silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,176
A new ransomware strain called Ordinypt is currently targeting victims in Germany, but instead of encrypting users' documents, the ransomware rewrites files with random data.
Discovered on Monday by G Data security researcher Karsten Hahn, the ransomware has been seen targeting only German users (based on VirusTotal detections) via emails written in German, and delivering ransom notes in an error-free German language. This ransomware was originally named by Karsten as HSDFSDCrypt for lack of a better name, but has since been changed to Ordinypt.
Similar to how the original Petya Ransomware was distributed, Ordinypt is also pretending to be resumes being sent in reply to job adverts. These emails contain two files — a JPG image of the woman supposedly sending a resume, and a ZIP file containing the resume and a curriculum vitae.
Discovered on Monday by G Data security researcher Karsten Hahn, the ransomware has been seen targeting only German users (based on VirusTotal detections) via emails written in German, and delivering ransom notes in an error-free German language. This ransomware was originally named by Karsten as HSDFSDCrypt for lack of a better name, but has since been changed to Ordinypt.
Similar to how the original Petya Ransomware was distributed, Ordinypt is also pretending to be resumes being sent in reply to job adverts. These emails contain two files — a JPG image of the woman supposedly sending a resume, and a ZIP file containing the resume and a curriculum vitae.
These attachments are named Viktoria Henschel - Bewerbungsfoto.jpg and Viktoria Henschel - Bewerbungsunterlagen.zip.
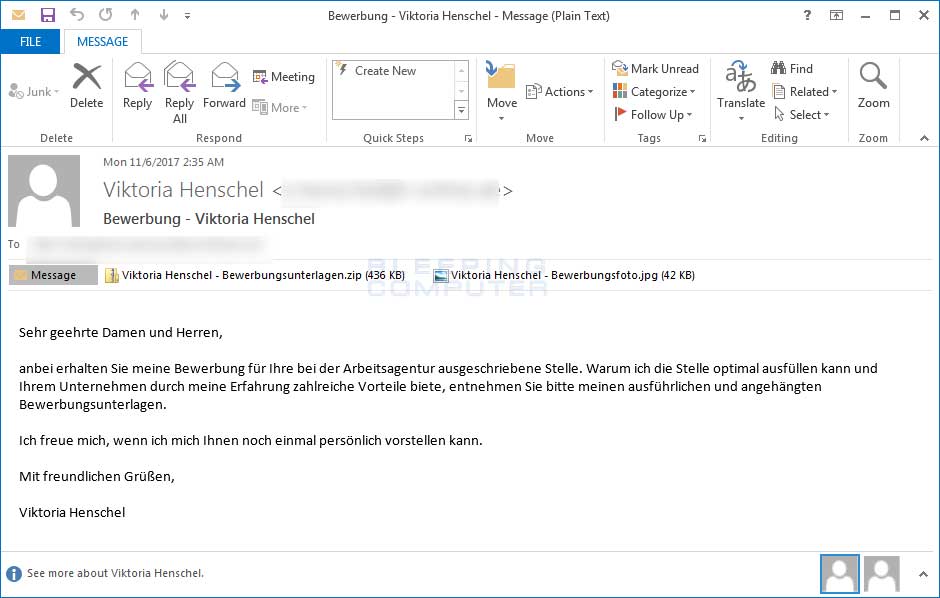
The ZIP archive contains two EXE files that use the old double-extension and custom icon tricks to fool users into thinking they're different files. In this case, PDF files.
On Windows PCs that hide the file extensions by default, the EXE extension will not show up, and users will only see the PDF part, enough to fool users into believing the files are legitimate PDFs, and not an executables.
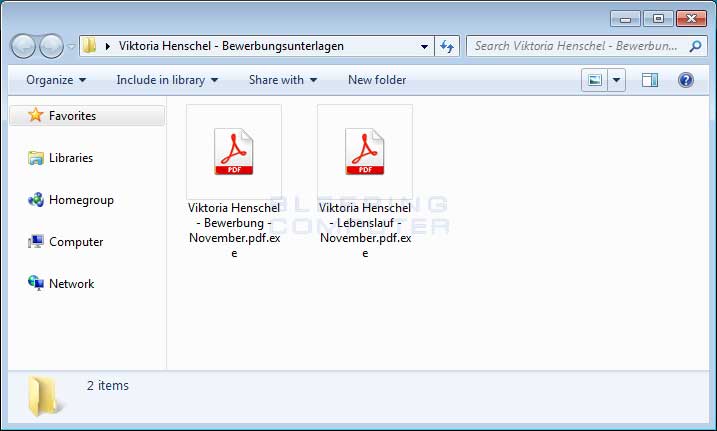
Ordinypt replaces files with random data
Running either executable will launch the Ordinypt ransomware, or better yet, the Ordinypt wiper. Ordinypt is actually a wiper and not ransomware because it does not bother encrypting anything, but just replaces files with random data.
