- Jul 22, 2014
- 2,525
Bad news. Even worse news if you're in China...
16 Mar 2016 at 14:51, John Leyden
Miscreants have forged a strain of iOS malware which poses a greater risk than previous nasties because it can infect non-jailbroken devices without the user’s confirmation.
AceDeceiver is fundamentally different from recent iOS malware because it relies in exploiting flaws in Apple’s DRM software rather than abusing enterprise certificates, a common trick in iOS malware over the past two years or so.
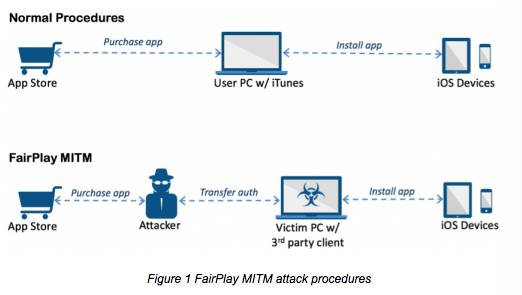
FairPlay MitM diddle: No certs required
AceDeceiver is the first iOS malware that exploits flaws in FairPlay, Apple’s DRM protection system to install malicious apps on iOS devices regardless of whether or not they are jailbroken.
Even though Apple has removed AceDeceiver from its App store, the malware can still spread, security researchers at Palo Alto Networks warn.
Malicious apps only need to have been available in the App Store once to spread, simply requiring the victim to install the client to his or her PC. After that, infection of iOS devices is completed in the background without the user’s awareness with the only indication being a new icon on the home screen that the user won’t recall downloading.
The hacking technique used by AceDeceiver, called “FairPlay Man-In-The-Middle (MITM)”, has been used to spread pirated iOS apps since 2013 but this is the first time it’s been used to spread malware.
Three different iOS apps in the AceDeceiver family were uploaded to the official App Store between July 2015 and February 2016, each claiming to be wallpaper apps. These apps successfully bypassed Apple’s code review at least seven times, according to Palo Alto. The success of AceDeceiver provides evidence that hackers have developed techniques to bypass Apple’s code review process and get malicious apps into the App Store.
AceDeceiver only displays malicious behaviours when a user is located in China, but this is likely to change over time.
Palo Alto Networks’ write-up of the AceDeceiver threat can be found in a blog post here. ®
16 Mar 2016 at 14:51, John Leyden
Miscreants have forged a strain of iOS malware which poses a greater risk than previous nasties because it can infect non-jailbroken devices without the user’s confirmation.
AceDeceiver is fundamentally different from recent iOS malware because it relies in exploiting flaws in Apple’s DRM software rather than abusing enterprise certificates, a common trick in iOS malware over the past two years or so.

FairPlay MitM diddle: No certs required
AceDeceiver is the first iOS malware that exploits flaws in FairPlay, Apple’s DRM protection system to install malicious apps on iOS devices regardless of whether or not they are jailbroken.
Even though Apple has removed AceDeceiver from its App store, the malware can still spread, security researchers at Palo Alto Networks warn.
Malicious apps only need to have been available in the App Store once to spread, simply requiring the victim to install the client to his or her PC. After that, infection of iOS devices is completed in the background without the user’s awareness with the only indication being a new icon on the home screen that the user won’t recall downloading.
The hacking technique used by AceDeceiver, called “FairPlay Man-In-The-Middle (MITM)”, has been used to spread pirated iOS apps since 2013 but this is the first time it’s been used to spread malware.
Three different iOS apps in the AceDeceiver family were uploaded to the official App Store between July 2015 and February 2016, each claiming to be wallpaper apps. These apps successfully bypassed Apple’s code review at least seven times, according to Palo Alto. The success of AceDeceiver provides evidence that hackers have developed techniques to bypass Apple’s code review process and get malicious apps into the App Store.
AceDeceiver only displays malicious behaviours when a user is located in China, but this is likely to change over time.
Palo Alto Networks’ write-up of the AceDeceiver threat can be found in a blog post here. ®