Cado Security Labs has uncovered a Realst malware campaign aimed at Web3 professionals. Dubbed the “Meeten Malware,” this cross-platform threat is capable of targeting both macOS and Windows systems, with a focus on stealing cryptocurrency wallet credentials and other sensitive data.
Operating
under the guise of legitimate companies like “Meetio,” the attackers leverage AI-generated content to create convincing websites and social media profiles, which they use to distribute the malware.
Social engineering attacks
The campaign relies on meticulous social engineering techniques. Posing as representatives of fictitious firms such as “Meeten” or “Meetio,” attackers lure targets through professional platforms like Telegram.
Reports indicate that scammers impersonate known contacts, sometimes even presenting genuine business materials stolen from the target's organization to gain credibility. Victims are directed to download a fake meeting application, which is a trojanized version of an information-stealing malware called Realst.
The associated websites contain malicious JavaScript designed to pilfer cryptocurrency stored in web browsers even before the malware is installed.
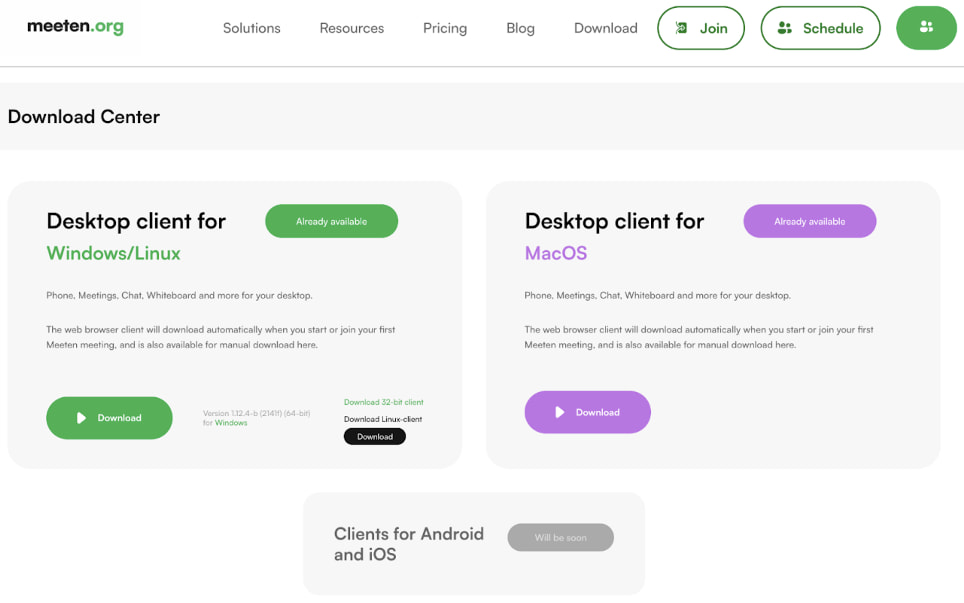
Website used in the “Meeten” attacks
Cado
The threat actors behind this campaign have exploited AI to bolster the perceived legitimacy of their operations. By using AI-generated text and images, they created professional-looking websites and maintained active social media accounts. These efforts make it harder for targets to discern the fraudulent nature of the operation. The scam highlights the growing use of AI as a tool not only for malware development but also for crafting convincing phishing campaigns.
Realst stealer analysis
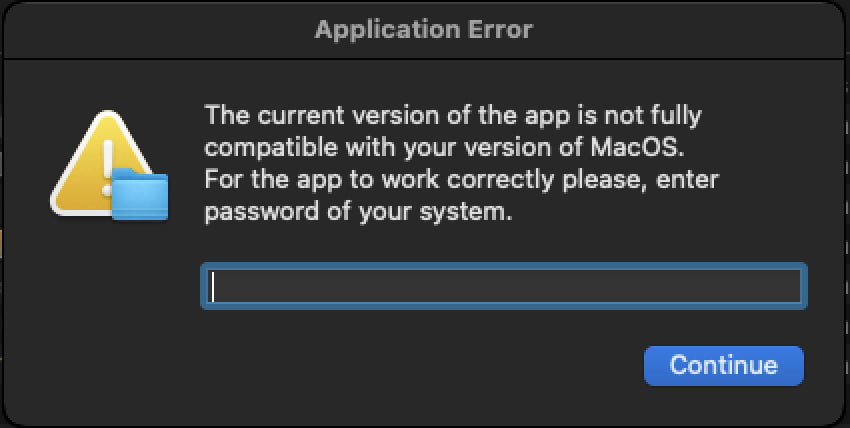
macOS variant
The macOS version, distributed as packages like CallCSSetup.pkg, is written in Rust and employs tactics to manipulate the user into providing administrative privileges. The malware uses the osascript tool to prompt for system passwords and exfiltrates sensitive data, including:
- Telegram credentials.
