A new malware family called Trojan.sysscan has the potential to wreak havoc in enterprise networks that feature poorly protected RDP servers.
Discovered by security firm Guardicore, attackers utilize this malware as a backdoor trojan, collecting data from compromised hosts, and exfiltrating it to an attacker's remote server.
Attacker infects systems after RDP brute-force attacks
Targeted systems are infected after the attacker scans the Internet for open RDP ports, which he brute-forces using common username and password combinations.
Poorly secured servers are the optimal targets, and because RDP servers are commonly found in medium-to-large enterprise networks, companies have the most to fear from this new threat.
According to Guardicore, this new trojan is coded in the Delphi programming language and comes with support for dumping passwords from locally installed applications such as browsers, databases, and PoS software.
The trojan contains specific functions to target credentials used for accounts on banking, gambling and tax websites. It will also target and steal browser cookie files.
Discovered by security firm Guardicore, attackers utilize this malware as a backdoor trojan, collecting data from compromised hosts, and exfiltrating it to an attacker's remote server.
Attacker infects systems after RDP brute-force attacks
Targeted systems are infected after the attacker scans the Internet for open RDP ports, which he brute-forces using common username and password combinations.
Poorly secured servers are the optimal targets, and because RDP servers are commonly found in medium-to-large enterprise networks, companies have the most to fear from this new threat.
According to Guardicore, this new trojan is coded in the Delphi programming language and comes with support for dumping passwords from locally installed applications such as browsers, databases, and PoS software.
The trojan contains specific functions to target credentials used for accounts on banking, gambling and tax websites. It will also target and steal browser cookie files.
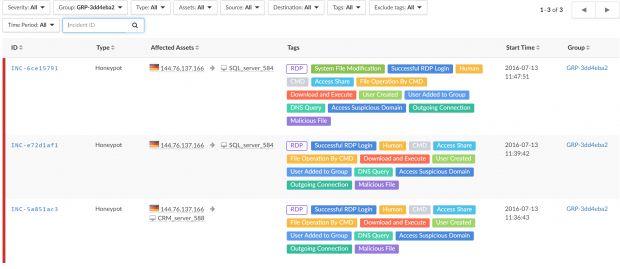
Two IP addresses used in recent attacks
The trojan sets up a hidden administrator account on compromised systems in order to gain boot persistence and makes sure to leave the RDP open for future connections.
Guardicore says Trojan.sysscan contains code to search and identify when the trojan is executed in sandbox environments and virtual machines. Nevertheless, the trojan only detects the presence of these environments and fails to take any action to stop execution or hide its activity.
The data the trojan collects is sent via an unencrypted HTTP request to a remote server. If the transfer fails, often times, the attacker logs in via RDP and copies the data manually.
Security experts say that during this recent wave of Trojan.sysscan attacks, the threat actor behind the malware has used two IPs: 85.93.5.43 (UAE) to store the stolen data, and 144.76.137.166 (Germany) to scan for open RDP ports.