Cisco Talos has been tracking a new campaign involving the FormBook malware since May 2018 that utilizes four different malicious documents in a single phishing email. FormBook is an inexpensive stealer available as "malware as a service." This means an attacker can purchase a compiled piece of malware based on their desired parameters. This is commonplace with crimeware and stealer type malware such as FormBook. It is able to record keystrokes, steal passwords (stored locally and in web forms) and can take screenshots.
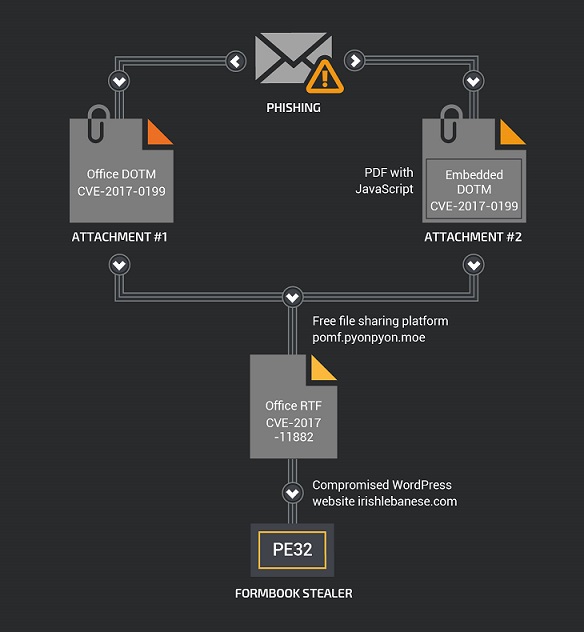
The author put a lot of effort in the infection vector using multiple malicious documents in a single phishing email. The author also mixed different file formats (PDF and Microsoft Office document) and used two public Microsoft Office exploits (CVE-2017-0199 and CVE-2017-11882) in order to drop the final payload on the targeted system. The final payload was downloaded during the campaign from a small Japanese file-sharing platform. The platform owner has since deleted the malicious payload binaries from their system.
We identified an infrastructure overlap between this campaign and a previous campaign we published in February 2017 relating to Pony malware which utilized Microsoft Publisher files to deliver its payload. There is the potential that the same actor behind these two attacks is the same due to an overlap in the two attacks' infrastructure. If that is the case, the actor could switch between Pony and FormBook to be able to continue their malicious activities for more than a year.