An end-of-the-year report from US cyber-security firm Malwarebytes reveals that ransomware, adware, and cryptojacking were extremely popular with cyber-criminals in 2017.
Data compiled by the company's security products reveals growth in almost all cyber-crime categories, with 2017 being a very successful year across the board for malware authors, phishers, and other cyber-criminal groups.
Record ransomware volumes in 2017
According to the Malwarebytes' 2017 State of Malware Report, ransomware attacks against consumers went up more than 93% while ransomware attacks against businesses increased 90%.
Of all of 2017, the month of September was the busiest one, while the period between July 2017 and September 2017 saw a 700% increase in ransomware attacks overall, compared to the same period in 2016.
The security firm says that most of the ransomware detections during the past year came for families like WannaCry, Locky, Cerber, and GlobeImposter.
Seeing ransomware among Malwarebytes' top threats of 2017 is no surprise if we remember that 2017 saw three major ransomware outbreaks —WannaCry, NotPetya, BadRabbit— that made tens of thousands of victims worldwide.
Despite this, self-spreading ransomware was not such a big problem, and most infections came from mundane spam campaigns and malvertising/exploit kits.
As for the rest of the malware scene, here are some of the other key findings from Malwarebytes' 2017 State of Malware Report:
◙ Malwarebytes blocked an average of 8 million cryptojacking (in-browser mining) attempts per day.
◙ The second half of the year marked an average of 102% increase in banking trojan detections.
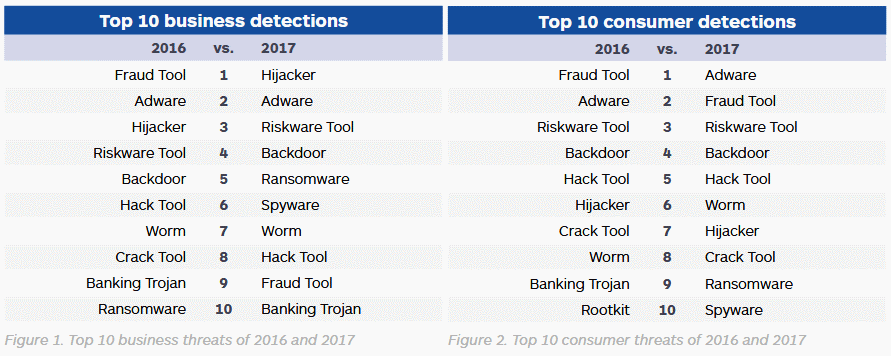
◙ Adware became the top threat to home users in 2017.
◙ Hijackers became the top threat to businesses users in 2017.
◙ Adware volume is up, but there are fewer adware developers active.
◙ Detections of adware in 2017 showed immense distribution volume, up 132% year-over-year.
◙ Adware now represents almost 40% of our consumer
threat detections,
◙ Exploit kits took a dive while malspam was unleashed.
◙ 2017 showed little development for exploit kits.
◙ No new zero-day exploits were used by any of the remaining exploit kits still in the wild.
◙ Scams in 2017 were notable for a shift in tactics away from the traditional browser locker to phishing emails and malvertising.
◙ As Bitcoin price rose, there was an upswing in Bitcoin-related scams towards the end of 2017.
◙ Spyware saw a big uptick in attacks towards the end of 2017.