- Oct 23, 2012
- 12,527
Operation uses a large collection of tools and techniques
With the holiday season just around the corner, PoS malware detection is at an all-time high, and one of the most well-organized campaigns is Operation Black Atlas.
Named after the infamous BlackPOS malware family responsible for the massive Target data breach, Operation Black Atlas, besides BlackPOS of course, also uses malware such as Alina, NewPOSThings, Gorynich, Diamond Fox, and a version of the Kronos backdoor.
Operation Black Atlas started in September 2015
Trend Micro security threat analysts have first detected this campaign in September and saw it intensify in nature as the holiday season got closer.
For spreading their malicious payloads, Black Atlas operators used a so-called "shotgun" approach. This relies on targeting multiple machines at the same time, with various known exploits and entry points, as opposed to focusing on individual users via social engineering or spear phishing attacks.
The shotgun technique ensures the malware reaches more victims, but also exposes the entire operation to cyber-security vendors and their team of engineers, which is exactly what happened.
"They basically checked available ports on the Internet to see if they can get in, ending up with multiple targets around the world," said Trend Micro's Jay Yaneza, Threats Analyst.
With the holiday season just around the corner, PoS malware detection is at an all-time high, and one of the most well-organized campaigns is Operation Black Atlas.
Named after the infamous BlackPOS malware family responsible for the massive Target data breach, Operation Black Atlas, besides BlackPOS of course, also uses malware such as Alina, NewPOSThings, Gorynich, Diamond Fox, and a version of the Kronos backdoor.
Operation Black Atlas started in September 2015
Trend Micro security threat analysts have first detected this campaign in September and saw it intensify in nature as the holiday season got closer.
For spreading their malicious payloads, Black Atlas operators used a so-called "shotgun" approach. This relies on targeting multiple machines at the same time, with various known exploits and entry points, as opposed to focusing on individual users via social engineering or spear phishing attacks.
The shotgun technique ensures the malware reaches more victims, but also exposes the entire operation to cyber-security vendors and their team of engineers, which is exactly what happened.
"They basically checked available ports on the Internet to see if they can get in, ending up with multiple targets around the world," said Trend Micro's Jay Yaneza, Threats Analyst.
Not all Black Atlas infections yield the desired results
As for infection methods, Black Atlas operators used a broad range of tools, varying from penetration testing frameworks to brute-force attacks to gather intelligence about targets they want to infect, and then crack their way inside machines.
According to Trend Micro, Black Atlas operators managed to steal data like website credentials, Facebook logins, and in an isolated case, the operators even hijacked a live video feed from a closed-circuit CCTV camera, inside a gas station.
Infection of PoS devices occurs in the later stages of the Black Atlas operation, after the botnet's operators are sure they landed on targets that handle financial transactions.
In most cases, users were infected with BlackPOS, downloaded via Gorynych or Diamond Fox, used as payload droppers.
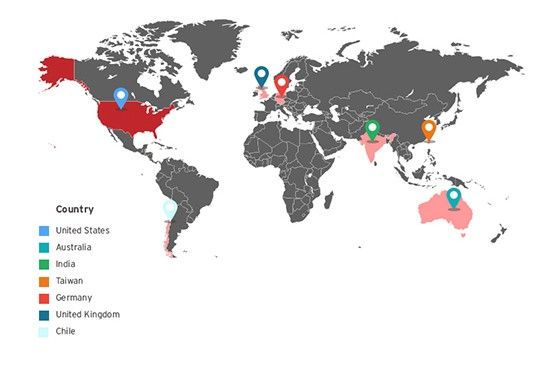
Most machines infected during the Black Atlas campaign are in the US, Australia, India, Taiwan, Germany, the UK, and Chile.