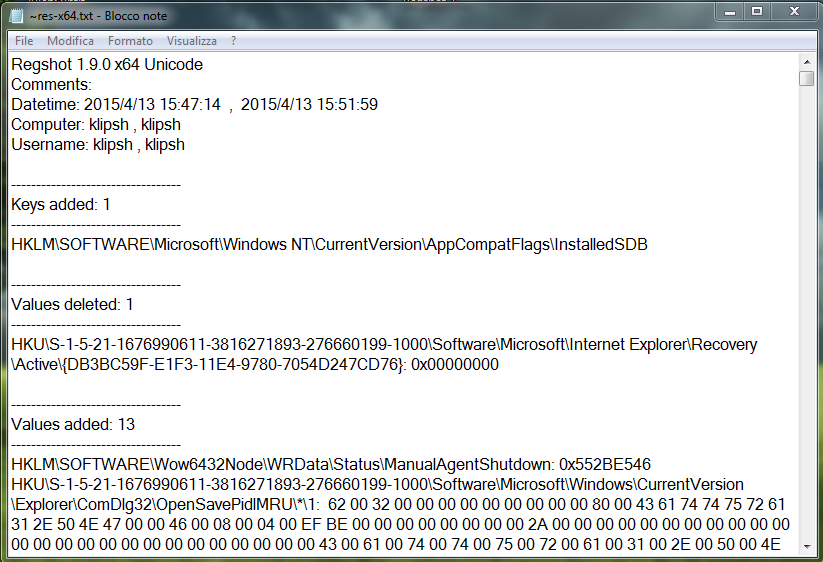
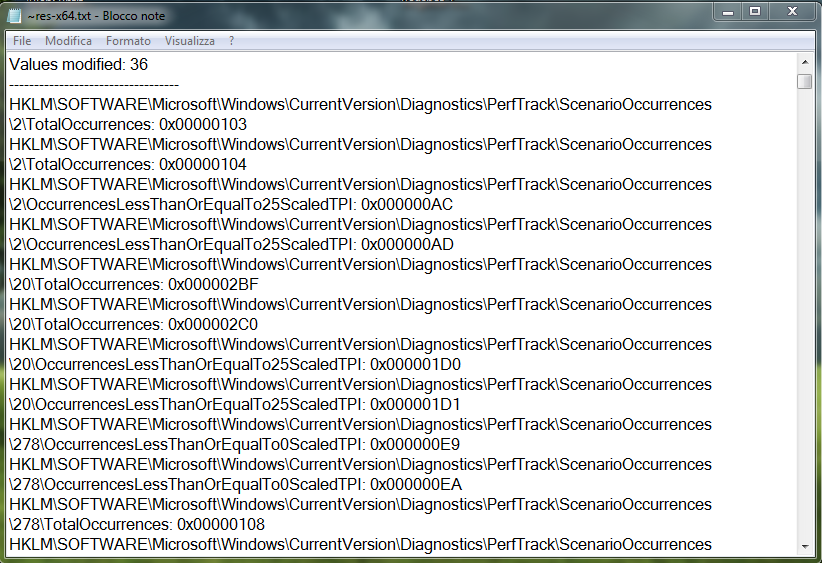
Comments
From the comparison of the results you can see registry entries created and modified by malware.
Checking carefully you can understand the actions taken by the malware to the operating system.
Enjoy with Malware Analysis
In this thread I'd like to make a dynamic analysis of a malware using Regshot.
This software allows you to track changes made to the Windows registry by the installation of a program or, in our case, by running a malware.
The tutorial of Regshot it was illustrated by @kram7750 in his thread: http://malwaretips.com/threads/how-to-start-analyzing-malware-guide.42291/
In the future, in the next report, if other tools tool works for analysis malware, I'll do a tutorial (if it doesn't already exist) as an introduction to proper use.
I thought I'd make a simple outline for posting the reports in order to simplify the procedure (I hope you like it, all comments are useful).
Of course before you begin, you must have a virtualization software to create a totally isolated Guest system from the Host system.
A virtual machine, Virtualbox or VMware Player.
I try ' Shadow Defender (light virtualization) , a shareware program very stable and secure.
OK, let's get started.
Virtualization tool
Shadow Defender : http://www.shadowdefender.com/
Malware Analysis tool
Regshot : http://sourceforge.net/projects/regshot/
Tipe of Analysis
Dynamic
Malware Identification
Adware
Link to malicious samples : hxxp://rghost.net/7FqNDWSG4
Archive password
infected
VirusTotal report link : https://www.virustotal.com/it/file/...7f1be5b705ebd0f210094fd6/analysis/1428851615/
Malware Analysis
Run Regshot
Create 1°snapshot to save the state of the registry before you run the malware.
After this step, do not start other applications to not create other changes besides those of the malware.
Run malware
Create 2° snapshot to save the state of the register after execution of the malware
Click Compare to have the results log
Comments
From the comparison of the results you can see registry entries created and modified by malware.
Checking carefully you can understand the actions taken by the malware to the operating system.
Enjoy with Malware Analysis
Last edited by a moderator: