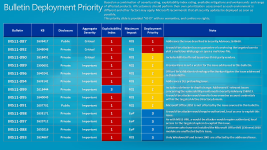
In December Microsoft released 13 security bulletins, (three of which are rated Critical in severity, and 10 Important) fixing 19 unique vulnerabilities in Microsoft products. As usual, Windows users are advised to apply the updates as soon as possible.
[attachment=968]
MS11-087 - Critical: Vulnerability in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2639417): This finally fixes the Vulnerability in TrueType Font Parsing used by the DUQU worm.
MS11-092 - Critical: Vulnerability in Windows Media Could Allow Remote Code Execution (2648048). This security update resolves a privately reported vulnerability in Windows Media Player and Windows Media Center. The vulnerability could allow remote code execution if a user opens a specially crafted Microsoft Digital Video Recording (.dvr-ms) file.
Another notable fixed vulnerability is addressed in Microsoft Security Bulletin MS11-099 - Important: Cumulative Security Update for Internet Explorer (2618444). This security update resolves three privately reported vulnerabilities in Internet Explorer. The most severe vulnerability could allow remote code execution if a user opens a legitimate HyperText Markup Language (HTML) file that is located in the same directory as a specially crafted dynamic link library (DLL) file. It affects all versions of Internet Explorer (6,7,8,9) and has an exploit-ability index of 3.
Source: The December bulletins are released [blogs.technet.com]
[attachment=968]
MS11-087 - Critical: Vulnerability in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2639417): This finally fixes the Vulnerability in TrueType Font Parsing used by the DUQU worm.
MS11-092 - Critical: Vulnerability in Windows Media Could Allow Remote Code Execution (2648048). This security update resolves a privately reported vulnerability in Windows Media Player and Windows Media Center. The vulnerability could allow remote code execution if a user opens a specially crafted Microsoft Digital Video Recording (.dvr-ms) file.
Another notable fixed vulnerability is addressed in Microsoft Security Bulletin MS11-099 - Important: Cumulative Security Update for Internet Explorer (2618444). This security update resolves three privately reported vulnerabilities in Internet Explorer. The most severe vulnerability could allow remote code execution if a user opens a legitimate HyperText Markup Language (HTML) file that is located in the same directory as a specially crafted dynamic link library (DLL) file. It affects all versions of Internet Explorer (6,7,8,9) and has an exploit-ability index of 3.
Source: The December bulletins are released [blogs.technet.com]