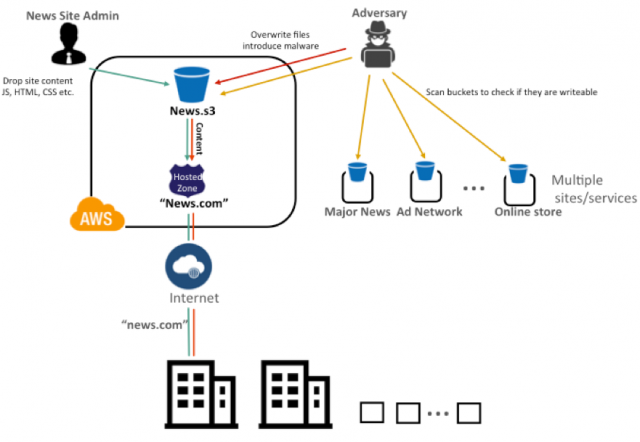
Hackers can exploit exposed Amazon S3 buckets to carry out silent Man-in-the-Middle attacks or other hacks on a company's customers or internal staff.
Codenamed GhostWriter, the technique relies on an attacker scanning the Internet and identifying misconfigured S3 buckets that not only have been left exposed online for anyone to view, but the server owner has also forgotten to restrict write access.
GhostWriter - replacing legitimate files with malicious ones
Attackers can leverage these S3 configuration mishaps to replace original files with modified versions that they use for nefarious purposes.
"Bucket owners who store JavaScript or other code should pay particular attention to this issue to ensure that 3rd parties don’t silently overwrite their code for drive-by attacks, Bitcoin mining, or other exploits," said Sekhar Sarukkai, Chief Scientist at
Skyhigh Networks.
Sarukkai details one of these attacks. For example, if an attacker finds an exposed S3 bucket with write access belonging to a news agency, the attacker could replace ad code and redirect revenue to his account or intercept and redirect subscription payments.