- Jan 24, 2011
- 9,378
Microsoft's security team finally addressed a zero-day vulnerability that affected both Internet Explorer and Edge, which was used for almost two years in a massive malvertising campaign exposed last month by Proofpoint security researchers.
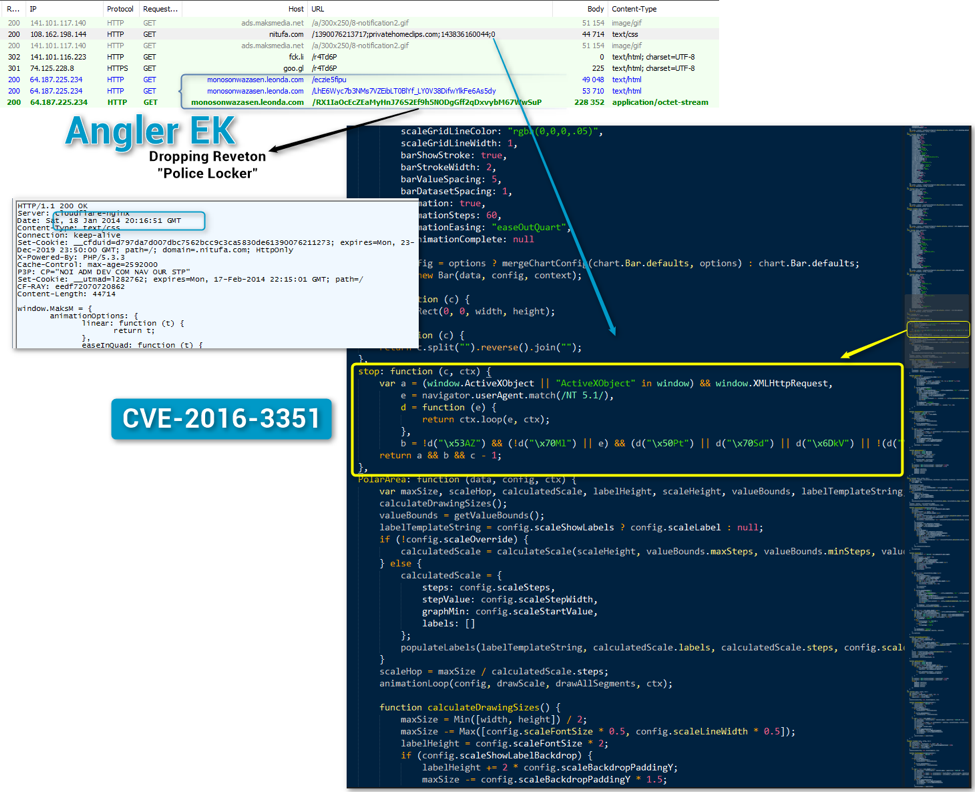
The zero-day, tracked by CVE-2016-3351, allowed the people behind this malvertising campaign to avoid security products and security engineers investigating the malicious ads.
Technically, the zero-day is an information disclosure bug that exposed details about the operating system via JavaScript calls executed inside the IE or Edge browsers, an attack also known as a "MIME type check."
Zero-day used to identify and avoid infosec researchers
Attackers using the zero-day were able to discover if certain file extensions had been assigned to locally installed applications. They used this information to see if file extensions often used by reverse engineering software was found on the PC of a possible victim.
If they were, the people behind this massive malvertising campaign, known as AdGholas, could pretty accurately determine that the computer belonged to a security engineer or was running a sandboxed environment or virtual machine, where the malicious ad code was probably analyzed.
When this happened, further JavaScript redirections that led the user to the actual exploitation point, would not execute anymore, dropping the connection.
By default, the AdGholas malvertising campaigns checked for the presence for the following file extensions: .cap, .hwl, .har, .halog, .chls, .py, .bfr, and .pcap.
Proofpoint researchers, who discovered this zero-day, say this zero-day was also used to check if a user had Internet Explorer as his default web browsers.
Read more: Microsoft Patches IE and Edge Zero-Day Used in Massive Malvertising Campaign
The zero-day, tracked by CVE-2016-3351, allowed the people behind this malvertising campaign to avoid security products and security engineers investigating the malicious ads.
Technically, the zero-day is an information disclosure bug that exposed details about the operating system via JavaScript calls executed inside the IE or Edge browsers, an attack also known as a "MIME type check."
Zero-day used to identify and avoid infosec researchers
Attackers using the zero-day were able to discover if certain file extensions had been assigned to locally installed applications. They used this information to see if file extensions often used by reverse engineering software was found on the PC of a possible victim.
If they were, the people behind this massive malvertising campaign, known as AdGholas, could pretty accurately determine that the computer belonged to a security engineer or was running a sandboxed environment or virtual machine, where the malicious ad code was probably analyzed.
When this happened, further JavaScript redirections that led the user to the actual exploitation point, would not execute anymore, dropping the connection.
By default, the AdGholas malvertising campaigns checked for the presence for the following file extensions: .cap, .hwl, .har, .halog, .chls, .py, .bfr, and .pcap.
Proofpoint researchers, who discovered this zero-day, say this zero-day was also used to check if a user had Internet Explorer as his default web browsers.
Read more: Microsoft Patches IE and Edge Zero-Day Used in Massive Malvertising Campaign
