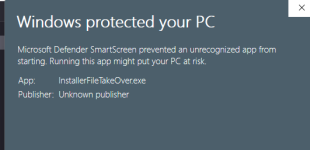
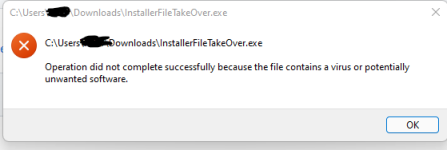
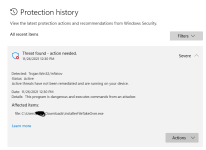
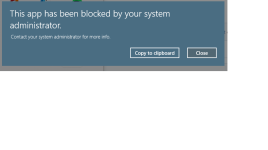
I tried this exploit on my computer (with Edge + Defender + SWH), but it was very hard:
- The download was blocked by Edge and I had to use "keep anyway" 3 times until Edge allowed it.
- The file was detected by Defender and when allowed, the execution was blocked by SmartScreen.
- Next, I tried another attack vector and downloaded the sample in the ZIP archive. After opening the downloaded file from Edge the Explorer window was displayed, so I clicked the InstallerFileTakeOver to execute the exploit. The execution was blocked by SmartScreen and next by SRP in the user Temp folder (where the archive was unpacked).
- Finally, I manually unpacked the ZIP archive and clicked on InstallerFileTakeOver executable. It was blocked by SmartScreen. In this case, the file was blocked thanks to the Windows built-in unpacker which preserves the MOTW (file could be executed if I would use 7-ZIP).
Last edited: