Last July, our colleagues at Doctor Web detected a Trojan backdoor on Google Play. Such discoveries are not exactly an everyday occurrence, but they’re hardly unheard of — researchers do find Trojans on Google Play, sometimes hundreds at a time.
This Trojan, however, was surprisingly sophisticated for malware found on Google Play, so our experts decided to dig deeper. They conducted their own investigation and found that the malware is part of a malicious campaign (which we dubbed PhantomLance) that’s been ongoing since the end of 2015.
What PhantomLance can do
Our experts detected several versions of PhantomLance. Despite their increasing complexity and the differences in time of appearance , they are fairly similar in terms of capabilities.
The main objective of PhantomLance is to harvest confidential information from the victim’s device. The malware is able to supply its handlers with location data, call logs, text messages, lists of installed apps, and full information about the infected smartphone. What’s more, its functionality can be expanded at any moment simply by loading additional modules from the C&C server.
PhantomLance distribution
Google Play is the malware’s main distribution platform. It’s also been found in third-party repositories, but for the most part they are only mirrors of the official Google app store.
We can say for sure that apps infected with a version of the Trojan started appearing in the store in the summer of 2018. The malware was found hiding in utilities for changing fonts, removing ads, system cleanup, and so on.

An app on Google Play found to contain the PhantomLance backdoor
Apps containing PhantomLance have all since been removed from Google Play, of course, but copies can still be found in mirrors. Ironically, some of these mirror repositories state that the installation package was downloaded directly from Google Play, and is thus said to be definitely virus-free.
How did the cybercriminals manage to sneak their toy into Google’s official store? First, for added authenticity, the attackers created a profile of each developer on GitHub. These profiles contained only some sort of license agreement. Nevertheless, having a profile on GitHub apparently lends developers respectability.
Second, the apps that PhantomLance’s creators initially uploaded to the store were not malicious. The first versions of the programs did not contain any suspicious features, and therefore they passed Google Play’s checks with flying colors. Only some time later, with updates, did the apps acquire malicious features.
PhantomLance’s targets
Judging by the geography of its spread, as well as the presence of Vietnamese versions of malicious apps in online stores, we believe the top targets of PhantomLance creators were users from Vietnam.
Moreover, our experts detected a number of characteristics linking PhantomLance with the OceanLotus group, which is responsible for creating a range of malware also aimed at users from Vietnam.
The set of OceanLotus malware tools previously analyzed includes a family of macOS backdoors, a family of Windows backdoors, and a set of Android Trojans, whose activity was spotted in 2014–2017. Our experts came to the conclusion that PhantomLance succeeded the abovementioned Android Trojans starting in 2016.
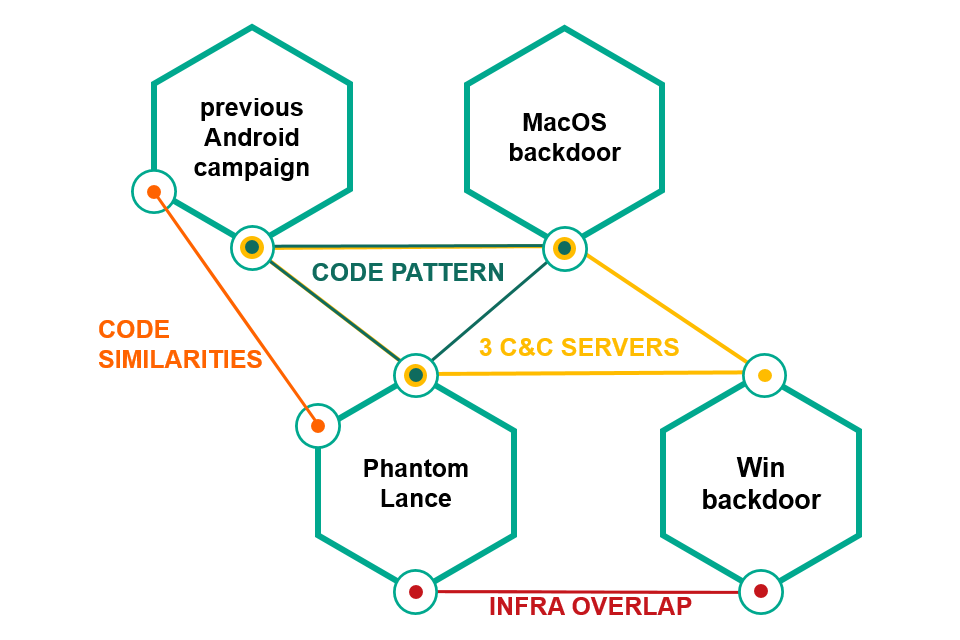
PhantomLance is linked to other OceanLotus malware weapons
How to guard against PhantomLance
One of the tips we often repeat in posts about Android malware is “Install apps only from Google Play.” But PhantomLance demonstrates yet again that malware can sometimes hoodwink even the Internet giants.
Google takes great pains to keep its app store clean (otherwise we’d run into suspicious software far more often), but the company’s capabilities are not unlimited, and attackers are inventive. Therefore, the mere fact that an app is on Google Play is no guarantee of its safety. Always consider other factors:
For more technical information about PhantomLance, see our experts’ detailed report on Securelist.
Source
This Trojan, however, was surprisingly sophisticated for malware found on Google Play, so our experts decided to dig deeper. They conducted their own investigation and found that the malware is part of a malicious campaign (which we dubbed PhantomLance) that’s been ongoing since the end of 2015.
What PhantomLance can do
Our experts detected several versions of PhantomLance. Despite their increasing complexity and the differences in time of appearance , they are fairly similar in terms of capabilities.
The main objective of PhantomLance is to harvest confidential information from the victim’s device. The malware is able to supply its handlers with location data, call logs, text messages, lists of installed apps, and full information about the infected smartphone. What’s more, its functionality can be expanded at any moment simply by loading additional modules from the C&C server.
PhantomLance distribution
Google Play is the malware’s main distribution platform. It’s also been found in third-party repositories, but for the most part they are only mirrors of the official Google app store.
We can say for sure that apps infected with a version of the Trojan started appearing in the store in the summer of 2018. The malware was found hiding in utilities for changing fonts, removing ads, system cleanup, and so on.

An app on Google Play found to contain the PhantomLance backdoor
Apps containing PhantomLance have all since been removed from Google Play, of course, but copies can still be found in mirrors. Ironically, some of these mirror repositories state that the installation package was downloaded directly from Google Play, and is thus said to be definitely virus-free.
How did the cybercriminals manage to sneak their toy into Google’s official store? First, for added authenticity, the attackers created a profile of each developer on GitHub. These profiles contained only some sort of license agreement. Nevertheless, having a profile on GitHub apparently lends developers respectability.
Second, the apps that PhantomLance’s creators initially uploaded to the store were not malicious. The first versions of the programs did not contain any suspicious features, and therefore they passed Google Play’s checks with flying colors. Only some time later, with updates, did the apps acquire malicious features.
PhantomLance’s targets
Judging by the geography of its spread, as well as the presence of Vietnamese versions of malicious apps in online stores, we believe the top targets of PhantomLance creators were users from Vietnam.
Moreover, our experts detected a number of characteristics linking PhantomLance with the OceanLotus group, which is responsible for creating a range of malware also aimed at users from Vietnam.
The set of OceanLotus malware tools previously analyzed includes a family of macOS backdoors, a family of Windows backdoors, and a set of Android Trojans, whose activity was spotted in 2014–2017. Our experts came to the conclusion that PhantomLance succeeded the abovementioned Android Trojans starting in 2016.

PhantomLance is linked to other OceanLotus malware weapons
How to guard against PhantomLance
One of the tips we often repeat in posts about Android malware is “Install apps only from Google Play.” But PhantomLance demonstrates yet again that malware can sometimes hoodwink even the Internet giants.
Google takes great pains to keep its app store clean (otherwise we’d run into suspicious software far more often), but the company’s capabilities are not unlimited, and attackers are inventive. Therefore, the mere fact that an app is on Google Play is no guarantee of its safety. Always consider other factors:
- Give preference to apps from trusted developers.
- Pay attention to app ratings and user reviews.
- Look carefully at the permissions an app requests, and don’t hesitate to refuse if you think it’s being greedy. For example, a weather app probably doesn’t need access to your contacts and messages, and likewise a photo filter doesn’t need to know your location.
- Scan the apps you install on your Android device with a reliable security solution.
For more technical information about PhantomLance, see our experts’ detailed report on Securelist.
Source