- Aug 17, 2017
- 1,610
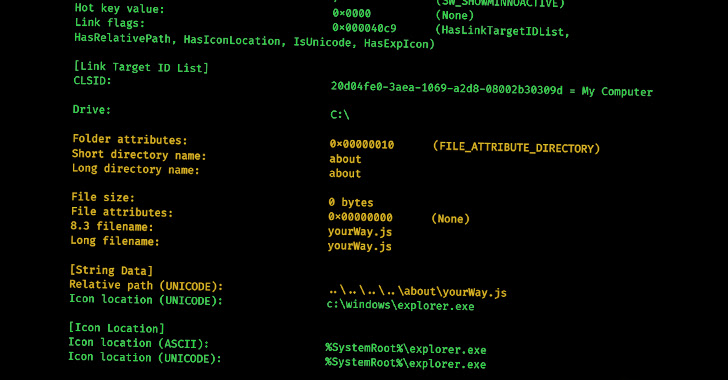
Specifically, multiple samples of LNK files leading to IcedID and Qakbot infections and those that were used in different Bumblebee campaigns have all been found to share the same Drive Serial Number. LNK files have also been employed by advanced persistent threat (APT) groups like Gamaredon (aka Armageddon) in its attacks aimed at Ukrainian government entities. The noticeable spike in campaigns using malicious shortcuts is seen as a reactive response to Microsoft's decision to disable macros by default in Office documents downloaded from the Internet, prompting threat actors to embrace alternative attachment types and delivery mechanisms to distribute malware. Recent analyses from Talos and Trustwave have disclosed how APT actors and commodity malware families alike are weaponizing Excel add-in (XLL) files and Publisher macros to drop remote access trojans on compromised machines. What's more, threat actors have been observed taking advantage of rogue Google Ads and search engine optimization (SEO) poisoning to push off-the-shelf malware like BATLOADER, IcedID, Rhadamanthys Stealer, and Vidar to victims searching for a slew of legitimate software.
New Research Delves into the World of Malicious LNK Files and Hackers Behind Them
New study by cybersecurity experts shows potential to identify relationships among threat actors by analyzing metadata of malicious LNK files.