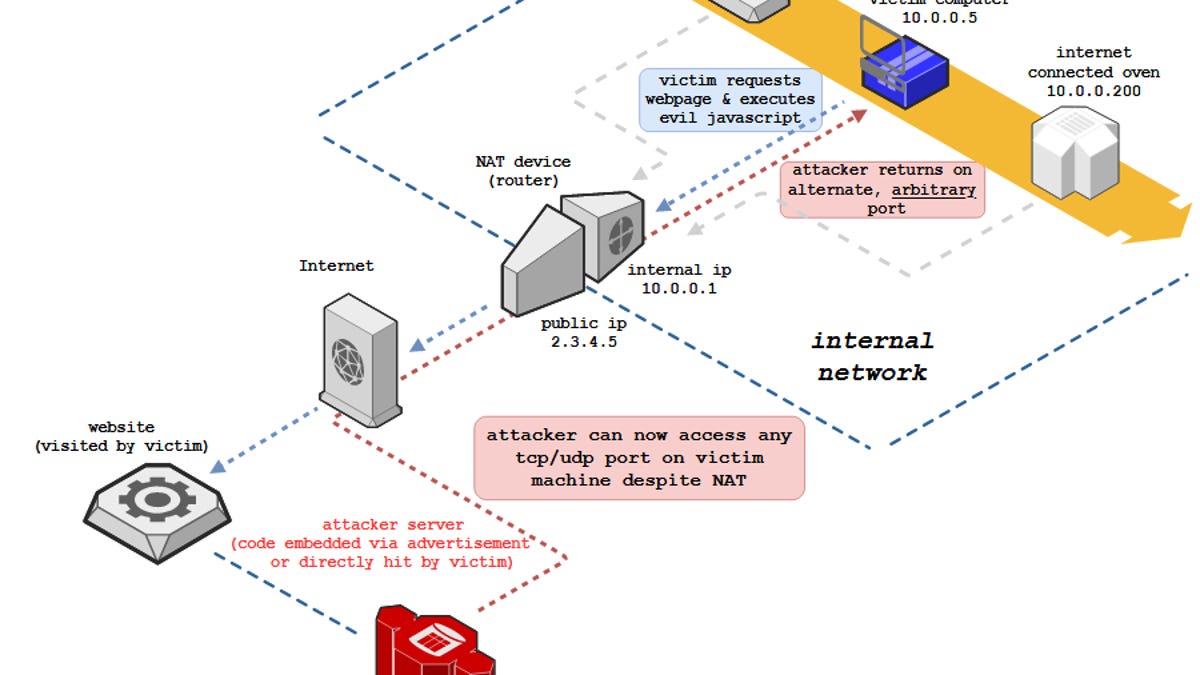
The original NAT Slipstream potentially allowed a miscreant to access any TCP/UDP service tied to a victim's machine by bypassing the victim's NAT (Network Address Translation) and firewall defenses. It can be triggered via JavaScript code on a malicious website.
NAT Slipstream v2 takes the technique further by allowing a hacker to penetrate a vulnerable NAT/firewall and reach any internal IP on the network, rather than just the IP address of the victim's device. In other words, it may expose every connected thing on a targeted network – printers, video cameras, industrial control systems, and other unmanaged hardware – to the internet. Such devices, which generally lack security controls, may then be compromised and commandeered or otherwise abused.
The researchers disclosed their findings to the major browser vendors back in November 2020, and patches, consisting of port restrictions, have been deployed since then.

Knock, knock. Who's there? NAT. Nat who? A NAT URL-borne killer
Last year's slipstream technique revived to pierce vulnerable firewalls – browsers patched to thwart bypass attempts