- Jan 24, 2011
- 9,378
In a two-part investigation, security researchers from Israeli security firm Check Point have dug around in countless logs of telemetry data to get to the bottom of the Nuclear Exploit Kit (EK) one of the most popular crimeware kits today.
Exploit kits are scripts that crooks install on a server that when a user visits a Web page, scans the victim's local PC setup for known software vulnerabilities and delivers an exploit that cracks the user's defenses and automatically installs malware without his knowledge.
Some of the most known exploit kits are Blackhole (now defunct), Angler (the most popular), Magnitude, and Neutrino. Also very popular is the Nuclear EK, which Check Point researchers recently managed to track down and hack into one of its master servers.
Nuclear EK author lives in Krasnodar, Russia
According to researchers, the Nuclear EK is offered as MaaS (Malware-as-a-Service) by a crook living in Krasnodar, Russia. This man is suspected to be the EK's leading developer, but Check Point says that Nuclear is not a one-man job and that others are also almost certainly helping him manage the service.
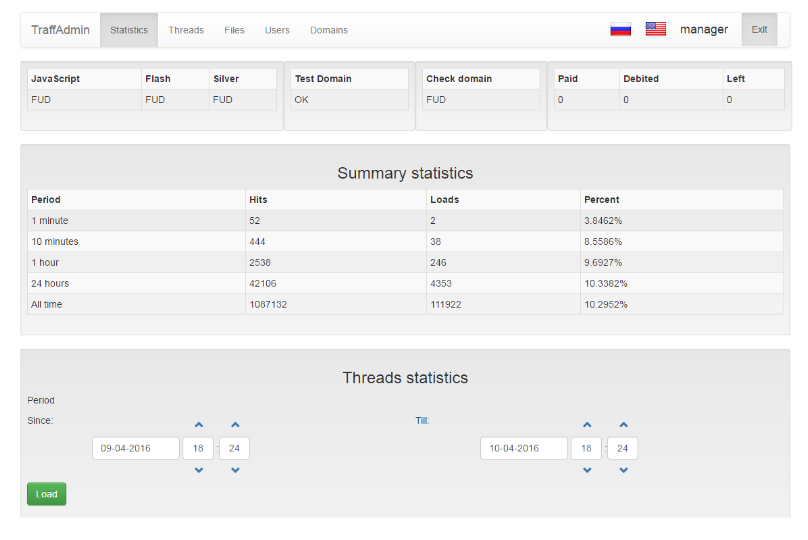
The EK's structure is simple. At the center resides the crook's main server, from where he manages and grants access to his infrastructure for all the other criminals that rent out his service.
Anyone that rents a Nuclear EK from this man gets his own server with an easy to use control panel to view statistics and manage the malware that gets sent to users. Below this level are multiple smaller servers, called "landing pages," servers that host Web pages where users land and get infected with malware.
Read more: Nuclear EK Authors Are Based in Russia, Make $100,000 per Month
Exploit kits are scripts that crooks install on a server that when a user visits a Web page, scans the victim's local PC setup for known software vulnerabilities and delivers an exploit that cracks the user's defenses and automatically installs malware without his knowledge.
Some of the most known exploit kits are Blackhole (now defunct), Angler (the most popular), Magnitude, and Neutrino. Also very popular is the Nuclear EK, which Check Point researchers recently managed to track down and hack into one of its master servers.
Nuclear EK author lives in Krasnodar, Russia
According to researchers, the Nuclear EK is offered as MaaS (Malware-as-a-Service) by a crook living in Krasnodar, Russia. This man is suspected to be the EK's leading developer, but Check Point says that Nuclear is not a one-man job and that others are also almost certainly helping him manage the service.
The EK's structure is simple. At the center resides the crook's main server, from where he manages and grants access to his infrastructure for all the other criminals that rent out his service.
Anyone that rents a Nuclear EK from this man gets his own server with an easy to use control panel to view statistics and manage the malware that gets sent to users. Below this level are multiple smaller servers, called "landing pages," servers that host Web pages where users land and get infected with malware.
Read more: Nuclear EK Authors Are Based in Russia, Make $100,000 per Month
