Talos has observed several malware campaigns attempting to spread Remcos to various victims. Since Remcos is advertised and sold on numerous hacking-related forums, we believe it is likely that multiple unrelated actors are leveraging this malware in their attacks using a variety of different methods to infect systems. Earlier this year, RiskIQ published a
report regarding an attacker who was reportedly targeting defense contractors in Turkey. Since then, this threat actor has continued to operate and has been observed targeting specific types of organizations. Talos has confirmed that in addition to defense contractors, this attacker has also targeted other organizations such as:
- International news agencies;
- Diesel equipment manufacturers and service providers operating within the maritime and energy sector; and
- HVAC service providers operating within the energy sector.
In all of the observed campaigns, the attack begins with specially crafted spear phishing emails written in Turkish. The emails appear as if they were sent from a Turkish government agency and purport to be related to tax reporting for the victim's organization. The attacker put effort into making the emails look as if they were official communications from Gelir İdaresi Başkanlığı (GIB), the Turkish Revenue Administration, which operates under the Ministry of Finance and is responsible for handling taxation functions in Turkey. The attacker even went as far to include official GIB graphics and the text at the bottom which translates to:
"Thank you for your participation in the e-mail notification system of [the] Department of Revenue Administration's e-mail service. This message has been sent to you by GIB Mail Notification System. Please do not reply to this message."
As is common with many spear phishing campaigns, malicious Microsoft Office documents are attached to the emails. While the majority of these documents have been Excel spreadsheets, we have also observed the same attacker leveraging Word documents. In many cases, the contents of the document have been intentionally blurred as way to entice victims to enable macros and view the content.
Remcos is a robust RAT that can be used to monitor keystrokes, take remote screen captures, manage files, execute commands on infected systems and more. In several cases, the distribution servers associated with these campaigns have been observed hosting several other malicious binaries in addition to Remcos. As previously mentioned, a company called Breaking Security has been offering Remcos and other questionable software for purchase on their website. There are no details about the company or the people behind it listed on its website. The website does, however, list a value-added tax (VAT) number (DE308884780) which shows the company is registered in Germany. Interestingly, you can look up the name and address of companies in almost any European Union (EU) country except Germany on this
website. Germany does not share this information due to privacy concerns. Because Breaking Security was registered in Germany, we were unable to identify the name and address of the individual behind this company. Nevertheless, we were able to identify several artifacts that give us an idea as to who might be behind the company.
As the release notes show, it is actively maintained. The authors release new versions on almost a monthly basis:
v2.0.5 – July 14, 2018
v2.0.4 – April 6, 2018
v2.0.3 – March 29, 2018
v2.0.1 – Feb. 10, 2018
v2.0.0 – Feb. 2, 2018
v1.9.9 – Dec. 17, 2017
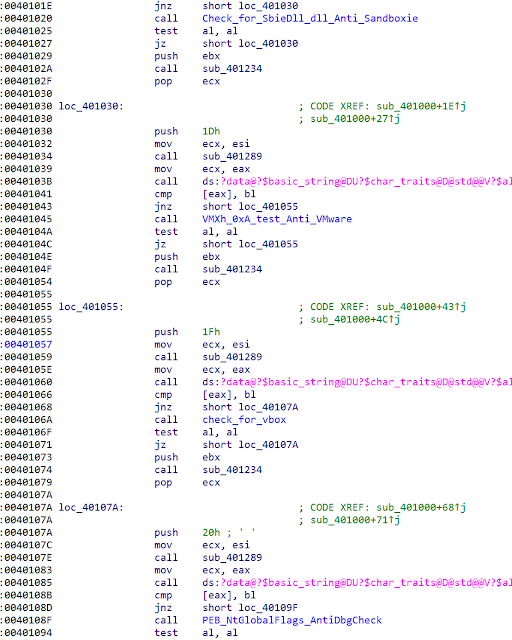
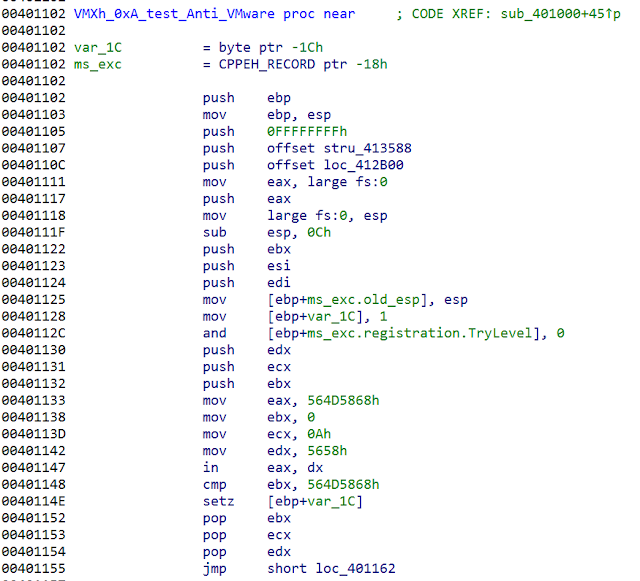
Remcos has the functionalities that are typical of a RAT. It is capable of hiding in the system and using malware techniques that make it difficult for the typical user to detect the existence of Remcos. Several routines are looking like they were just copied and (best case) slightly modified from publicly available sources. A good example is the anti-analysis section:
It is checking for an outdated artifact, the 'SbieDll.dll'. In our opinion, there are not many analysts using Sandboxie these days anymore. A closer look at the other functions is also showing a high code similarity to publicly available projects. Below you can see the Remcos VMware detection code: