- Jan 24, 2011
- 9,378
Russian security vendor Kaspersky Lab, who assisted with the official police investigation, confirmed today that the cyber-crime syndicate that developed the Lurk banking trojan was also the team that developed the Angler exploit kit (EK), the world's most popular crimeware kit at the time of its demise.
At the end of May, Russian authorities announced they arrested 50 people, detaining 18, for their involvement in the distribution of the Lurk banking trojan, which was used to steal more than $45 million (3 billion rubles) from Russian banks and other financial companies since 2011.
Lurk had a huge impact on banking software worldwide
The trojan, which initially targeted RBS (Remote Banking Software) used in Russian banks, had a huge impact on the financial market in Russia and all over the globe.
Two years after it appeared on the scene, along with other RBS-targeting malware like the one developed by the Carberp gang, banks, and RBS software vendors introduced several security measures in the money transferring process worldwide.
RBS software vendors stopped offering free demos of their product, while banks added two-step verification and off-site authentication codes.
Angler EK appeared when profits from Lurk died down
These changes happened in 2013, about the same time Kaspersky and other security vendors can track down the first versions of Angler.
Kaspersky's experts put forward the theory that the Lurk gang, which was operating a huge crew of malware developers, money mules, spammers, and others, had to find another stream of revenue to pay their employees.
As such, the team decided to open a part of their infrastructure to other criminal groups. Until that moment, the Lurk gang kept the tools it developed only for its own operations.
What they decided to make available for rent was their toolkit used to serve malware via drive-by downloads. This toolkit was later named Angler by the security firms that analyzed it.
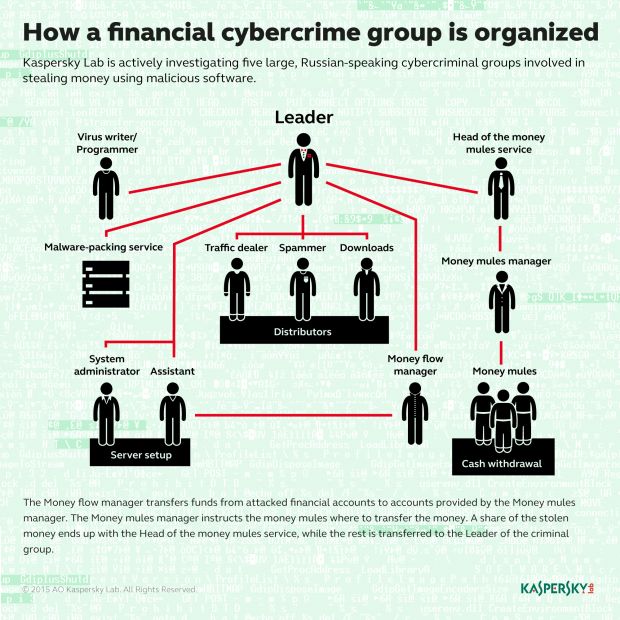
The anatomy of a cyber-crime gang
Read more: Mystery Solved: Angler Exploit Kit Was Developed by Now-Arrested Lurk Gang
At the end of May, Russian authorities announced they arrested 50 people, detaining 18, for their involvement in the distribution of the Lurk banking trojan, which was used to steal more than $45 million (3 billion rubles) from Russian banks and other financial companies since 2011.
Lurk had a huge impact on banking software worldwide
The trojan, which initially targeted RBS (Remote Banking Software) used in Russian banks, had a huge impact on the financial market in Russia and all over the globe.
Two years after it appeared on the scene, along with other RBS-targeting malware like the one developed by the Carberp gang, banks, and RBS software vendors introduced several security measures in the money transferring process worldwide.
RBS software vendors stopped offering free demos of their product, while banks added two-step verification and off-site authentication codes.
Angler EK appeared when profits from Lurk died down
These changes happened in 2013, about the same time Kaspersky and other security vendors can track down the first versions of Angler.
Kaspersky's experts put forward the theory that the Lurk gang, which was operating a huge crew of malware developers, money mules, spammers, and others, had to find another stream of revenue to pay their employees.
As such, the team decided to open a part of their infrastructure to other criminal groups. Until that moment, the Lurk gang kept the tools it developed only for its own operations.
What they decided to make available for rent was their toolkit used to serve malware via drive-by downloads. This toolkit was later named Angler by the security firms that analyzed it.
The anatomy of a cyber-crime gang
Read more: Mystery Solved: Angler Exploit Kit Was Developed by Now-Arrested Lurk Gang