- Aug 17, 2014
- 11,111
Users searching for popular software are being targeted by a new malvertising campaign that abuses Google Ads to serve trojanized variants that deploy malware, such as Raccoon Stealer and Vidar.
The activity makes use of seemingly credible websites with typosquatted domain names that are surfaced on top of Google search results in the form of malicious ads by hijacking searches for specific keywords.
The ultimate objective of such attacks is to trick unsuspecting users into downloading malevolent programs or potentially unwanted applications.
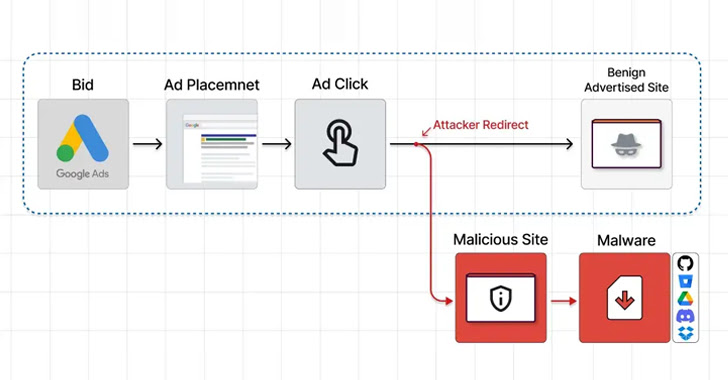
In one campaign disclosed by Guardio Labs, threat actors have been observed creating a network of benign sites that are promoted on the search engine, which when clicked, redirect the visitors to a phishing page containing a trojanized ZIP archive hosted on Dropbox or OneDrive.
"The moment those 'disguised' sites are being visited by targeted visitors (those who actually click on the promoted search result) the server immediately redirects them to the rogue site and from there to the malicious payload," researcher Nati Tal said.
Among the impersonated software include AnyDesk, Dashlane, Grammarly, Malwarebytes, Microsoft Visual Studio, MSI Afterburner, Slack, and Zoom, among others.
New Malvertising Campaign via Google Ads Targets Users Searching for Popular Software
A new malvertising campaign has been discovered that targets people searching for popular software. This campaign uses Google Ads to spread trojans.