- Jan 24, 2011
- 9,378
Security researchers have gained access to one of the servers used by the Cerber gang, from where they were able to extract basic statistics about their operation.
A security researcher that only goes by the nickname of Racco42 discovered the vulnerability on Thursday, January 12.
The issue affected only one Cerber server, not all, and was most likely due to a misconfiguration. The server wasn't a command and control server, but a mere staging server from where the victims' computers would connect and download the actual ransomware, which would later run and infect their PCs.
Server errors lets researchers in
An error in one of the server files displayed page source code, instead of executing it.
This information found its way to Avast security researcher Jaromir Horejsi, who together with the Avast team leveraged this error to get control over the server.
For a period of three hours, the Avast teams explains, they collected information from server logs.
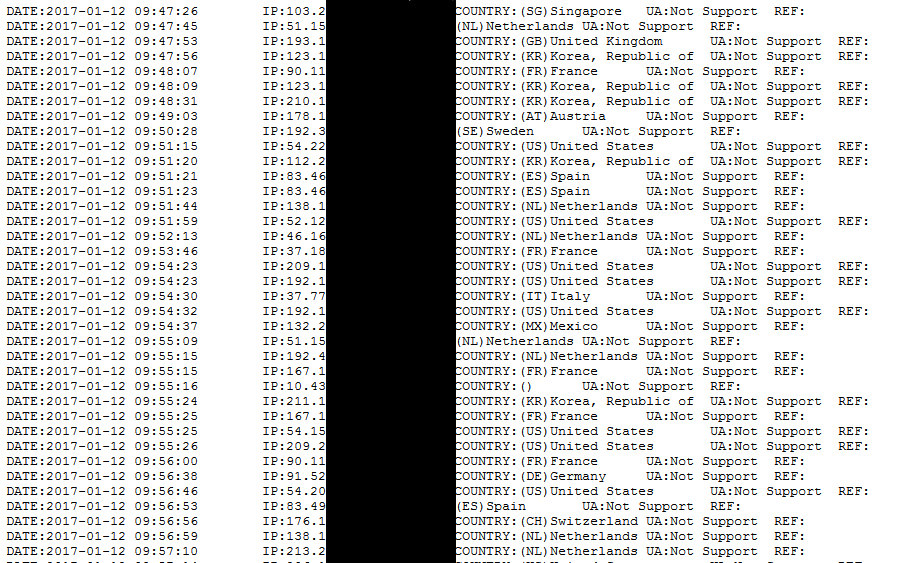
Log showing victims who downloaded the Cerber ransomware [Avast]
The Avast team observed over 700 victims download Cerber installers, which with no doubt encrypted their PCs.
Extrapolating this number to a whole day, just one typical Cerber ransomware staging server would be able to infect around 8,400 users during a spam run or malvertising campaigns.
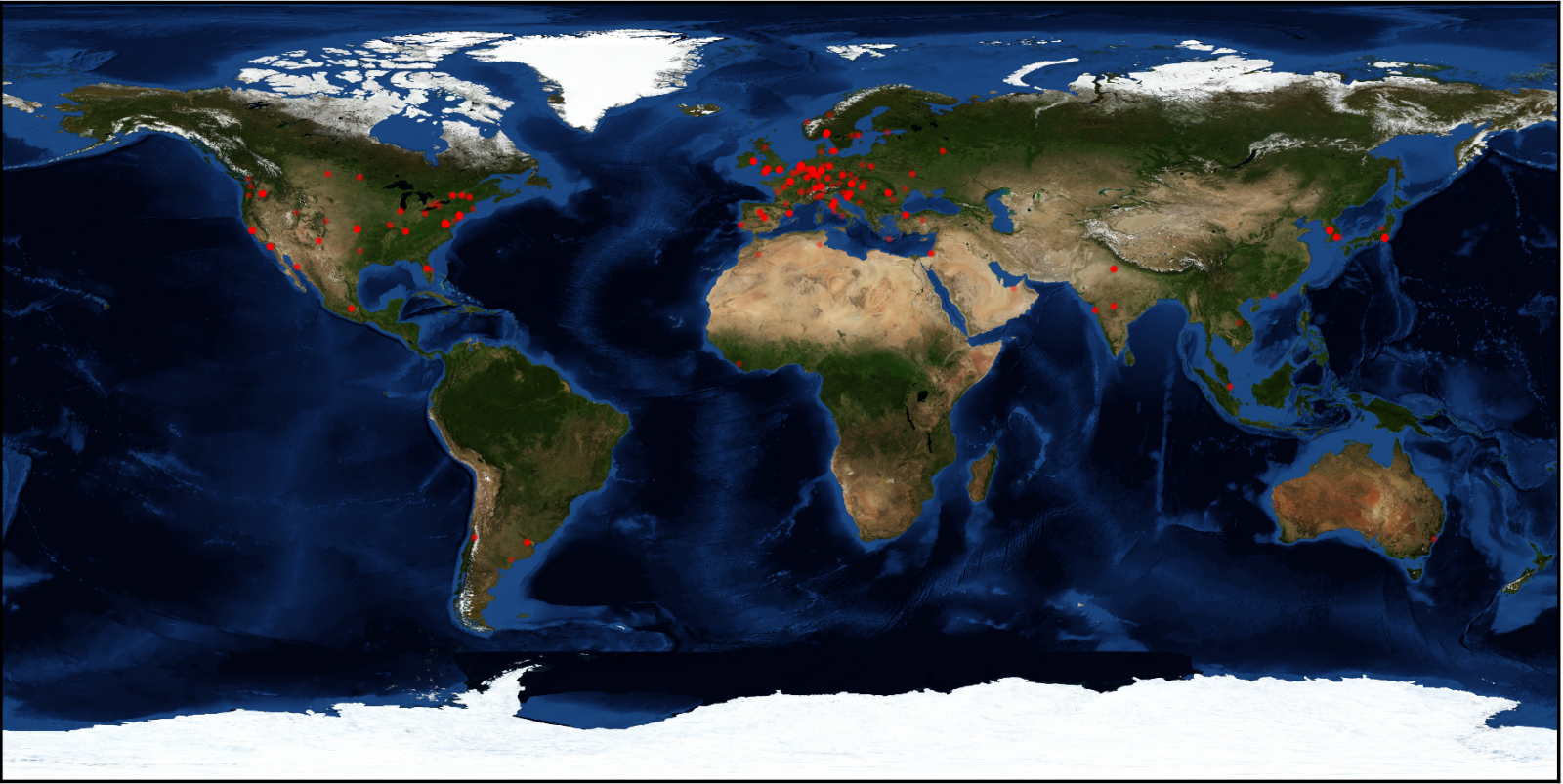
The data Avast researchers collected was plotted on a map which shows that most victims were located in Europe and North America.
Read more: Misconfigured Server Gives Insight Into Cerber Ransomware Operation
A security researcher that only goes by the nickname of Racco42 discovered the vulnerability on Thursday, January 12.
The issue affected only one Cerber server, not all, and was most likely due to a misconfiguration. The server wasn't a command and control server, but a mere staging server from where the victims' computers would connect and download the actual ransomware, which would later run and infect their PCs.
Server errors lets researchers in
An error in one of the server files displayed page source code, instead of executing it.
This information found its way to Avast security researcher Jaromir Horejsi, who together with the Avast team leveraged this error to get control over the server.
For a period of three hours, the Avast teams explains, they collected information from server logs.

Log showing victims who downloaded the Cerber ransomware [Avast]
The Avast team observed over 700 victims download Cerber installers, which with no doubt encrypted their PCs.
Extrapolating this number to a whole day, just one typical Cerber ransomware staging server would be able to infect around 8,400 users during a spam run or malvertising campaigns.
The data Avast researchers collected was plotted on a map which shows that most victims were located in Europe and North America.

Read more: Misconfigured Server Gives Insight Into Cerber Ransomware Operation
