silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,743
- 123,908
- 8,399
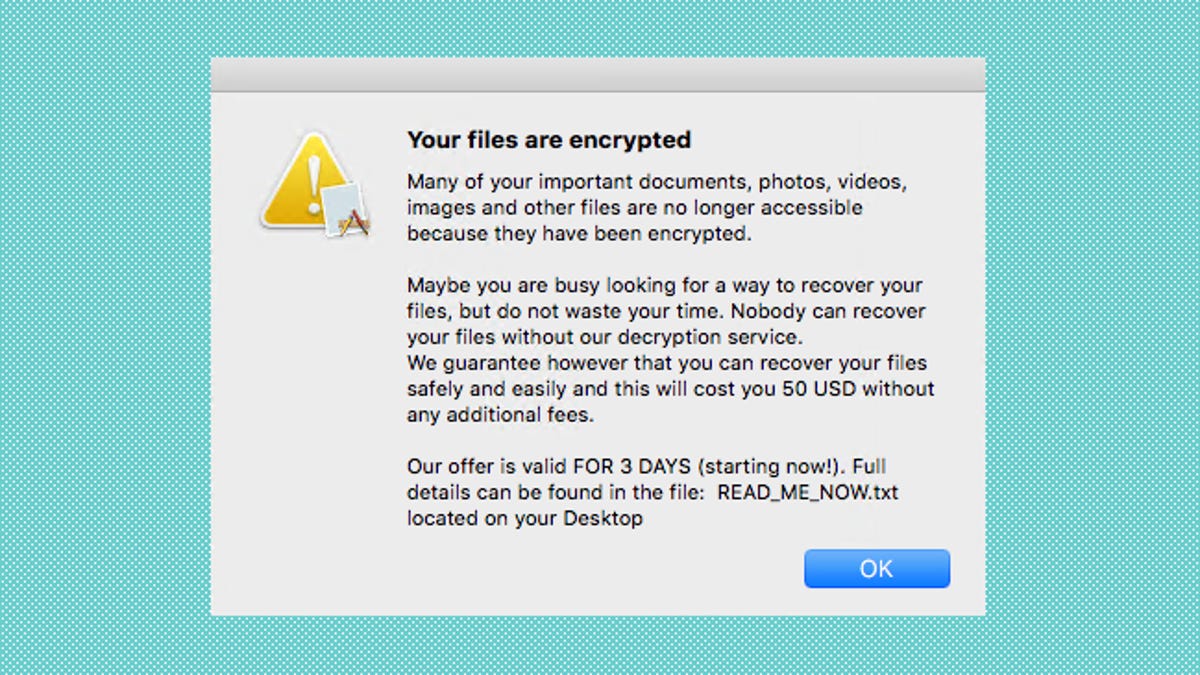
Security researchers have discovered this week a new ransomware strain targeting macOS users.
Named OSX.EvilQuest, this ransomware is different from previous macOS ransomware threats because besides encrypting the victim's files, EvilQuest also installs a keylogger, a reverse shell, and steals cryptocurrency wallet-related files from infected hosts.
"Armed with these capabilities, the attacker can main full control over an infected host," said Patrick Wardle, Principal Security Researcher at Jamf. This means that even if victims paid, the attacker would still have access to their computer and continue to steal files and keyboard strokes. Wardle is currently one of the many macOS security researchers who are analyzing this new threat.
Others who are also investigating EvilQuest include Thomas Reed, Director of Mac & Mobile at Malwarebytes, and Phil Stokes, macOS security researcher at SentinelOne. Reed and Stokes are currently looking for a weakness or bug in the ransomware's encryption scheme that could be exploited to create a decryptor and help infected victims recover their files without paying the ransom.
But the researcher who first spotted the new EvilQuest ransomware is K7 Lab security researcher Dinesh Devadoss. Devadoss tweeted about his finding yesterday, June 29. However, new evidence surfaced in the meantime has revealed that EvilQuest has been, in reality, distributed in the wild since the start of June 2020.