According to reverse engineer Philipp Mackensen, Ordinypt will replace the contents of files with random generated characters consisting of uppercase and lowercase letters and numbers.
File names and content are generated by the same function (only needs a length as input) which randomly generates a string that consists of uppercase, lowercase and numeric characters . File size can differ between 8KB and 24KB (also random). Doesn't encrypt .png files tho.
— Philipp Mackensen (@PMackensen) November 9, 2017
Philipp further told Bleeping Computer that the wiper performs a search for files just like any other ransomware, but just "creates a "pseudo-encrypted-file" which in reality is just a garbage file and deletes the original file afterwards.". Philipp further went on to say that they were most likely doing this to look like a ransomware, while disguising the fact that it is a wiper.
The same algorithm used to generate the random data is also used to generate the new "pseudo-encrypted-file's" name, which is made up of 14 random alpha-numeric characters.
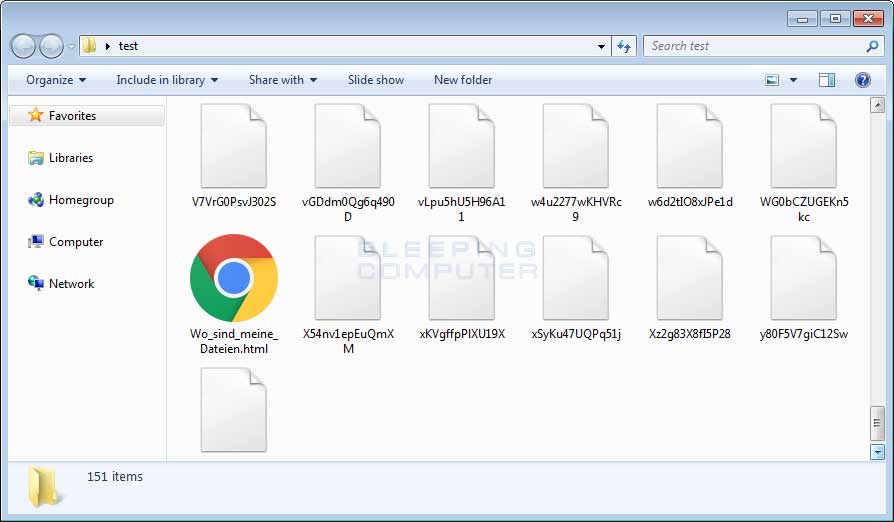
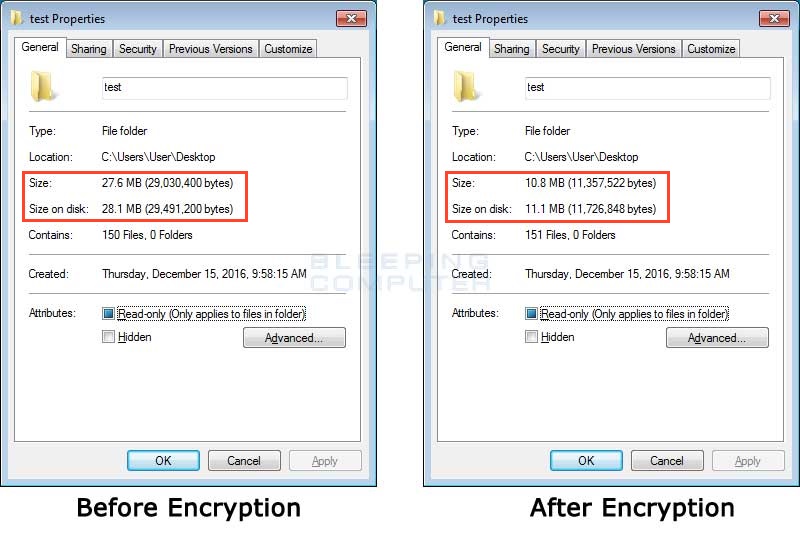
Ordinypt doesn't even bother hiding its destructive nature, as the new files are sometimes more than half the size of the originals.
Ordinypt also drops a ransom note in every folder where it destroys files. The ransom note is named Wo_sind_meine_Dateien.html, which translates to Where_are_my_files.html.
