silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,181
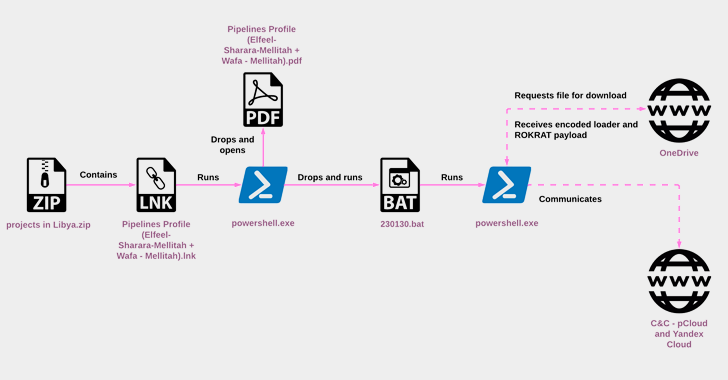
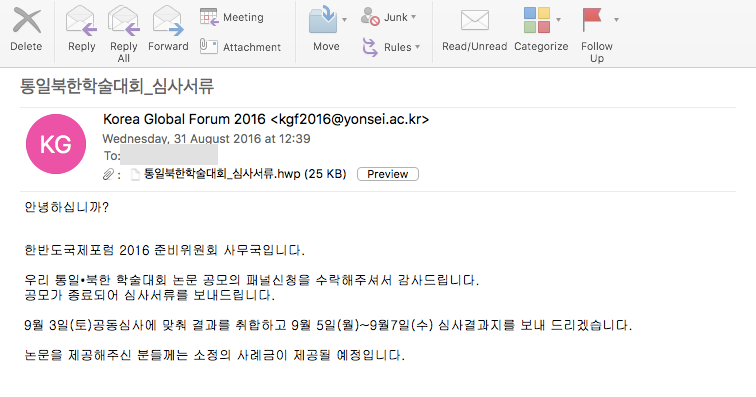
The North Korean threat actor known as ScarCruft started experimenting with oversized LNK files as a delivery route for RokRAT malware as early as July 2022, the same month Microsoft began blocking macros across Office documents by default.
"RokRAT has not changed significantly over the years, but its deployment methods have evolved, now utilizing archives containing LNK files that initiate multi-stage infection chains," Check Point said in a new technical report.
"This is another representation of a major trend in the threat landscape, where APTs and cybercriminals alike attempt to overcome the blocking of macros from untrusted sources."

North Korea's ScarCruft Deploys RokRAT Malware via LNK File Infection Chains
ScarCruft, the North Korean threat group behind RokRAT malware, has adapted to the blocking of macros by using oversized LNK files.
 thehackernews.com
thehackernews.com