D
Deleted member 21043
Thread author
Hi everyone, how are you all doing?
The purpose of this thread is dedicated to monitoring the Registry. In this thread I will be using a tool known as Regshot, which can be downloaded from the following URL:
To learn to use Regshot, please open up the following SPOILER:
If anyone else has a better tool for monitoring the Registry changes during Malware Analysis, feel free to post them in the comments. As long as it works as intended and does the job, there shouldn't be an issue with using another tool.
Anyway, time we got started at using Regshot to monitor the Registry with a sample.
WARNING: PLEASE USE A VIRTUAL MACHINE. DO NOT ATTEMPT TO CONTINUE ON YOUR MAIN SYSTEM.
To start off, download the sample (the download URL is attached to the top of this thread, the password to the archieve is also supplied underneath the download URL at the top of this thread).
Once the archieve is downloaded, extract the archieve to the Desktop.
Now, open up Regshot (with Administrative rights). It should look like this:

We will start by making our 1st shot before we execute the sample. Please take your 1st shot.
After you have taken your 1st shot, it's time to execute the sample!
Navigate to where you saved the sample... And execute it. [when I say "execute", I am referring to "opening". So when I say "execute it", I mean "open it". Just thought I'd get that out the way].
The installer will load. Wait for it, let it install. If you would like to view some screenshots I took during the installation process, you can view them in the following spoiler:




 (this screenshot is special because I took the screenshot as the text above the file path was changing, so we ended up with some messed up text issues in it).
(this screenshot is special because I took the screenshot as the text above the file path was changing, so we ended up with some messed up text issues in it).

Once the installer has completed, you can click Finish on it to close it. Usually, if I was executing a sample which is not a installer and wanted to monitor the registry I would do it during the execution (few minutes) as a quick check, and do the last compare when the process exits.
Now, go back to Regshot. Take your '2nd shot' of the registry.
Let Regshot work and take the shot.
Once it has completed taking the second shot, the Compare button should be enabled. Click it.
After it has finished comparing the 2 shots, it will open up a text file (with your default text editor, usually Window Notepad application) with the list of changes. You can view some more screenshots in the following spoiler:

At the very end of the text file, we receive a calculation of the total changes. In this case, it's 42399 changes:

