- Oct 23, 2012
- 12,527
A new piece of ATM malware may be behind the recent ATM heists that took place in Thailand and possibly Taiwan, security researchers from FireEye have discovered.
Earlier this week, Thai authorities reported that crooks managed to steal $378,000 (12 million baht) from ATMs across Thailand.
A few minutes before local press reported the heist, FireEye researchers said that cyber-security platform detected a new file uploaded on VirusTotal from an IP address in Thailand that included all the features of ATM malware.
FireEye discovers new ATM malware family
A subsequent investigation revealed their initial suspicion. What researchers had discovered was a new malware variant that targets ATMs, which they named RIPPER, based on text found inside the malware source code (ATMRIPPER).
While this was a never-before-seen malware family, FireEye says they identified multiple components also found in other ATM malware variants such as Padpin (Tyupkin), SUCEFUL, GreenDispenser, and Skimer.
It may be possible that the malware was uploaded to VirusTotal either by one of the crooks working on a new version or by Thai investigators who found it on the infected ATMs.
Earlier this week, Thai authorities reported that crooks managed to steal $378,000 (12 million baht) from ATMs across Thailand.
A few minutes before local press reported the heist, FireEye researchers said that cyber-security platform detected a new file uploaded on VirusTotal from an IP address in Thailand that included all the features of ATM malware.
FireEye discovers new ATM malware family
A subsequent investigation revealed their initial suspicion. What researchers had discovered was a new malware variant that targets ATMs, which they named RIPPER, based on text found inside the malware source code (ATMRIPPER).
While this was a never-before-seen malware family, FireEye says they identified multiple components also found in other ATM malware variants such as Padpin (Tyupkin), SUCEFUL, GreenDispenser, and Skimer.
It may be possible that the malware was uploaded to VirusTotal either by one of the crooks working on a new version or by Thai investigators who found it on the infected ATMs.
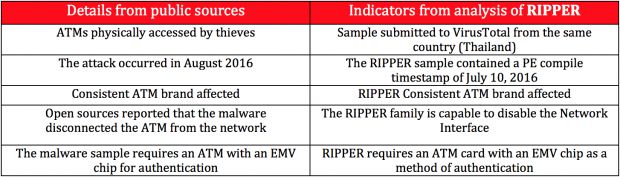
FireEye's technical analysis for RIPPER includes many findings that corroborate with ATM heist details reported by local press.
RIPPER features coincide with ATM heist press reports
The malware included a component that would disable the ATM's network interface whenever needed. Thai press quotes investigators who said the robbed ATMs were taken offline during the heists.
RIPPER allows an attacker to control ATMs via a payment card with a special authentication code embedded in its EMV chip. Investigators reported the same thing about the malware found on targeted ATMs.
The Thailand attacks only targeted ATMs manufactured by NCR. Authorities suspect that the group behind this attack was also behind an NT$70 million ($2.18 million) ATM heist in Taiwan from July. In that attack, crooks targeted ATMs from Wincor Nixdorf.
FireEye says RIPPER includes code to target three specific vendors. The company doesn't mention their names, but this fits in the group's modus operandi.
Furthermore, the PE compile timestamp from the malware uploaded this week on VirusTotal is July 10, 2016, two days before the attacks in Taiwan.
RIPPER steals features from other ATM malware strains
FireEye researchers note that RIPPER's component that reads or ejects cards on demand is very similar to the one found in SUCEFUL while the technique of using custom-made master EMV cards is borrowed from Skimer.
They add that the ability to disable the local network connection resembles that of Padpin (Tyupkin) and the "sdelete" secure self-deletion module is similar to the one found in GreenDispenser.
"In addition to requiring technical sophistication, attacks such as that affecting the ATMs in Thailand require coordination of both the virtual and the physical," FireEye researcher Daniel Regalado explains. "This speaks to the formidable nature of the thieves."