- Apr 5, 2014
- 6,008
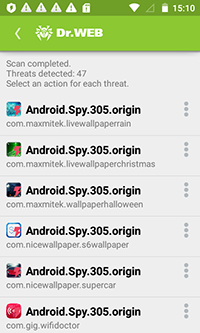
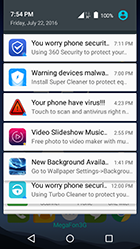
Doctor Web specialists have discovered a Trojan on Google Play that displays annoying advertisements and steals private user information. This malware has been incorporated into more than 150 Android applications which have already been downloaded by over 2.8 million users.
This Trojan, named Android.Spy.305.origin, is implemented as an advertising SDK platform that is used to generate income from application downloads. Doctor Web specialists registered at least seven developers who have embedded Android.Spy.305.origin into their apps: MaxMitek Inc, Fatty Studio, Gig Mobile, TrueApp Lab, Sigourney Studio, Doril Radio.FM, Finch Peach Mobile Apps, and Mothrr Mobile Apps.
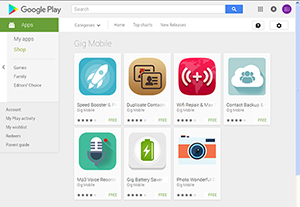

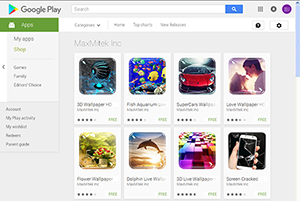
Among these malicious applications are live wallpapers, image catalogs, utilities, photo editors, radio applications, and so on. Thus far Doctor Web’s security researchers have registered 155 dangerous applications, which have already been downloaded over 2.8 million times. Although the company informed Google as to which applications contain Android.Spy.305.origin, many of them are still available for download.
Once one of these applications is launched, Android.Spy.305.origin connects to its command and control (C&C) server and receives a command to download an additional module—Android.Spy.306.origin. This component contains the main malicious payload that Android.Spy.305.origin uses with the help of the DexClassLoader class.
The Trojan then sends the following data to the C&C server:
This Trojan, named Android.Spy.305.origin, is implemented as an advertising SDK platform that is used to generate income from application downloads. Doctor Web specialists registered at least seven developers who have embedded Android.Spy.305.origin into their apps: MaxMitek Inc, Fatty Studio, Gig Mobile, TrueApp Lab, Sigourney Studio, Doril Radio.FM, Finch Peach Mobile Apps, and Mothrr Mobile Apps.



Among these malicious applications are live wallpapers, image catalogs, utilities, photo editors, radio applications, and so on. Thus far Doctor Web’s security researchers have registered 155 dangerous applications, which have already been downloaded over 2.8 million times. Although the company informed Google as to which applications contain Android.Spy.305.origin, many of them are still available for download.
Once one of these applications is launched, Android.Spy.305.origin connects to its command and control (C&C) server and receives a command to download an additional module—Android.Spy.306.origin. This component contains the main malicious payload that Android.Spy.305.origin uses with the help of the DexClassLoader class.
The Trojan then sends the following data to the C&C server:
- Email address connected to the Google user account
- List of installed applications
- Current system language
- Name of the device manufacturer
- Mobile device model
- IMEI identifier
- OS version
- Screen resolution
- Mobile network operator
- Name of the application containing the Trojan
- Developer’s ID
- SDK platform’s version