- Aug 17, 2014
- 11,115
The Sharp Panda cyber-espionage hacking group is targeting high-profile government entities in Vietnam, Thailand, and Indonesia with a new version of the ‘Soul’ malware framework.
The particular malware was previously seen in espionage campaigns targeting critical Southeast Asian organizations, attributed to various Chinese APTs.
Check Point identified a new campaign using the malware that started in late 2022 and continues through 2023, employing spear-phishing attacks for initial compromise.
The use of the RoyalRoad RTF kit, C2 server addresses, and the hacker's working hours allowed Check Point to attribute the latest espionage operation to state-backed Chinese hackers. The TTPs and tools are consistent with previously seen activities by Sharp Panda.
The new Sharp Panda campaign uses spear-phishing emails with malicious DOCX file attachments that deploy the RoyalRoad RTF kit to attempt to exploit older vulnerabilities to drop malware on the host.
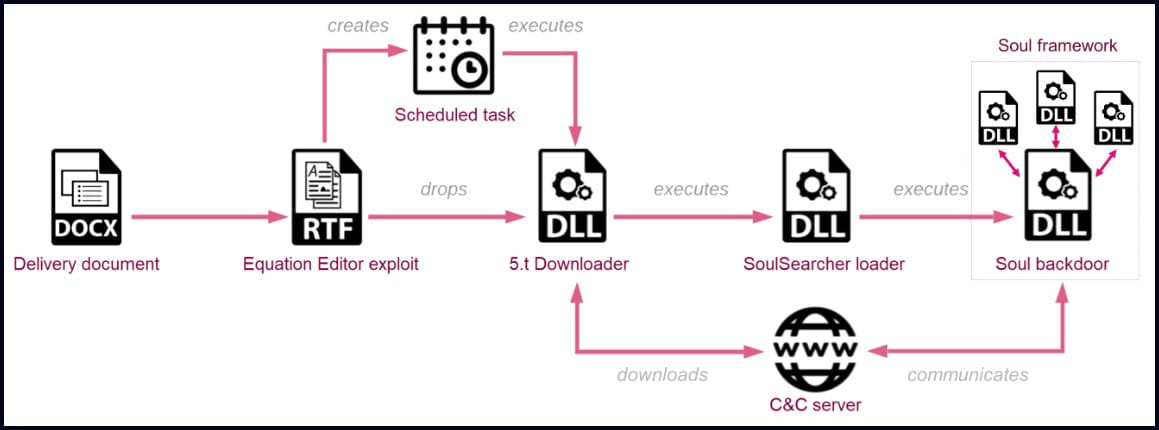
Infection chain (Check Point)

New malware variant has “radio silence” mode to evade detection
The Sharp Panda cyber-espionage hacking group was observed targeting high-profile government entities in Vietnam, Thailand, and Indonesia, using a new version of the 'Soul' malware framework.