- Oct 23, 2012
- 12,527
A scan of Cisco networking devices from around the world has revealed that hundreds of thousands of devices are vulnerable to an unpatched security issue that allows attackers to retrieve data from the equipment's memory.
Cisco has recently acknowledged that a cyber-offensive toolkit leaked online by a group of unknown hackers is also affecting its current device models after initial analysis said that only older (discontinued) PIX firewalls were affected.
The tool, named BENINGCERTAIN, leaked in August when a group calling themselves The Shadow Brokers put it online along with tens of other hacking utilities they claim to have stolen from the server of a cyber-espionage entity named the Equation Group, which some security vendors said to be the NSA.
BENINGCERTAIN could extract VPN keys from Cisco devices
Initial analysis by Mustafa Al-Bassam, aka tFlow, co-founder of the LulzSec hacking crew, showed how someone could use BENINGCERTAIN to extract VPN keys from Cisco PIX firewalls.
Last week, a month after BENINGCERTAIN was leaked, Cisco announced that the tool was also effective against current devices running IOS, IOS XE, and IOS XR software.
At the time of writing, there still is no patch available against BENINGCERTAIN (or Pix Pocket) exploitation.
Cisco has recently acknowledged that a cyber-offensive toolkit leaked online by a group of unknown hackers is also affecting its current device models after initial analysis said that only older (discontinued) PIX firewalls were affected.
The tool, named BENINGCERTAIN, leaked in August when a group calling themselves The Shadow Brokers put it online along with tens of other hacking utilities they claim to have stolen from the server of a cyber-espionage entity named the Equation Group, which some security vendors said to be the NSA.
BENINGCERTAIN could extract VPN keys from Cisco devices
Initial analysis by Mustafa Al-Bassam, aka tFlow, co-founder of the LulzSec hacking crew, showed how someone could use BENINGCERTAIN to extract VPN keys from Cisco PIX firewalls.
Last week, a month after BENINGCERTAIN was leaked, Cisco announced that the tool was also effective against current devices running IOS, IOS XE, and IOS XR software.
At the time of writing, there still is no patch available against BENINGCERTAIN (or Pix Pocket) exploitation.
Researchers used IKE packets to discover vulnerable devices
At the technical level, the exploit (CVE-2016-6415) employs a vulnerability in how the firmware of certain Cisco firewalls deals with IKEv1 and IKEv2 (Internet Key Exchange) packets.
The Shadowserver Foundation, with the help of Cisco engineers, has conducted a scan of the entire Internet for Cisco devices vulnerable to this exploit.
"We are querying all computers with routable IPv4 addresses that are not firewalled from the internet with a specifically crafted 64 byte ISAKMP packet and capturing the response," the company explained.
Over 850,000 devices currently exposed online
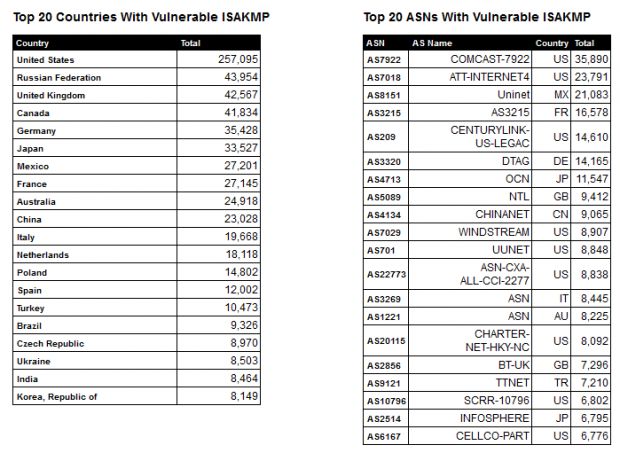
The scan is carried out at regular intervals, and according to the Shadowserver Foundation, on September 25, 2016, at 00:12 GMT, there were 850,803 vulnerable Cisco devices online.
Over 250,000 of these devices are found in the US, followed by the Russian Federation, the UK, Canada, and Germany.
The large number of devices, along with publicly available exploit code makes them easy-pickings for any threat actor that wants to compromise enterprise networks.
Cisco has previously advised network admins to protect affected equipment by placing them behind firewalls.