- Aug 17, 2014
- 11,108
Unidentified threat actors have deployed a new backdoor that borrows its features from the U.S. Central Intelligence Agency (CIA)'s Hive multi-platform malware suite, the source code of which was released by WikiLeaks in November 2017.
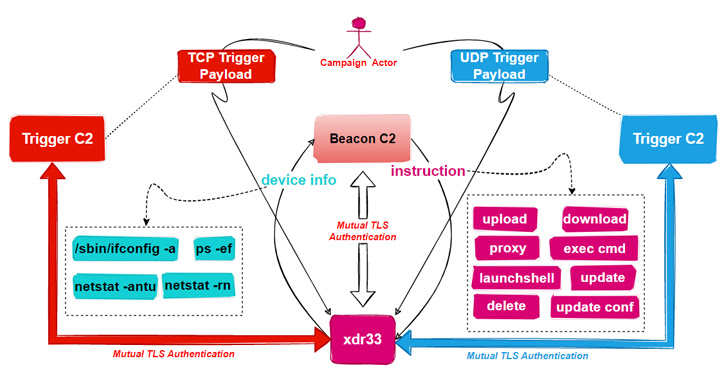
"This is the first time we caught a variant of the CIA Hive attack kit in the wild, and we named it xdr33 based on its embedded Bot-side certificate CN=xdr33," Qihoo Netlab 360's Alex Turing and Hui Wang said in a technical write-up published last week.
xdr33 is said to be propagated by exploiting a security vulnerability in the F5 appliance and communicating with a command-and-control (C2) server using SSL with forged Kaspersky certificates.
The intent of the backdoor, per the Chinese cybersecurity firm, is to harvest sensitive information and act as a launchpad for subsequent intrusions. It improves upon Hive by adding new C2 instructions and functionalities, among other implementation changes.
The ELF sample further operates as a Beacon by periodically exfiltrating system metadata to the remote server and executing commands issued by the C2.
New Backdoor Created Using Leaked CIA's Hive Malware Discovered in the Wild
A new backdoor has been discovered that borrows its features from the leaked CIA's Hive malware suite.

