A
Alkajak
Thread author
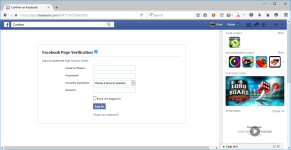
Crooks are using a new phishing scheme to trick users into handing over their Facebook credentials, and this time around, they're taking advantage of Facebook's own website to carry out their attacks.
The crooks are utilizing Facebook's Apps platform to host malicious content inside the Facebook site itself. The attackers are registering Facebook apps, and they're using the platform's free range powers to load malicious Web pages via iframes.
The iframes load content from the crooks' server, which is displayed inside the Facebook app, shown on the Facebook website.
Even low-end skilled attackers can fool users with this trick
Crooks who want to carry out phishing attacks and steal Facebook credentials only need some CSS skills in order to craft a login form that uses Facebook's default UI style.
Users who land on these pages through various email or social spam campaigns would have a hard time detecting this as a malicious page.
All other Facebook elements are there, all fully functional. The Facebook menu works, the notifications show actual Facebook notifications, and the page's URL is a Facebook address.
The only difference is the malicious iframe in the middle of the page, loaded via the Facebook Apps platform from the crook's server. For this particular campaign spotted by security firm Netcraft, this iframe was loaded from a malicious website hosted on HostGator.
A second-stage trick drives the phish home
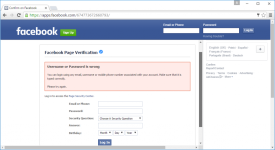
In case some more astute users suspected anything, a particularity for this campaign made sure to fool even those who had gone through anti-phishing training, which tells users to enter the wrong login credentials in suspicious login forms.
Users who enter the incorrect login details and get a success message will surely be convinced the login form is fake, and somebody is trying to dupe them.
As a particularity of the campaign spotted by Netcraft, the login form always showed a login error every time the user tried to authenticate, even if they entered to correct or the wrong credentials.
By using this trick, some low-end CSS skills, social engineering, and the Facebook Apps platform, crooks can run highly efficient phishing campaigns right from an official Facebook URL.
To stay safe, users should be very wary of entering their Facebook login credentials inside Facebook apps (hosted on apps.facebook.com domains). Facebook automatically authenticates all users inside these apps, and everyone should always use thefacebook.com/login URL to authenticate on the site, and nowhere else.