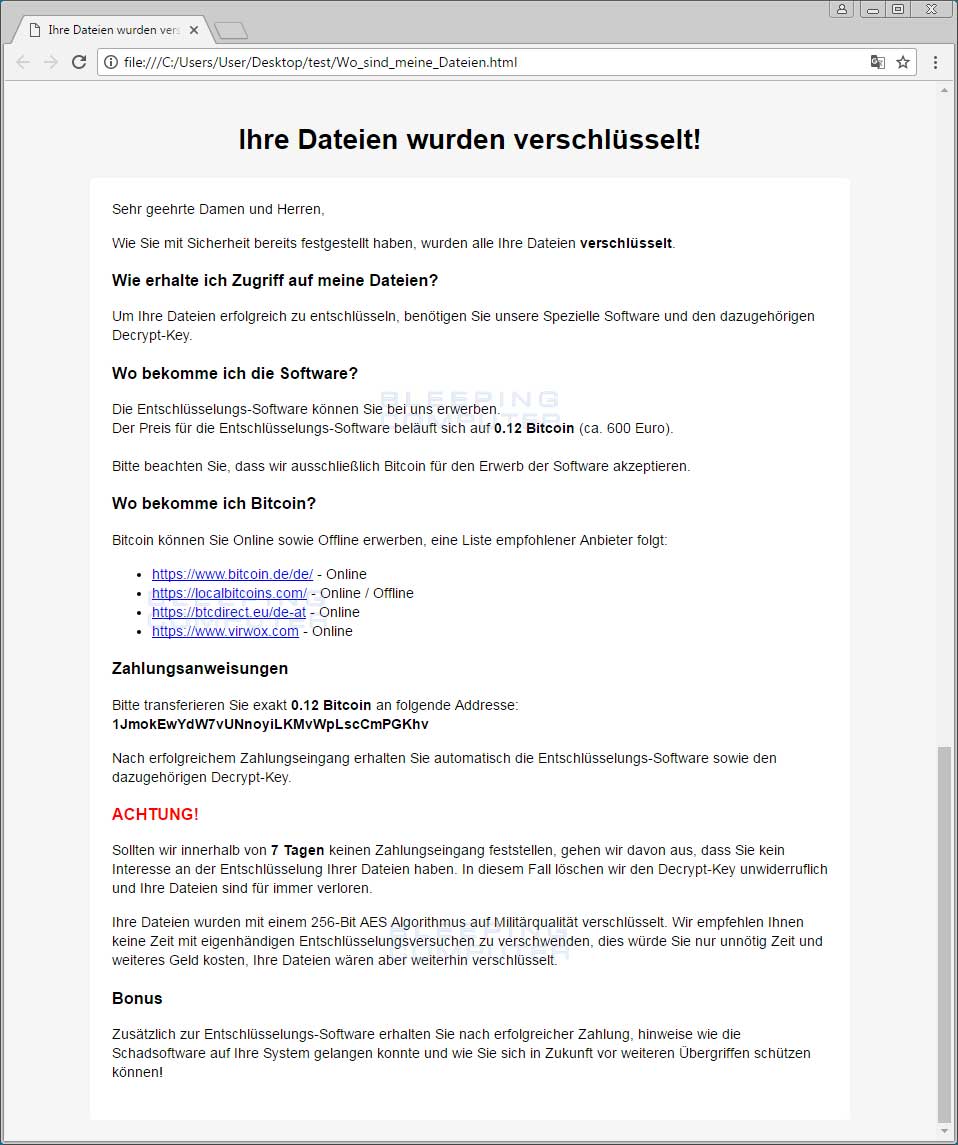
Ordinypt is a wiper disguised as ransomware
The intentional data destruction behavior is evident in the way the ransom note was coded.
Usually, ransomware strains show an infection ID and a Bitcoin address, Dark Web URL, or email address where victims can contact the ransomware's operator and confirm the ransom payment.
Ordinypt does not list an infection ID, nor does it ask for a file from where the ransomware's authors can extract such an ID.
Instead, Ordinypt's ransom note uses a JavaScript function to select a random Bitcoin address from a list of 101 hardcoded wallet addresses.
