Question NextDNS client infected?
- Thread starter oldschool
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
During the installation of a program, all this behaviour (including the one that is deemed as attack) is normal, there is nothing out of the ordinary there. I would still flag this thread for @struppigel but I don’t see any malicious payload or behaviour in this installer.
1-2 products that apparently have a very aggressive configuration on VT, such as Fortinet, detect heuristic threats. It’s not enough to even suspect anything.
1-2 products that apparently have a very aggressive configuration on VT, such as Fortinet, detect heuristic threats. It’s not enough to even suspect anything.
If you are to believe the poster in that forum post the installer tries to use taskkill to disable AV, reads clipboard and installs a keylogger. Suspicious behaviour indeed, and if it is OilRig linked campaign then that is a well-known APT crew. It wouldn't surprise me as NextDns would be a prime target for APT crews to compromise. But someone somewhere should have noticed this earlier if it is indeed a breach/compromise and if the file is 4 months old so it's not new, unsure of the final verdict.
That’s why tools like VT and various sandboxes are not used in real-time protection, as they will delete 90% of Windows and will leave just 5 pictures in the document folder.If you are to believe the poster in that forum post the installer tries to use taskkill to disable AV, reads clipboard and installs a keylogger. Suspicious behaviour indeed, and if it is OilRig linked campaign then that is a well-known APT crew. It wouldn't surprise me as NextDns would be a prime target for APT crews to compromise. But someone somewhere should have noticed this earlier if it is indeed a breach/compromise and if the file is 4 months old so it's not new, unsure of the final verdict.
What’s displayed as “keylogging” behaviour might be just attempts to capture keyboard shortcuts.
The AV strings might be for compatibility reasons, for example NextDNS might be applying special configurations to be compatible with antivirus software.
In the context of an installer and installed application such as NextDNS, there is nothing suspicious really. It will be suspicious if a PDF document attempts all that.
Your points are very valid and spot on, as I said if this has been around for 4 months then it would have been caught earlier you would think especially if it was OilRig threat actors, it's probably just paranoia at work by the forum poster. NextDns users would be the security conscious type, sometimes you try and find issues where there are none and find hacks/breaches when it's just a dumb app config or something innocuous. I guess with all the hacks/breaches lately it's impacted people's thinking, people expect hacks and think nothing is secure.
.
.
Really!? With confusing correlation reference to a locked SOC report, Mitre basic info, and AnyRun samples that's from 2018, 2019 and 2020 with a Oilrig tag, all high detected btw, and the " supposed " related dropped files in the latest VT submission with 1 score/detections, this is a 100% conclusive assessment on a genuine, Oilrig attack?infected by a threat actor from the middle east
You always make me laugh lol.Really!? With confusing correlation reference to a locked SOC report, Mitre basic info, and AnyRun samples that's from 2018, 2019 and 2020 with a Oilrig tag, all high detected btw, and the " supposed " related dropped files in the latest VT submission with 1 score/detections, this is a 100% conclusive assessment on a genuine, Oilrig attack?
View attachment 274590
Not sure how it was even attributed and specially to Oilrig.
Either the poster is genuinely confused (I do not want to use the word dumb) and misinterpreted the rule vs the match or it is one of those repeated attempts from other DNS provides.Really!?
Like he is referring to the taskkill to be used to kill AV. No, it is used to kill NextDNS.exe so it can be updated.
Attachments
So a software that makes Taskill is necessarily a malware?
OK there is KillAV malware, but the antivirus software blocks it quickly and knows how to defend itself (Self-Defense).
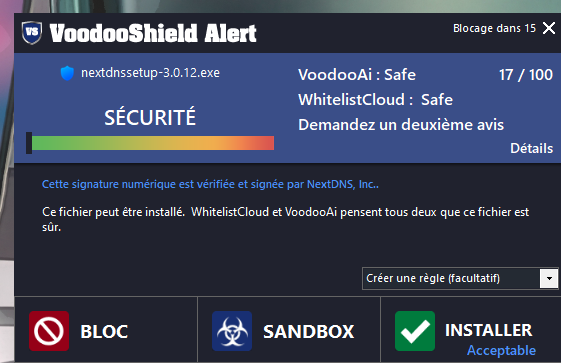
For NextDNS, no detection with ESET up to date and Voodooshield.
(Sorry, my software is in French, it's my language)
OK there is KillAV malware, but the antivirus software blocks it quickly and knows how to defend itself (Self-Defense).
For NextDNS, no detection with ESET up to date and Voodooshield.
(Sorry, my software is in French, it's my language)
You forgot to update VoodooShield to the latest version. Thats even worse than the fact that the NextDNS installer could be infected. >_>So a software that makes Taskill is necessarily a malware?
OK there is KillAV malware, but the antivirus software blocks it quickly and knows how to defend itself (Self-Defense).
For NextDNS, no detection with ESET up to date and Voodooshield.
(Sorry, my software is in French, it's my language)
View attachment 274598
View attachment 274599
Updating..You forgot to update VoodooShield to the latest version. Thats even worse than the fact that the NextDNS installer could be infected. >_>

Waiting Simpsons GIF - Waiting Simpsons Homer - Découvrir et partager des GIF
Click to view the GIF
So a software that makes Taskill is necessarily a malware?
The original poster is not very knowledgeable and quickly saw behaviour which undoubtedly COULD be dangerous, just not in this context. This is why this behaviour alone can’t be used to create detections, it is not reliable, it will produce a lot of fps.
He is talking about this:
From there, he is quick to suppose that NextDNS is infected and he even pins it on a specific attacker. I would expect him soon to go and sue the “attacker”. Assuming much?
The dropped files he is referring to (with detection) are few shortcuts detected by a second-tier engine with low reliability (not Kaspersky, Eset, Bitdefender, Symantec). Obviously this detection means nothing.
And those are the only posts that he did on the NextDNS forum. Might actually be a hater or someone from the competition, but those are just assumptions.The original poster is not very knowledgeable and quickly saw behaviour which undoubtedly COULD be dangerous, just not in this context. This is why this behaviour alone can’t be used to create detections, it is not reliable, it will produce a lot of fps.
He is talking about this:
View attachment 274602
From there, he is quick to suppose that NextDNS is infected and he even pins it on a specific attacker. I would expect him soon to go and sue the “attacker”. Assuming much?
I don't think he is a hater. You would use Twitter or Reddit to bash a competitor not the companies very own forum where they can censor and delete your post. I think he is just confused or misreading VT results, maybe he's new to the security world and has read one too many APT reports and the constant media headlines and attention of hacks and breachers has got to him and he's looking for things that are not there.And those are the only posts that he did on the NextDNS forum. Might actually be a hater or someone from the competition, but those are just assumptions.
NextDNS does not that, they are hardly active at all, considering it is just 2 people. There are regular posts on NextDNS forum and reddit to persuade people to move to a "better" DNS.I don't think he is a hater. You would use Twitter or Reddit to bash a competitor not the companies very own forum where they can censor and delete your post.
So what I get from that thread every is that every software that kills its active tasks when updating or reads for keyboard shortcut is malware. Wow! I had no idea my system was so heavily infected. All major security suite failed me! I'll ditch my computers and start using an abacus... 
The Bitdefender engine used to detect the .lnk file as a FileRunner Trojan (old report from 1 month ago?) or something like that, but after doing the "Renalyze file" option in VT, it stopped. This is probably why he thought it was infected.
Last edited:
That’s why tools like VT and various sandboxes are not used in real-time protection, as they will delete 90% of Windows and will leave just 5 pictures in the document folder.
You may also like...
-
-
-
-
Question Anyone else having their LG TV attempting to reach weird domains?
- Started by cartaphilus
- Replies: 8