- Apr 25, 2013
- 5,355
Introduction
The Netherlands was hit with a new spamrun designed to spread a cryptolocker variant known as torrentlocker from Monday October 13th 2014 onwards. Please note that torrentlocker appears to present itself to victims as cryptolocker in all cases. Fox-IT now receives multiple reports of new victims in the Netherlands and we are currently analyzing the new spamrun and malware that was subsequently used.
This blogpost is aimed at providing victims with advice on how to deal with the infections. It contains technical details that will help system administrators trace back the original infection, and contain the spread of the infection as much as possible. We will update this blog post as more information is available.
What to do if you are a victim of torrentlocker?
You have fallen victim to torrentlocker if you find that a number of your (data) files have been encrypted and are unreadable. In this instance of torrentlocker, each directory that contains encrypted files will also contain an HTML-file with instruction on how to contact and pay the criminals behind this latest wave of torrentlocker attacks.
There are a number of things that you can do yourself to find the original infection and contain the spread of torrentlocker and if possible restore files to their original state.

Indicators of compromise in email
Within your messaging logs, you may search for emails with the subject:
Heb je niet geleverde packet
Starting on Sunday emails were sent around impersonating a Dutch postal company called PostNL. The emails were styled so as to look exactly like the company’s normal email communication:

The recipient of the email is enticed to click on the ‘Zie de informatie’ link. This took the recipient to a compromised wordpress website used as redirection page towards the actual malicous page.
Indicators of compromise in network traffic
Within your gateway logs (proxy, firewall and IDS logs, etc) you may search for traffic to the following site in order to identify systems within your infrastructure that visited malicious websites associated with this attack. Please note that this list contains currently known resources on the internet but is not necessarily complete.
Initial websites linked to in the email:
The domain ‘postnl-track.com’ had its CSS and images loaded from ‘postnl-track.com’. The page was a convincing page talking about a track and trace document being available:
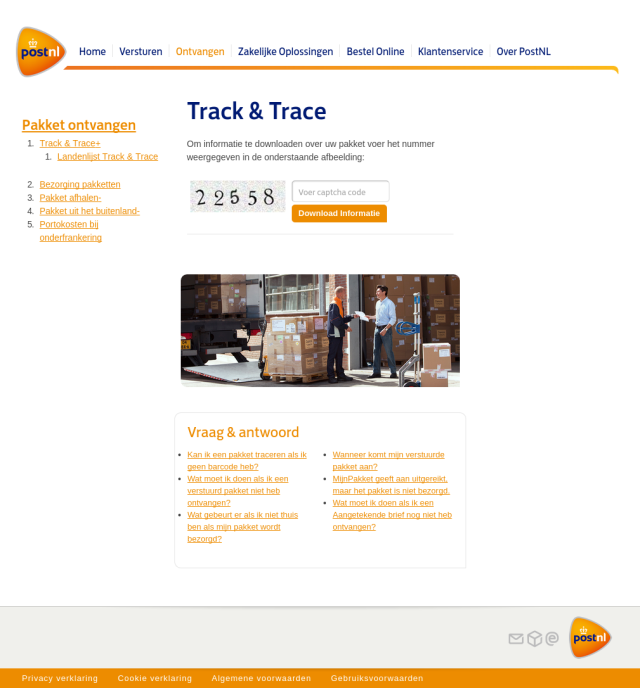
The user is forced to enter the captcha in order to proceed. After the captcha the user is presented with a download of their track and trace information:

The user is presented with a zip which has the payload inside. After opening their ‘document’ the malware will start connecting with its command and control server, generate encryption keys and start encrypting files. After its completed the user is presented with the following notice:

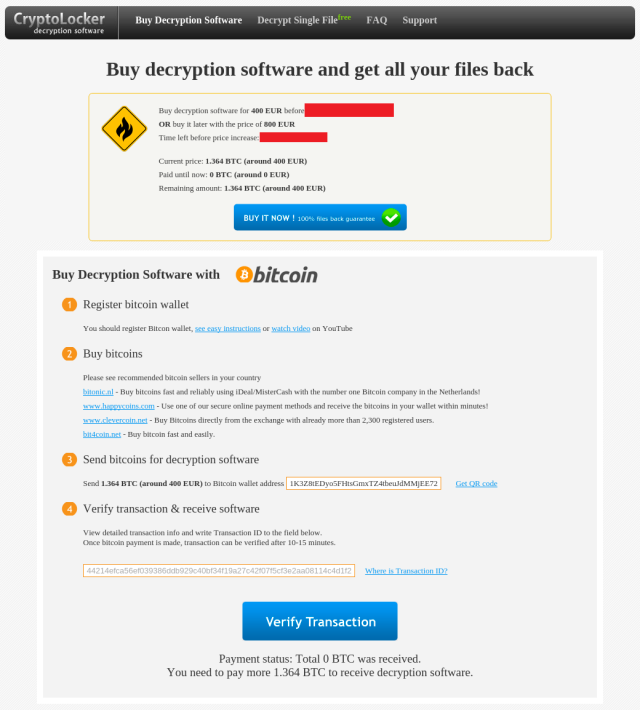
When visiting one of the links of their payment website the user is told to pay 400 EURO’s within a certain time otherwise the price will be doubled:
Indicators of compromise on hosts
On suspected systems, you may look for the following clues of infection by torrentlocker. Please note that once you determine that a system is infected, you should remove it from your infrastructure. Do not wipe or reinstall the system as it may contain additional clues about the infection.
The Netherlands was hit with a new spamrun designed to spread a cryptolocker variant known as torrentlocker from Monday October 13th 2014 onwards. Please note that torrentlocker appears to present itself to victims as cryptolocker in all cases. Fox-IT now receives multiple reports of new victims in the Netherlands and we are currently analyzing the new spamrun and malware that was subsequently used.
This blogpost is aimed at providing victims with advice on how to deal with the infections. It contains technical details that will help system administrators trace back the original infection, and contain the spread of the infection as much as possible. We will update this blog post as more information is available.
What to do if you are a victim of torrentlocker?
You have fallen victim to torrentlocker if you find that a number of your (data) files have been encrypted and are unreadable. In this instance of torrentlocker, each directory that contains encrypted files will also contain an HTML-file with instruction on how to contact and pay the criminals behind this latest wave of torrentlocker attacks.
There are a number of things that you can do yourself to find the original infection and contain the spread of torrentlocker and if possible restore files to their original state.
- (temporarily) Block access to certain resources on the internet in order to minimize the risk of further infections. For information on which resources to block, see section “Indicators of compromise in network traffic”.
- Activate system policies that prevent further activity by torrentlocker:
- Activate a policy that prevents users from deleting files from shares. We have indications that such a policy may prevent torrentlocker from working effectively. We are currently investigating this claim.
- In addition, you may change user’s rights on all files to “read-only”. This will prevent changes to files.
- Identify the systems that were initially infected with torrentlocker. Once identified, these systems should be removed from the infrastructure, which would prevent further encryption of additional files. The following steps will help with identification:
- Identify who received emails as part of the spamrun. Within your email messaging logs, search for email messages with characteristics as described in the section “Indicators of compromise in email”. Any hits should provide you with information about who within your organization received emails as part of the spamrun and will allow you to remove these emails.
- Identify who visited suspicious torrentlocker websites. Within your gateway logs (proxy logs, firewall logs, IDS logs etc) search for visits to websites known to be associated with this spamrun. Any hits should provide you with evidence which systems within your infrastructure visited those websites and are potentially infected with torrentlocker. More information about what to look for can be found in section “Indicators of compromise in network traffic”.
- Identify which systems are infected. After the previous two steps, you may have narrowed down the number of systems that are potentially infected and have caused the files to be encrypted. On suspected systems, you may use the information in the section “Indicators of compromise on hosts”.
- Remove the identified systems from your infrastructure. Do not wipe or reimage these systems as they may contain important clues for decryption of the encrypted files or additional information about the infection.
- Restore backups of the infected files.

Indicators of compromise in email
Within your messaging logs, you may search for emails with the subject:
Heb je niet geleverde packet
Starting on Sunday emails were sent around impersonating a Dutch postal company called PostNL. The emails were styled so as to look exactly like the company’s normal email communication:

The recipient of the email is enticed to click on the ‘Zie de informatie’ link. This took the recipient to a compromised wordpress website used as redirection page towards the actual malicous page.
Indicators of compromise in network traffic
Within your gateway logs (proxy, firewall and IDS logs, etc) you may search for traffic to the following site in order to identify systems within your infrastructure that visited malicious websites associated with this attack. Please note that this list contains currently known resources on the internet but is not necessarily complete.
Initial websites linked to in the email:
Code:
annswebfolio.com/wp-content/themes/twentfourteen/showthread.php
nodramadating.com/wp-content/uploads/showthread.php
strengthyourrunning.com/wp-includes/js/tinymce/themes/advanced/skins/wp_theme/img/showthread.php
kjob.jp/re/wp-content/themes/twentyten/showthread.php
garypilafas.com/wp-content/themes/whitehousepro3_dev/showthread.php
The above websites redirected to:
www.postnl-tracktrace.com
postnl-track.com
Domains for command and control traffic over SSL:
server4love.ru
octoberpics.ru
Command and control IP’s involved with this threat:
46.161.30.20
46.161.30.16
Fake PostNL IP’s involved with this threat:
109.68.190.174
193.124.95.83
The user is forced to enter the captcha in order to proceed. After the captcha the user is presented with a download of their track and trace information:

The user is presented with a zip which has the payload inside. After opening their ‘document’ the malware will start connecting with its command and control server, generate encryption keys and start encrypting files. After its completed the user is presented with the following notice:

When visiting one of the links of their payment website the user is told to pay 400 EURO’s within a certain time otherwise the price will be doubled:

Indicators of compromise on hosts
On suspected systems, you may look for the following clues of infection by torrentlocker. Please note that once you determine that a system is infected, you should remove it from your infrastructure. Do not wipe or reinstall the system as it may contain additional clues about the infection.
- The initial infection is dropped as the following file C:\WINDOWS\[a-z]{8}.exe
- There will be a reference in the registry to the previous file, to make sure that torrentlocker starts up automatically upon boot. You may use the Windows tool msconfig to inspect startup entries.
- A second process “explorer.exe” will be active.