Security researchers have discovered a new Android trojan that uses the DroidPlugin framework to split malicious behavior across multiple plugins, making detection much harder.
Nicknamed PluginPhantom by Palo Alto Networks security researchers, this newly discovered trojan employs a novel technique not seen in other Android malware families until now.
Trojan abuses DroidPlugin framework
The trojan abuses DroidPlugin, which is a virtualization framework for Android apps. DroidPlugin allows Android developers to create apps that can load plugins from local or remote files in real-time, without users needing to "approve" the loading (installation) process.
While used for nefarious actions by the PluginPhantom malware, the DroidPlugin framework is normally used for legitimate purposes as keeping an app's size down, enabling multi-account support for social media apps, and for hot-patching (real-time updates that don't go through the Google Play Store).
The way PluginPhantom uses DroidPlugin is by splitting the trojan into a host app that when analyzed, doesn't feature any malicious behavior except the ability to load plugins.
The malicious behavior is contained in these plugins, which are simple APK files stored inside the host app's resources. The DroidPlugin framework allows the host app to load these APK files without the user's approval.
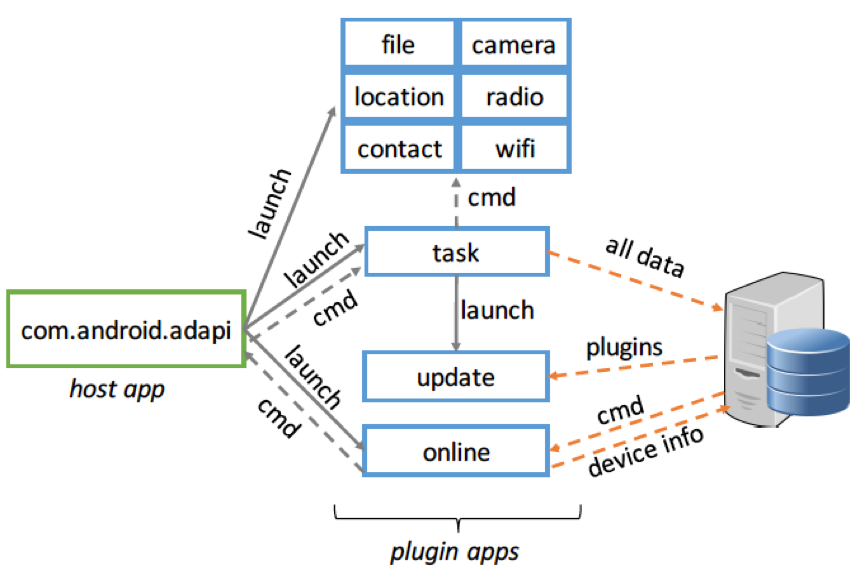
PluginPhatom architecture (Source: Palo Alto Networks)
Currently, the PluginPhatom malware includes nine plugins, three for basic operations and six for malicious actions.
Read more about the plugins: PluginPhantom Android Malware Uses Novel Approach to Hide Malicious Behavior
Nicknamed PluginPhantom by Palo Alto Networks security researchers, this newly discovered trojan employs a novel technique not seen in other Android malware families until now.
Trojan abuses DroidPlugin framework
The trojan abuses DroidPlugin, which is a virtualization framework for Android apps. DroidPlugin allows Android developers to create apps that can load plugins from local or remote files in real-time, without users needing to "approve" the loading (installation) process.
While used for nefarious actions by the PluginPhantom malware, the DroidPlugin framework is normally used for legitimate purposes as keeping an app's size down, enabling multi-account support for social media apps, and for hot-patching (real-time updates that don't go through the Google Play Store).
The way PluginPhantom uses DroidPlugin is by splitting the trojan into a host app that when analyzed, doesn't feature any malicious behavior except the ability to load plugins.
The malicious behavior is contained in these plugins, which are simple APK files stored inside the host app's resources. The DroidPlugin framework allows the host app to load these APK files without the user's approval.

PluginPhatom architecture (Source: Palo Alto Networks)
Currently, the PluginPhatom malware includes nine plugins, three for basic operations and six for malicious actions.
Read more about the plugins: PluginPhantom Android Malware Uses Novel Approach to Hide Malicious Behavior