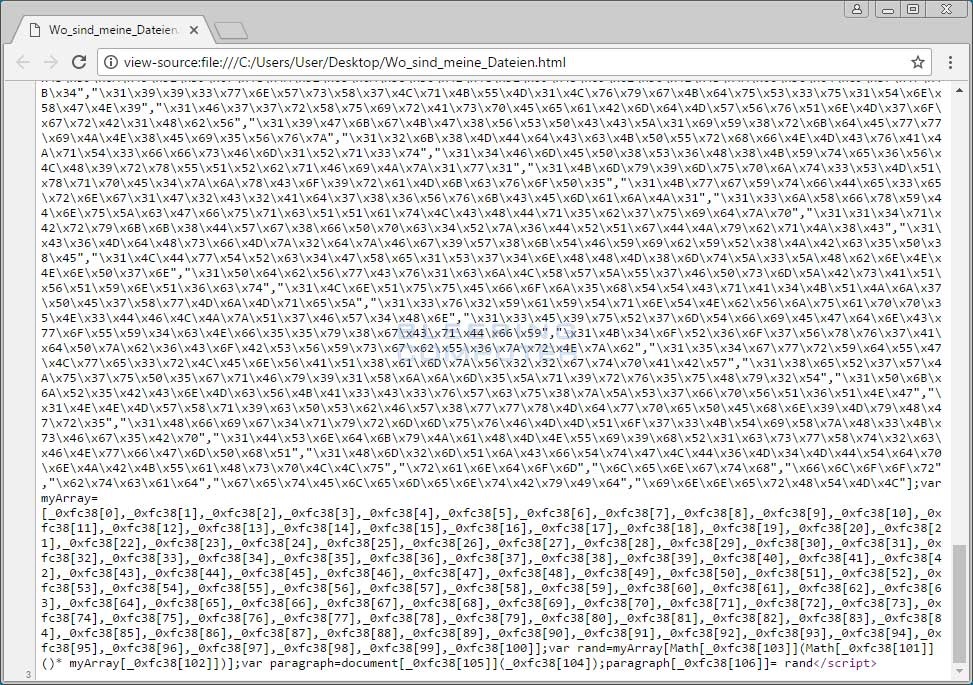
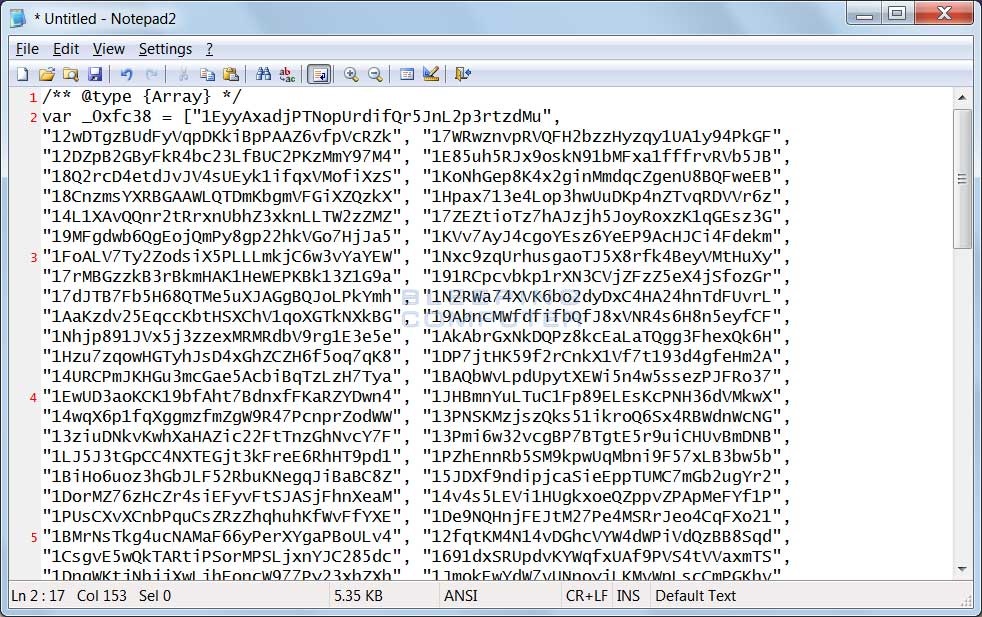
Furthermore, there's no way of contacting the faux ransomware's authors and verifying the payment. All evidence points to the fact that someone coded Ordinypt with the intention to damage computers.
The targeting of HR departments via job application emails also speaks volumes about this being an intentional campaign to damage the operations of some Germany-based companies.
Ordinypt is not the first wiper disguised as ransomware. The most famous case is NotPetya, the faux ransomware that hit the Ukraine in late June, but quickly spread to companies all over the world.
