Gandalf_The_Grey
Level 83
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Apr 24, 2016
- 7,260
Dutch article translated by DeepL:
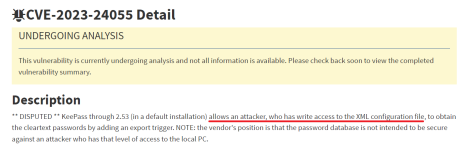
The Ministry of Justice and Security's National Cyber Security Center (NCSC) is warning of a vulnerability in password manager KeePass that would allow an attacker who already has access to a system to obtain data in the KeePass database, such as passwords. The developer states that this is not a vulnerability and KeePass' password database is not designed to protect against an attacker with such access to the system. Accordingly, no security update will be released.
A proof-of-concept exploit that allows a local attacker to obtain the contents of the KeePass database has appeared online. The security flaw is caused by KeePass' configuration being stored unencrypted. A local attacker can modify this configuration and add a rogue export rule. When a user opens a KeePass database, the export rule causes stored data to be exported to the attacker undetected.
According to the NCSC, system administrators can still prevent abuse through an Enforced Configuration. "Setting the ExportNoKey parameter to false ensures that a master password is required for exporting stored data. This prevents a malicious party from surreptitiously exporting sensitive data," the NCSC said.
The government agency advises organizations to use an Enforced Configuration and implement at least the above configuration. In addition, organizations are advised to perform risk assessment before using KeePass. The vulnerability in KeePass is designated as CVE-2023-24055, but has been disputed by the developer.