Hello everyone,
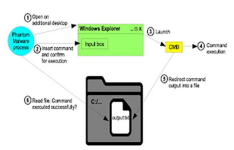
I want to raise your attention to an architectonic vulnerability in the graphical user interfaces of Windows, macOS and Linux. A powerful malware obfucation technique can be developed based on this vulnerability which is building block of a new malware type – Phantom Malware.
Metaphorically speaking, Phantom Malware is an additional hidden user “who” is acting currently with the “real” user (human).
For example, Phantom Ransomware: The user encrypts its own files...
Unfortunately, state of the art malware detection techniques are unable to detect the new malware type. Due to these techniques do not consider that the malware is able to interact with the graphical user interface.
Here is the link: Phantom Malware: Conceal Malicious Actions From Malware Detection Techniques by Imitating User Activity
It shows a new dimension of attack vectors: Instead of exploiting vulnerabilities of a program (e.g. Buffer Overflow), the design of a user interface is exploited for reaching an arbitrary code execution as trusted system user.
What do you think about that?
I want to raise your attention to an architectonic vulnerability in the graphical user interfaces of Windows, macOS and Linux. A powerful malware obfucation technique can be developed based on this vulnerability which is building block of a new malware type – Phantom Malware.
Metaphorically speaking, Phantom Malware is an additional hidden user “who” is acting currently with the “real” user (human).
For example, Phantom Ransomware: The user encrypts its own files...
Unfortunately, state of the art malware detection techniques are unable to detect the new malware type. Due to these techniques do not consider that the malware is able to interact with the graphical user interface.
Here is the link: Phantom Malware: Conceal Malicious Actions From Malware Detection Techniques by Imitating User Activity
It shows a new dimension of attack vectors: Instead of exploiting vulnerabilities of a program (e.g. Buffer Overflow), the design of a user interface is exploited for reaching an arbitrary code execution as trusted system user.
What do you think about that?