- Aug 17, 2017
- 1,280
- 17,222
- 2,568
While the nation-state group has previously employed ScreenConnect, RemoteUtilities, and Syncro, a new analysis from Group-IB has revealed the adversary's use of the SimpleHelp remote support software in June 2022. MuddyWater, active since at least 2017, is assessed to be a subordinate element within Iran's Ministry of Intelligence and Security (MOIS). Some of the top targets include Turkey, Pakistan, the U.A.E., Iraq, Israel, Saudi Arabia, Jordan, the U.S., Azerbaijan, and Afghanistan."MuddyWater uses SimpleHelp, a legitimate remote device control and management tool, to ensure persistence on victim devices," Nikita Rostovtsev, senior threat analyst at Group-IB said."SimpleHelp is not compromised and is used as intended. The threat actors found a way to download the tool from the official website and use it in their attacks."
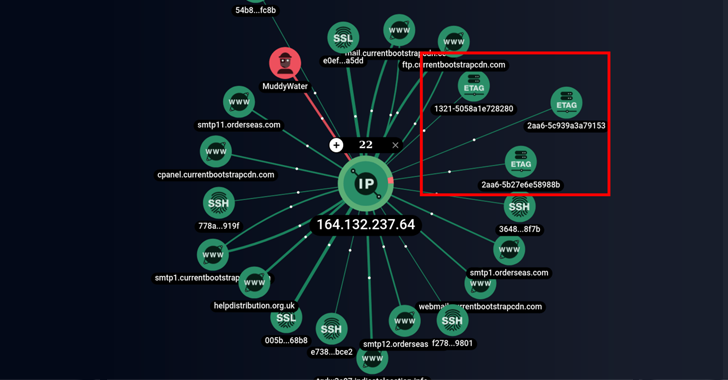
Iranian Hackers Using SimpleHelp Remote Support Software for Persistent Access
Iranian MuddyWater hacker group has been found using the legitimate SimpleHelp remote support software to maintain persistence on victim devices.