- Banking card details.
- Keychain credentials.
- Browser cookies and autofill credentials from major browsers like Chrome, Brave, and Edge.
- Cryptocurrency wallets, including Ledger and Trezor.
Data is zipped and sent to a remote server before the malware deletes traces of its operation.
Fake dialog used for stealing the user's password on macOS
Cado
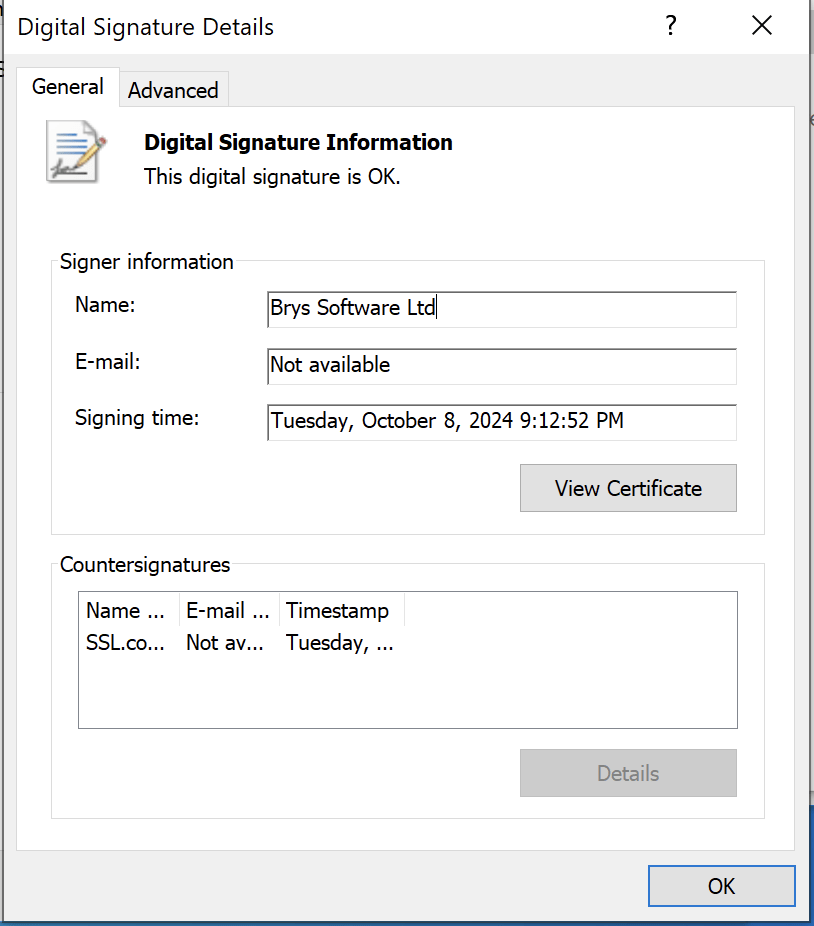
Windows variant
The Windows variant, MeetenApp.exe, is packaged using the Electron framework, a technology often used for legitimate cross-platform applications. It includes advanced obfuscation techniques, such as Bytenode-compiled JavaScript, to evade reverse engineering. The malware steals:
- Telegram credentials.
- Browser autofill data and cookies.
- Wallet credentials for popular services like Binance and Phantom.
Additionally, the Windows version achieves persistence by adding itself to the system's registry keys. Secondary payloads are fetched from external servers, enhancing the malware's capabilities and enabling it to exfiltrate system information, such as hardware IDs and running processes.
Windows variant using a digitally signed executable
Cado
To mitigate risks associated with the Meeten Malware campaign and social engineering attacks in general, the following is recommended:
- Scrutinize unsolicited business opportunities, even if they appear to come from trusted contacts.
- Avoid downloading applications from unknown or unofficial websites.
- Employ comprehensive antivirus solutions capable of detecting cross-platform threats.
- Secure accounts with additional authentication layers like MFA steps, especially for cryptocurrency platforms.
- Regularly review cryptocurrency wallet activities for unauthorized transactions.