silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,746
- 123,924
- 8,399
The value of a security vulnerability drops significantly the moment it gets patched but the bad guys will keep exploiting it for as long as they can find victims that are worth the effort.
According to a report today, the most exploited security bugs in the first quarter of 2019 were well-known, old problems, some of them patched almost a decade ago.
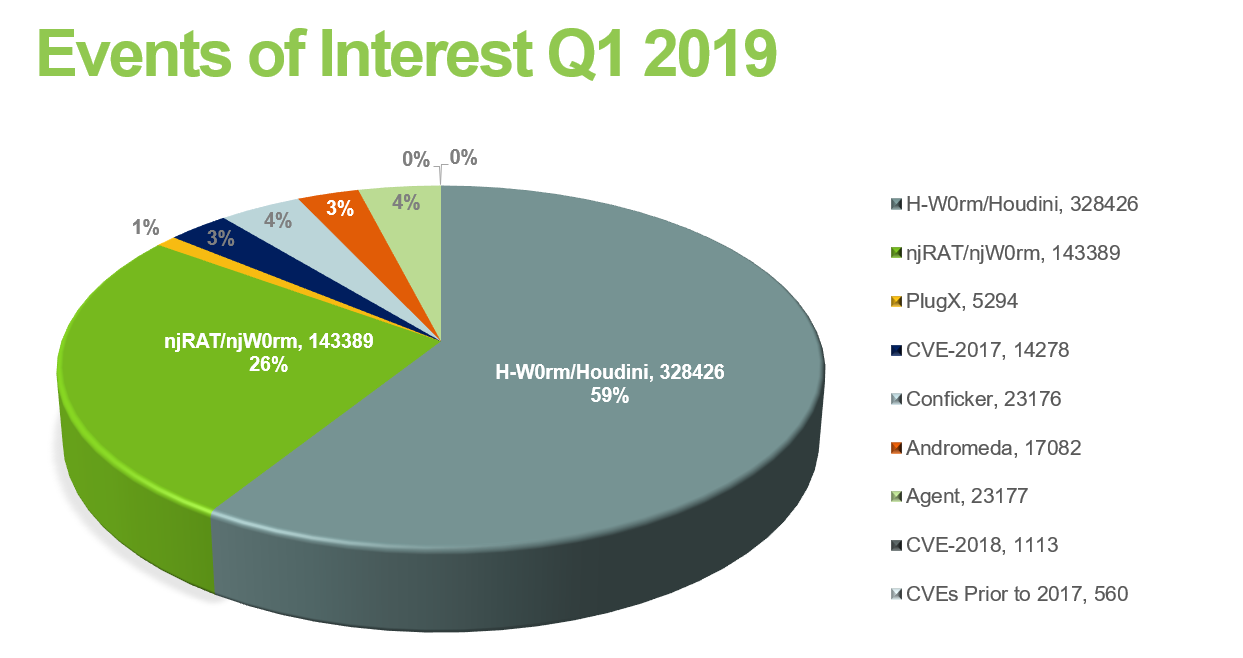
Statistics and research from Fidelis Cybersecurity show that about a third of the alerts recorded by the company were for exploits, vulnerabilities, and malware that emerged in 2017 and earlier.
The malware-generated events that caused most alerts pointed to H-W0rm and njRAT, two remote access tools (RATs) that have been been in use since at least 2012.
njRAT is customizable and there are numerous tutorials explaining how to use it; some go as far back as 2012 and are extremely easy to find. This clarifies why it is so popular.
Fidelis researchers believe that the authors of the two threats may be working together, based on observations from forums on the dark web.
Apart from old tools and kits, the researchers also noticed that 27% of the compromise attempts and alerts were for vulnerabilities from 2017 and earlier. The most prevalent are the following:
- CVE-2017-8570 - "Composite Moniker" remote code execution, exploit code available
- CVE-2017-0143 - affects SMBv1 protocol, exploit released by the ShadowBrokers (Eternal Synergy)
- CVE-2018-11776 - remote code execution in Apache Struts, exploit available
- CVE-2017-11882 - remote code execution in Microsoft Office, exploit available
- CVE-2009-3129 - remote code execution in Microsoft Excel/Word used in operation "Red October" exploit available