If you were unsure on actually using the tool with a sample even after the normal tutorial, hopefully this reassured you on using this tool. Of course, any issues/questions, put them below. I or another fellow member of this community will be there to help you.
Credits to @.com, the sample was taken from one of his threads off the Malware Hub. You can view the original thread here: http://malwaretips.com/threads/bundlore-graftor-10-02-2015.42071/
Cheers.
The purpose of this thread is dedicated to monitoring the Registry. In this thread I will be using a tool known as Regshot, which can be downloaded from the following URL:
To learn to use Regshot, please open up the following SPOILER:
Before we start using Regshot, I should probably first explain what Regshot will help you with during Malware Analysis, and what it does.
Regshot is a tool which will allow you to create logs (in other words of the program, “shots”) of your registry. The use for this is to take a shot before executing a malware sample, and then to take another shot afterwards (or after a certain time duration of executing a sample). You can them compare the two logs (“shots”) to check the registry keys which have been created, deleted, changed.
It can be very useful during malware analysis. If you ever have a malware sample you wish to upload onto the Malware Hub, you could be more helpful by using your analysis skills to analyse the sample and created a report on the post. This is optional of course, however if you did, you could include registry change information.
Anyway, let’s continue to learning how to use the tool.
After you have extracted the ZIP containing Regshot to a folder, you should have 9 items in the folder, and those items should be like in the following screenshot I have taken for you:
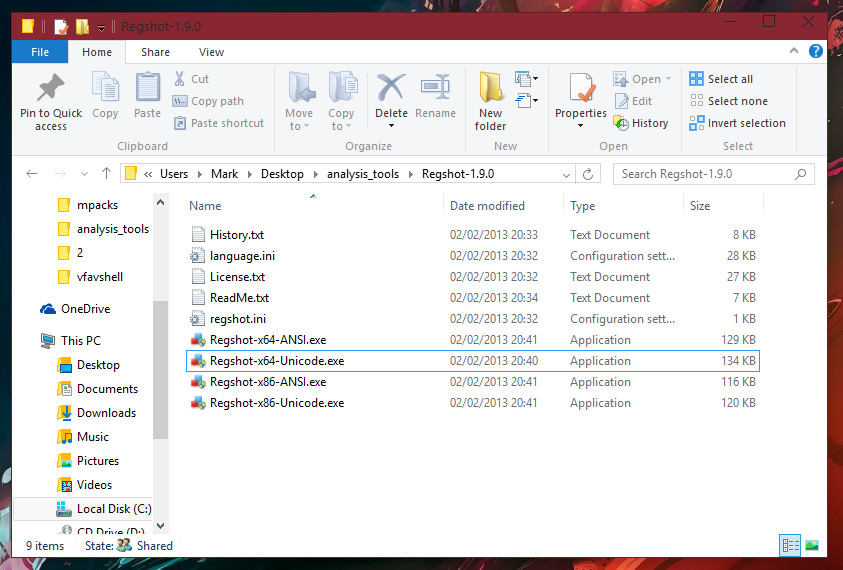
Depending on whether you are a 32-bit (x86) or 64-bit user (x64) you will need to open the different executable file to launch Regshot. Because I am an x64 user, I will open up Regshot-x64-Unicode.exe.
Once the program has opened, it should look like the following screenshot:
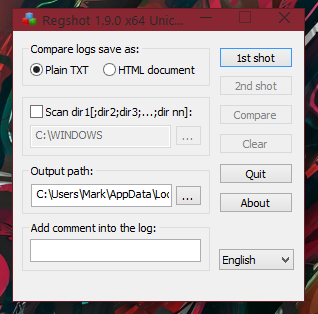
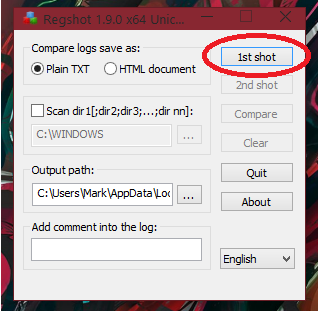
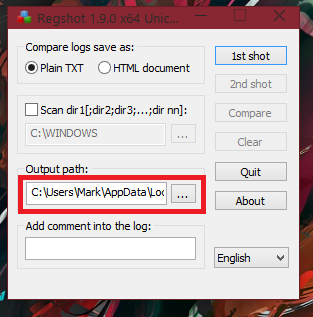
To start off before you open up a malware sample, (or any sample you are analysing because you won’t necessarily know if it’s malicious or not until after analysing it, in the case of a submission which is FUD), you must first take your 1st shot. You can accomplish this of course by clicking the 1st shot button, shown in the below image:
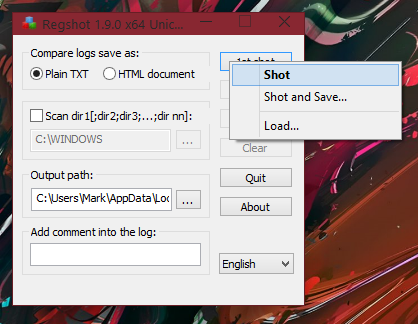
You should receive a dropdown menu after clicking this, displaying items to “Shot”, “Shot and Save…” and “Load…”. If you select “Shot”, the default location for the log report will be in the “Output path”, which for me is:C:\Users\Mark\AppData\Local\Temp\ (of course you can change the output path if you’d like, for easy access this may be a folder on the Desktop, for example).
Once your first shot has been created you can execute your sample. Once you are ready, take the second shot, and then click on Compare.
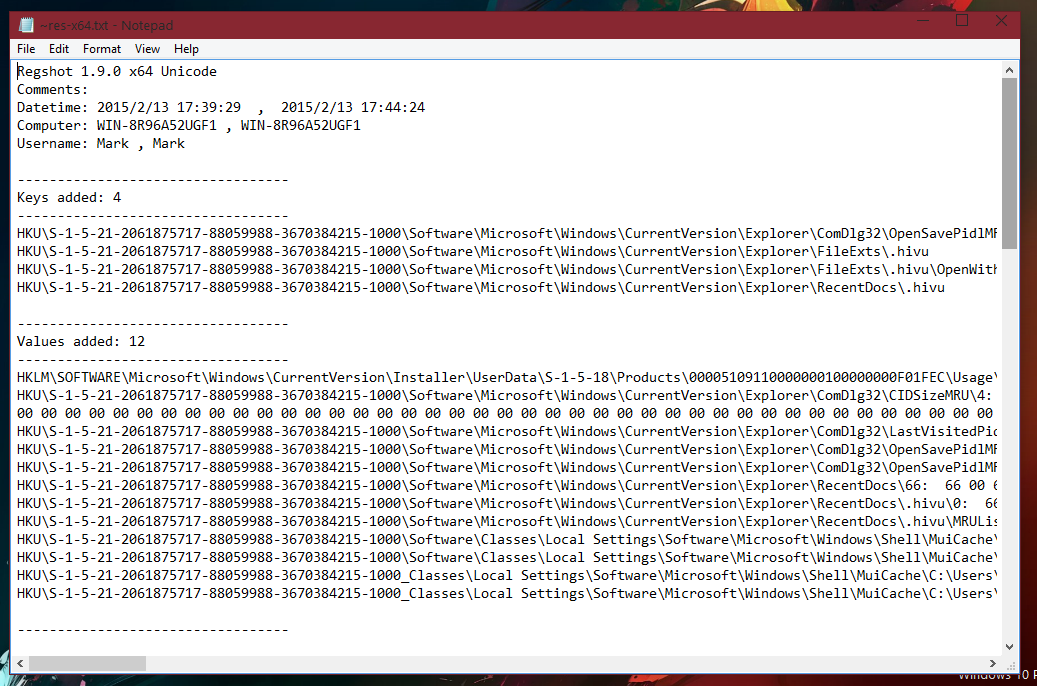
Once the Compare process has completed, the log will be executed into the text editor. This will be notepad for me, in this case.
The log for me includes Keys added, Values added, Values modified. At the bottom is a integer value corresponding to the total amount of changes.
The rest of the screenshots are provided below:
As you can see, this tool is very useful.
Regshot is a tool which will allow you to create logs (in other words of the program, “shots”) of your registry. The use for this is to take a shot before executing a malware sample, and then to take another shot afterwards (or after a certain time duration of executing a sample). You can them compare the two logs (“shots”) to check the registry keys which have been created, deleted, changed.
It can be very useful during malware analysis. If you ever have a malware sample you wish to upload onto the Malware Hub, you could be more helpful by using your analysis skills to analyse the sample and created a report on the post. This is optional of course, however if you did, you could include registry change information.
Anyway, let’s continue to learning how to use the tool.
After you have extracted the ZIP containing Regshot to a folder, you should have 9 items in the folder, and those items should be like in the following screenshot I have taken for you:

Depending on whether you are a 32-bit (x86) or 64-bit user (x64) you will need to open the different executable file to launch Regshot. Because I am an x64 user, I will open up Regshot-x64-Unicode.exe.
Once the program has opened, it should look like the following screenshot:

To start off before you open up a malware sample, (or any sample you are analysing because you won’t necessarily know if it’s malicious or not until after analysing it, in the case of a submission which is FUD), you must first take your 1st shot. You can accomplish this of course by clicking the 1st shot button, shown in the below image:

You should receive a dropdown menu after clicking this, displaying items to “Shot”, “Shot and Save…” and “Load…”. If you select “Shot”, the default location for the log report will be in the “Output path”, which for me is:C:\Users\Mark\AppData\Local\Temp\ (of course you can change the output path if you’d like, for easy access this may be a folder on the Desktop, for example).
Once your first shot has been created you can execute your sample. Once you are ready, take the second shot, and then click on Compare.
Once the Compare process has completed, the log will be executed into the text editor. This will be notepad for me, in this case.
The log for me includes Keys added, Values added, Values modified. At the bottom is a integer value corresponding to the total amount of changes.
The rest of the screenshots are provided below:



As you can see, this tool is very useful.
If anyone else has a better tool for monitoring the Registry changes during Malware Analysis, feel free to post them in the comments. As long as it works as intended and does the job, there shouldn't be an issue with using another tool.
Anyway, time we got started at using Regshot to monitor the Registry with a sample.
WARNING: PLEASE USE A VIRTUAL MACHINE. DO NOT ATTEMPT TO CONTINUE ON YOUR MAIN SYSTEM.
To start off, download the sample (the download URL is attached to the top of this thread, the password to the archieve is also supplied underneath the download URL at the top of this thread).
Once the archieve is downloaded, extract the archieve to the Desktop.
Now, open up Regshot (with Administrative rights). It should look like this:

We will start by making our 1st shot before we execute the sample. Please take your 1st shot.
After you have taken your 1st shot, it's time to execute the sample!
Navigate to where you saved the sample... And execute it. [when I say "execute", I am referring to "opening". So when I say "execute it", I mean "open it". Just thought I'd get that out the way].
The installer will load. Wait for it, let it install. If you would like to view some screenshots I took during the installation process, you can view them in the following spoiler:






Once the installer has completed, you can click Finish on it to close it. Usually, if I was executing a sample which is not a installer and wanted to monitor the registry I would do it during the execution (few minutes) as a quick check, and do the last compare when the process exits.
Now, go back to Regshot. Take your '2nd shot' of the registry.
Let Regshot work and take the shot.
Once it has completed taking the second shot, the Compare button should be enabled. Click it.
After it has finished comparing the 2 shots, it will open up a text file (with your default text editor, usually Window Notepad application) with the list of changes. You can view some more screenshots in the following spoiler:

At the very end of the text file, we receive a calculation of the total changes. In this case, it's 42399 changes:

If you were unsure on actually using the tool with a sample even after the normal tutorial, hopefully this reassured you on using this tool. Of course, any issues/questions, put them below. I or another fellow member of this community will be there to help you.
Credits to @.com, the sample was taken from one of his threads off the Malware Hub. You can view the original thread here: http://malwaretips.com/threads/bundlore-graftor-10-02-2015.42071/
Cheers.
Last edited by a moderator: