- Nov 10, 2017
- 3,135
- 1
- 22,994
- 4,269
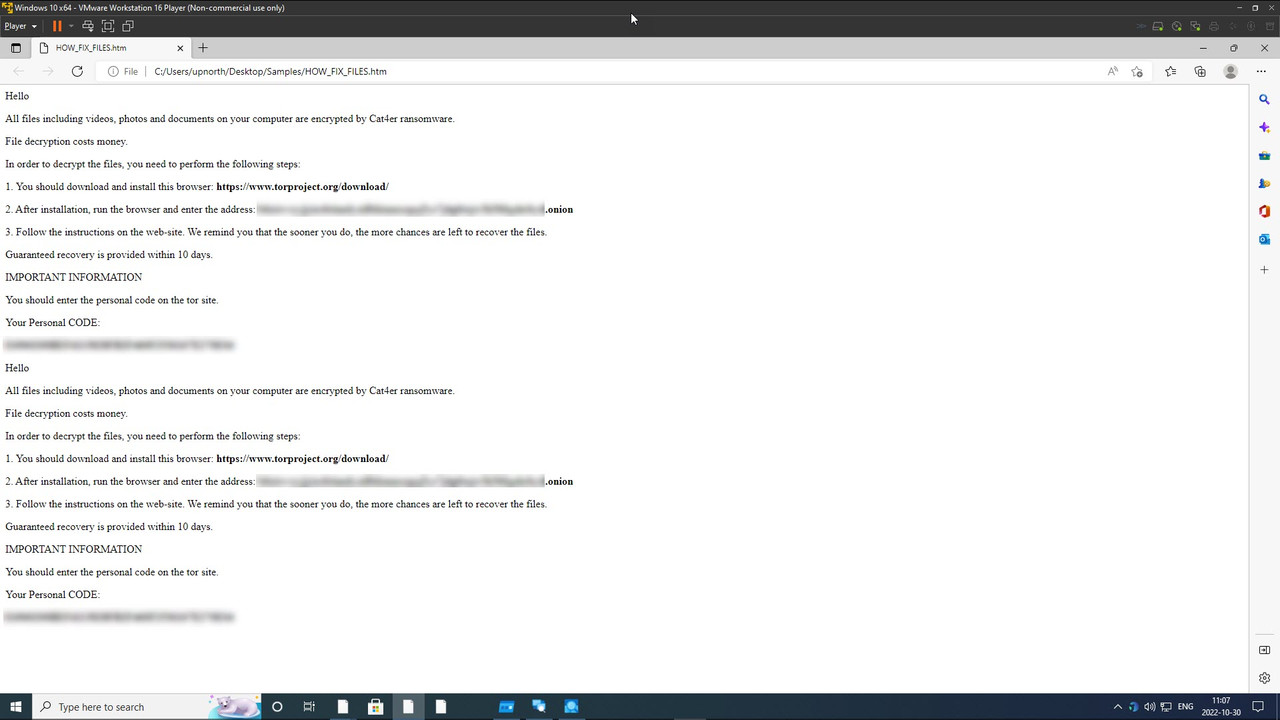
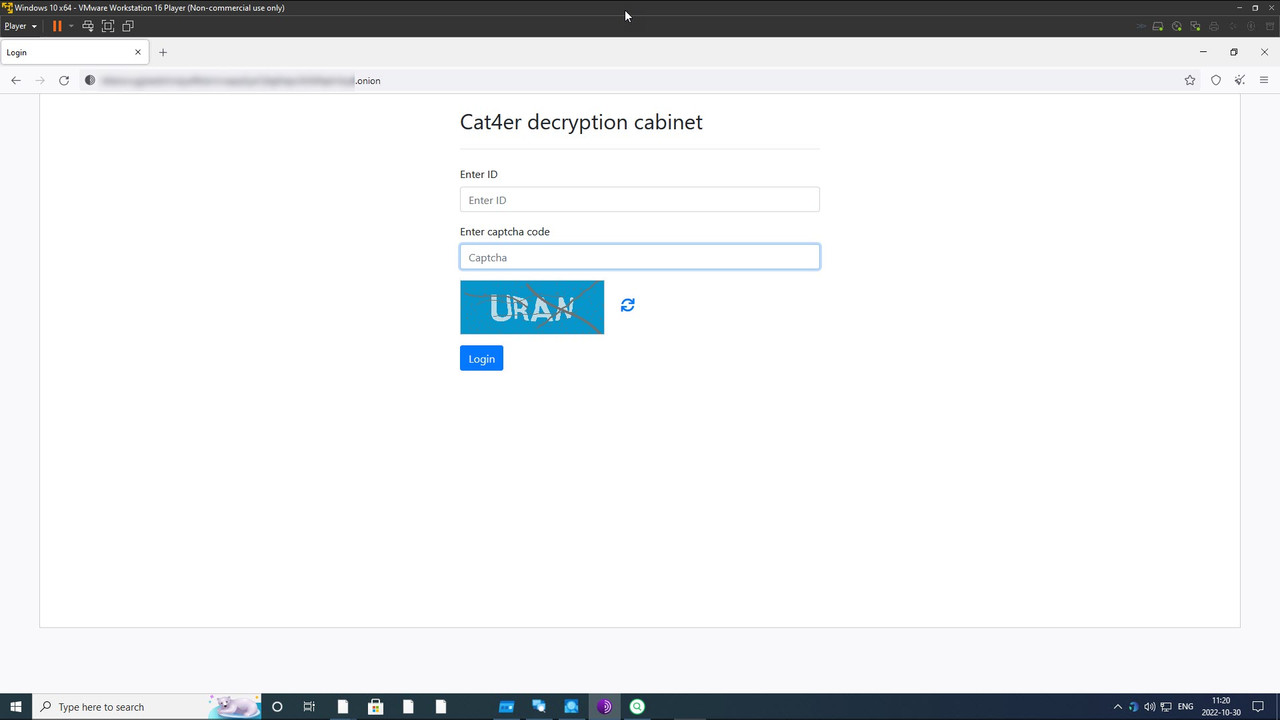
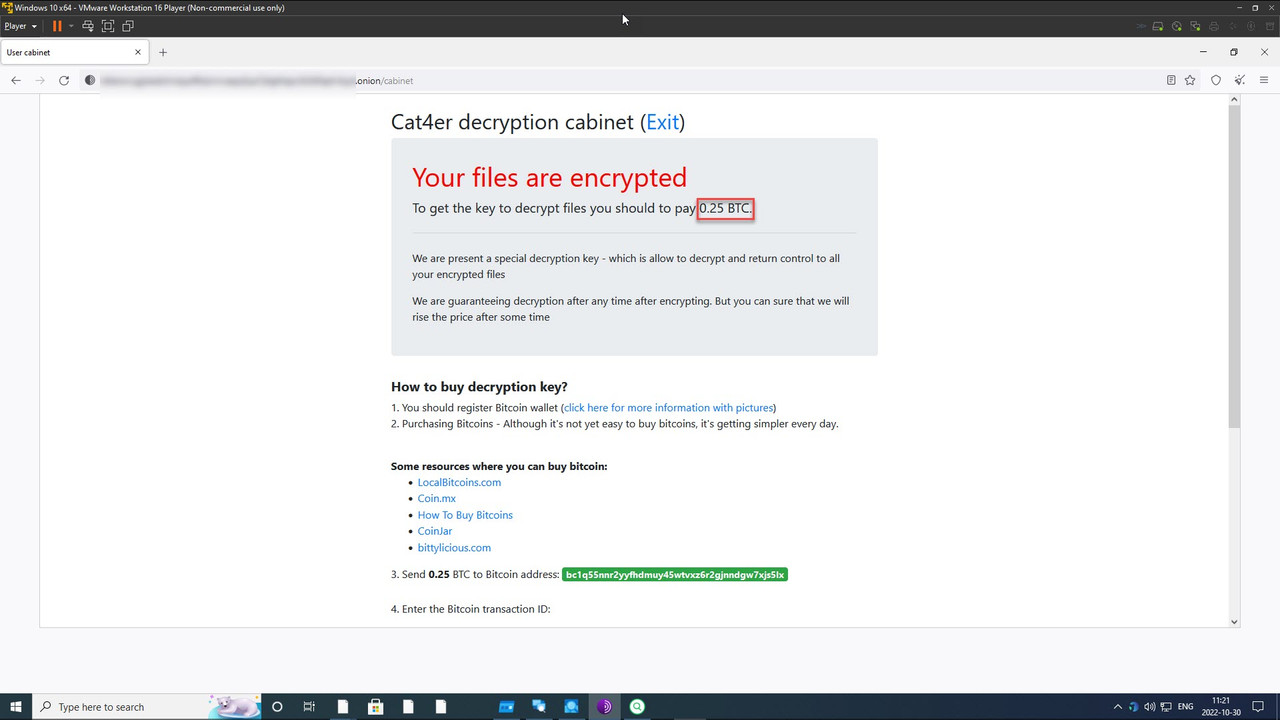
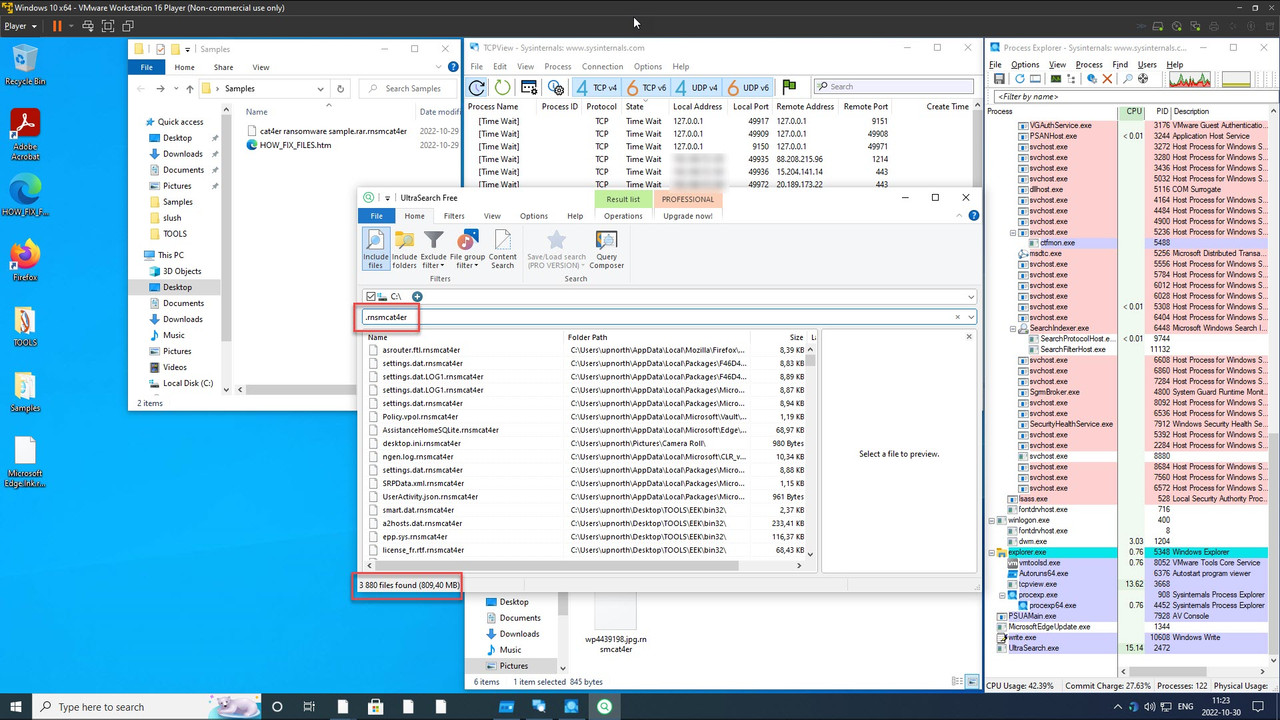
Security researchers at Trend Micro have discovered a new ransomware strain that abuses the application programming interfaces of a third-party Windows search engine tool called Everything.
The ransomware, which Trend Micro named Mimic, targets Russian and English-speaking users. It has the following capabilities:
- Collecting system information
- Bypassing User Account Control (UAC)
- Disabling Windows Defender
- Disabling Windows telemetry
- Activating anti-shutdown measures
- Activating anti-kill measures
- Unmounting virtual drives
- Terminating processes and services
- Disabling sleep mode and shutdown of the system
- Removing indicators
- Preventing system recovery
For more information

New ransomware strain exploits Windows search tool Everything
A ransomware strain that exploits a legitimate Windows search tool has recently been discovered by security researchers. The new variant can disable Windows Defender and even prevent shutdowns.