- Jan 22, 2014
- 577
Project details : MRG Effitas 360 Assessment & Certification Q4 2015
Tests Employed
In this assessment (Q4 2015), we ran the following tests:
In the Wild 360 / Full Spectrum Test
Testing was conducted as per the methodology detailed in Appendix 1. In total, 507 live ITW samples were used.
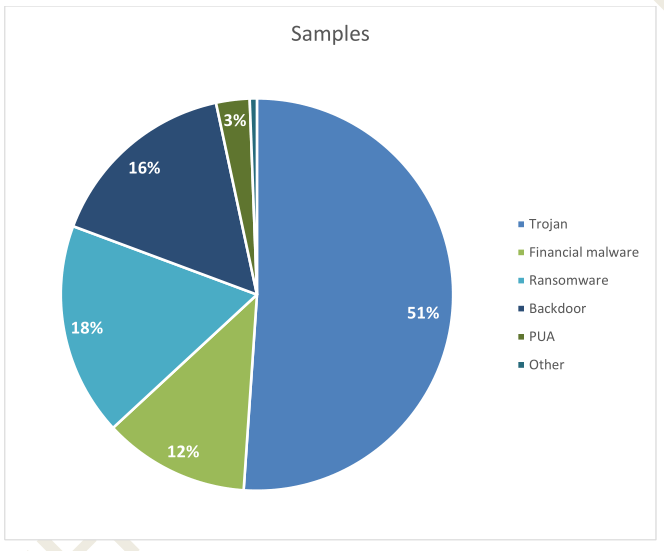
The stimulus load was comprised of the following: 259 trojans, 81 backdoors, 61 financial malware samples, 89 ransomware samples, 14 PUAs, and 3 other.
Security Applications Tested
(Last program build used in the project)
Test Results
The tables below show the results of testing under the MRG Effitas 360 Q4 Assessment Programme.
More information on source url.
- 16 applications tested
- 507 In-the-Wild malware samples used
- Operating System: Windows 8.1 x64
- Browser: Internet Explorer
- Real World scenario with no user initiated threat neutralization
Tests Employed
In this assessment (Q4 2015), we ran the following tests:
In the Wild 360 / Full Spectrum Test
Testing was conducted as per the methodology detailed in Appendix 1. In total, 507 live ITW samples were used.
The stimulus load was comprised of the following: 259 trojans, 81 backdoors, 61 financial malware samples, 89 ransomware samples, 14 PUAs, and 3 other.
Security Applications Tested
(Last program build used in the project)
- avast Internet Security 11.1.2245
- AVG Internet Security 2016 16.0 Build 7294
- Avira Internet Security 2016 15.0.15.129
- BitDefender Internet Security 2016 20.0.24.1290
- ESET Smart Security 9.0.363
- Intel McAfee Internet Security 2015 18.0
- Kaspersky Internet Security 16.0.0.614(d)
- Malwarebytes Anti-Malware 2.2.0.1024
- Microsoft Windows Defender
- Panda Internet Security 2016 16.1.0
- SurfRight HitmanPro 3.7.12 - Build 253
- Symantec Norton Security 2015 22.5.4.24
- ThreatTrack VIPRE Internet Security 2016 9.0.1.4
- Trend Micro Internet Security 2016 10.0.0.1150
- Webroot SecureAnywhere Internet Security 9.0.7.46
- Zemana Anti-Malware 2.19.2.797
Test Results
The tables below show the results of testing under the MRG Effitas 360 Q4 Assessment Programme.
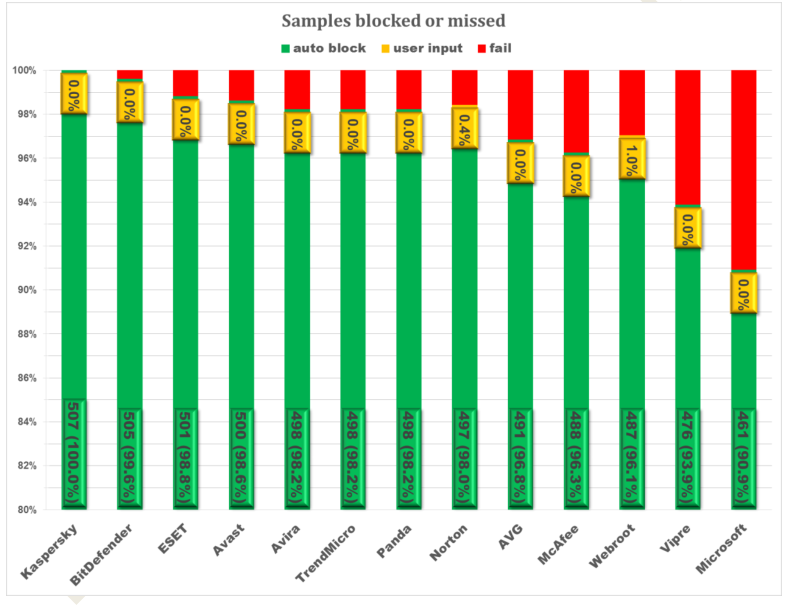
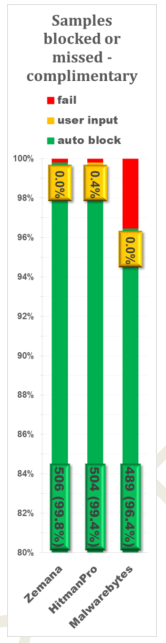
Q4 2015 In the Wild 360 / Full Spectrum Test Results
Q4 2015 Time to Detect & Remediate Test
Q4 2015 Time to Detect & Remediate Test
Understanding Grade of Pass:
- Level 1 = All threats detected on first exposure / system uncompromised.
- Kaspersky Internet Security
- Level 2 = All threats detected and neutralised / system remediated before or on the first user reboot
- Bitdefender Internet Security
- ESET SmartSecurity
- Webroot SecureAnywhere Internet Security Plus
- SurfRight HitmanPro *
- Zemana Anti-Malware
- Failed = Security product failed to detect all infections and remediate the system during the test procedure.
- avast! Internet Security
- AVG Internet Security
- Avira Internet Security
- Malwarebytes Anti-Malware
- McAfee Internet Security
- Microsoft Security Essentials
- Panda Internet Security
- Symantec Norton Security
- ThreatTrack VIPRE Internet Security
- Trend Micro Premium Security