Mandiant researchers have uncovered a groundbreaking method to bypass browser isolation technologies, leveraging machine-readable QR codes to establish command-and-control (C2) communication in environments designed to prevent traditional attack methods. The technique highlights critical weaknesses in remote, on-premises, and local browser isolation solutions.
How browser isolation works
Browser isolation aims to protect users by separating web browsing from local systems, typically running the browser in a secure cloud, on-premises, or virtualized environment. It prevents direct interaction between the local device and malicious web content by streaming only the visual content (pixels) to the user. This setup hinders common C2 approaches that rely on HTTP request and response manipulation, as attackers cannot directly access the raw HTTP response from the isolated environment.
QR code-based C2 exploit
Mandiant's Red Team
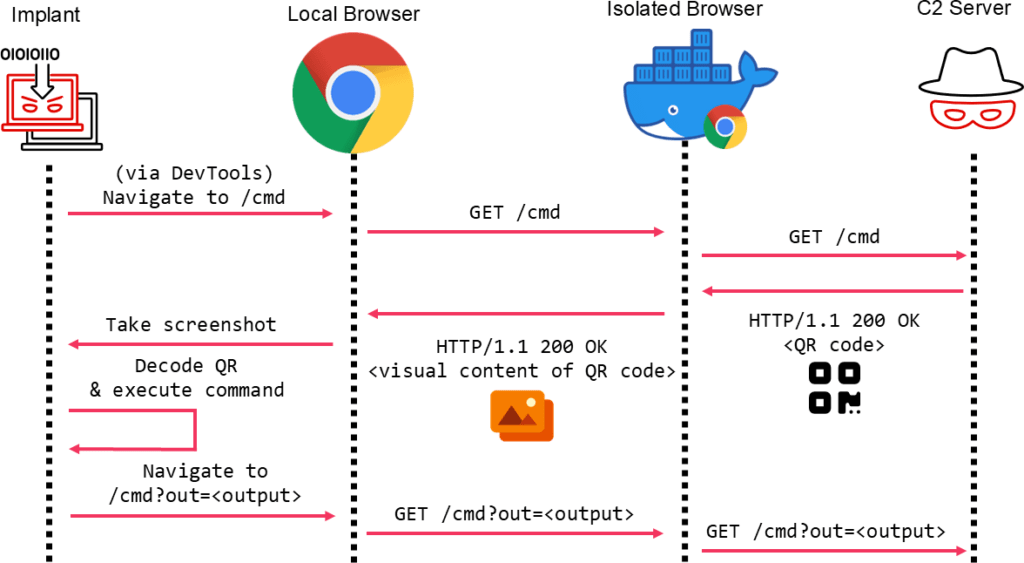
developed a novel strategy for bypassing these restrictions. Instead of embedding C2 commands in HTTP responses, the attacker-controlled server sends a web page containing a QR code. The malicious implant renders the page in a headless browser, captures a screenshot of the QR code via pixel streaming, and decodes it to retrieve embedded command data.
The C2 communication proceeds as follows:
- The implant initiates a local headless browser (e.g., using Puppeteer).
- It retrieves the attacker's web page, which is rendered through the isolated browser.
- The QR code is displayed visually in the pixel stream.
- The implant captures and decodes the QR code to extract the command.
- Command output is sent back to the attacker via URL parameters in subsequent requests.
Mandiant's proof-of-concept (PoC) implementation relied on the Google Chrome browser in headless mode and integrated with Cobalt Strike's External C2 feature. This approach is versatile, working across all three types of browser isolation.
Challenges and limitations
While effective, the QR code-based C2 method has limitations. For starters, QR codes can store a maximum of 2,953 bytes, but streaming quality issues forced Mandiant to limit data to 2,189 bytes.
Secondly, each request takes ~5 seconds due to rendering and processing delays, making high-throughput operations like SOCKS proxying impractical. Finally, running headless browsers and decoding QR codes introduces significant complexity and latency.
Despite those limitations, Mandiant's exercise exposes weaknesses in browser isolation, which, while effective against many traditional threats, is not impervious. Organizations relying solely on isolation must consider this new attack vector and strengthen their defenses accordingly.
Mandiant recommends adopting a multi-layered “defense in depth” strategy, including traffic inspections for anomalous patterns indicative of QR code-based C2 activity and performing domain reputation checks and URL scanning.