proofpoint.com: Threat actors follow the money: Proofpoint releases the Human Factor 2018 Report
Trends: Threat actors follow the money: Proofpoint releases the Human Factor 2018 Report
Trends: new threats every day, from massive malicious spam campaigns to phishing, social media scams, web-based attacks
By Proofpoint Staff

Individuals and organizations encounter new threats every day, from massive malicious spam campaigns to phishing, social media scams, web-based attacks, and even attacks by state-sponsored actors. Yet the vast majority of these threats share a common thread: they exploit the “human factor” rather than relying on software and hardware vulnerabilities.
The human factor—the instincts of curiosity and trust that lead well meaning people to click, download, install, move funds, and more—is simply more reliable and lucrative than exploits with increasingly short shelf lives.
Here are the key findings from Proofpoint’s 2018 Human Factor Report, exploring the ways in which threat actors continue to refine their approaches to social engineering with well-crafted lures and schemes that regularly trick even savvy users.
Social Engineering
We see countless examples of the social engineering that underpins the human factor.
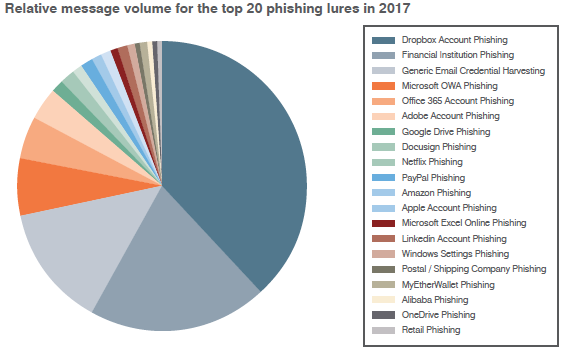
Figure 1: Relative phishing message volumes for the top lures in 2017
Targeting trends
Attacks throughout the year ranged from massive malicious spam campaigns to highly targeted email fraud attacks.
Users are accustomed to frequent email notifications from cloud services and apps but attackers are using these services to send malicious messages and host malware.
Trends: Threat actors follow the money: Proofpoint releases the Human Factor 2018 Report
Trends: new threats every day, from massive malicious spam campaigns to phishing, social media scams, web-based attacks
By Proofpoint Staff

Individuals and organizations encounter new threats every day, from massive malicious spam campaigns to phishing, social media scams, web-based attacks, and even attacks by state-sponsored actors. Yet the vast majority of these threats share a common thread: they exploit the “human factor” rather than relying on software and hardware vulnerabilities.
The human factor—the instincts of curiosity and trust that lead well meaning people to click, download, install, move funds, and more—is simply more reliable and lucrative than exploits with increasingly short shelf lives.
Here are the key findings from Proofpoint’s 2018 Human Factor Report, exploring the ways in which threat actors continue to refine their approaches to social engineering with well-crafted lures and schemes that regularly trick even savvy users.
Social Engineering
We see countless examples of the social engineering that underpins the human factor.
- Suspiciously registered domains of large enterprises outnumbered brand-registered domains 20 to 1. That means targets of phishing attacks are more likely to mistake typosquatted and suspicious domains for their legitimate counterparts.
- Fake browser and plugin updates appeared in massive malvertising campaigns affecting millions of users. As many as 95% of observed web-based attacks like these, including those involving exploit kits, incorporated social engineering to trick users into installing malware.
- About 55% of social media attacks that impersonated customer-support accounts—a trend known as “angler phishing”—targeted customers of financial services companies.
- Some 35% of social media scams that used links and “clickbait” brought users to video streaming and movie download sites.
- Examining trends in volume and type of attack provide useful insights for both defenders and organizations.
- Dropbox phishing was the top lure for phishing attacks but click rates for Docusign lures were the highest at over five times the average click rate for the top 20 lures, demonstrating that volume did not necessarily equate to effectiveness.
- Observed network traffic of coin mining bots jumped almost 90% between September and November. This threat activity closely mirrored the rise and fall of the value of Bitcoin.
- Ransomware and banking Trojans accounted for more than 82% of all malicious email messages, making them the most widely distributed malware types.
- Microsoft Office exploits appeared regularly in email campaigns but they usually came in short bursts.

Figure 1: Relative phishing message volumes for the top lures in 2017
Targeting trends
Attacks throughout the year ranged from massive malicious spam campaigns to highly targeted email fraud attacks.
- Education, management consulting, entertainment, and media firms experienced the greatest number of EMAIL FRAUD attacks, averaging over 250 attacks per organization.
- Construction, manufacturing, and technology topped the most phished industries. Manufacturing, healthcare, and technology firms were the top targets of crimeware.
- Ransomware predominated worldwide, but Europe and Japan saw the highest regional proportions of banking Trojans, with 36% and 37% of all malicious mail in those regions respectively.
- Businesses are embracing cloud services to improve worker collaboration, streamline operations and engage customers but with these new benefits come new risks.
- Nearly 25% of all suspicious login attempts to cloud services were successful.
- About 1% of all cloud service credentials have been in leaked in our sample of hundreds of thousands of SaaS accounts examined during risk assessments conducted across industries.
- Roughly half of all cloud app users have installed third-party add-ons. About 18% of these add-ons have access to email and files.
- Around 60% of cloud service users, including 37% of privileged users, did not have a password policy or multi-factor authentication enforced.
Users are accustomed to frequent email notifications from cloud services and apps but attackers are using these services to send malicious messages and host malware.
- No major cloud services avoided abuse. For example, threat actors used Microsoft SharePoint to host malware distributed in millions of messages across hundreds of campaigns through 2017.
- Other services, ranging from G Suite to Evernote, were used to send phishing emails and malware.
- Third-party add-ons open up new features, but they also create possibilities for abuse. We found a vulnerability in Google Apps Script, for example, that allowed attackers to send malware through legitimate emails that came from G Suite accounts.
Last edited: