- Jul 22, 2014
- 2,525
Researchers have detected a new worm that is spreading via SMB, but unlike the worm component of the WannaCry ransomware, this one is using seven NSA tools instead of two.
The worm's existence first came to light on Wednesday, after it infected the SMB honeypot of Miroslav Stampar, member of the Croatian Government CERT, and creator of the sqlmap tool used for detecting and exploiting SQL injection flaws.
EternalRocks uses seven NSA tools
The worm, which Stampar named EternalRocks based on worm executable properties found in one sample, works by using six SMB-centric NSA tools to infect a computer with SMB ports exposed online. These are ETERNALBLUE, ETERNALCHAMPION, ETERNALROMANCE, and ETERNALSYNERGY, which are SMB exploits used to compromise vulnerable computers, while SMBTOUCH and ARCHITOUCH are two NSA tools used for SMB reconnaissance operations.
Once the worm has obtained this initial foothold, it then uses another NSA tool, DOUBLEPULSAR, to propagate to new vulnerable machines.
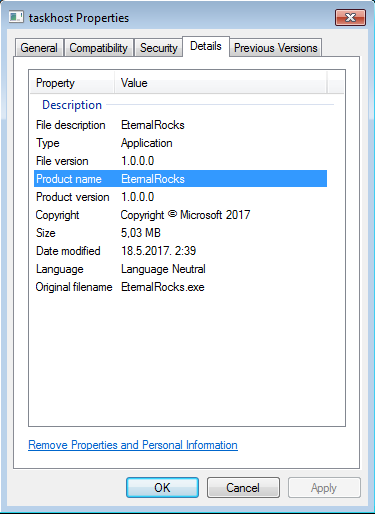
Origin of the EternalRocks name
The WannaCry ransomware outbreak, which affected over 240,000 victims, also used an SMB worm to infect computers and spread to new victims.
Unlike EternalRocks, WannaCry's SMB worm used only ETERNALBLUE for the initial compromise, and DOUBLEPULSAR to propagate to new machines.
EternalRocks is more complex but less dangerous
...
The worm's existence first came to light on Wednesday, after it infected the SMB honeypot of Miroslav Stampar, member of the Croatian Government CERT, and creator of the sqlmap tool used for detecting and exploiting SQL injection flaws.
EternalRocks uses seven NSA tools
The worm, which Stampar named EternalRocks based on worm executable properties found in one sample, works by using six SMB-centric NSA tools to infect a computer with SMB ports exposed online. These are ETERNALBLUE, ETERNALCHAMPION, ETERNALROMANCE, and ETERNALSYNERGY, which are SMB exploits used to compromise vulnerable computers, while SMBTOUCH and ARCHITOUCH are two NSA tools used for SMB reconnaissance operations.
Once the worm has obtained this initial foothold, it then uses another NSA tool, DOUBLEPULSAR, to propagate to new vulnerable machines.

Origin of the EternalRocks name
The WannaCry ransomware outbreak, which affected over 240,000 victims, also used an SMB worm to infect computers and spread to new victims.
Unlike EternalRocks, WannaCry's SMB worm used only ETERNALBLUE for the initial compromise, and DOUBLEPULSAR to propagate to new machines.
EternalRocks is more complex but less dangerous
...
